
Microsoft is now using a Windows driver to prevent users from changing the configured Windows 10 and Windows 11 default browser through software or by manually modifying the Registry.
Windows users can still change their default browser through the Windows settings. However, those who utilized software to make the changes are now blocked by a driver quietly introduced to users worldwide as part of the February updates for Windows 10 (KB5034763) and Windows 11 (KB5034765).
IT consultant Christoph Kolbicz was the first to notice the change when his programs, SetUserFTA and SetDefaultBrowser, suddenly stopped working.
SetUserFTA is a command line program that lets Windows admins change file associations through login scripts and other methods. SetDefaultBrowser works similarly but is only for changing the default browser in Windows.
Starting with Windows 8, Microsoft introduced a new system for associating file extensions and URL protocols with default programs to prevent them from being tampered with by malware and malicious scripts.
This new system associates a file extension or URL protocol to a specially crafted hash stored under the UserChoice Registry keys.
For example, the default web browser assigned to the HTTPS URL protocol is found under:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Associations\UrlAssociations\https\UserChoice]
"ProgId"="ChromeHTML"
"Hash"="N3eikAB1HhI="
If the correct hash is not used, Windows will ignore the Registry values and use the default program for this URL protocol, which is Microsoft Edge.
Kolbicz reverse engineered this hashing algorithm to create the SetUserFTA and SetDefaultBrowser programs to change default programs.
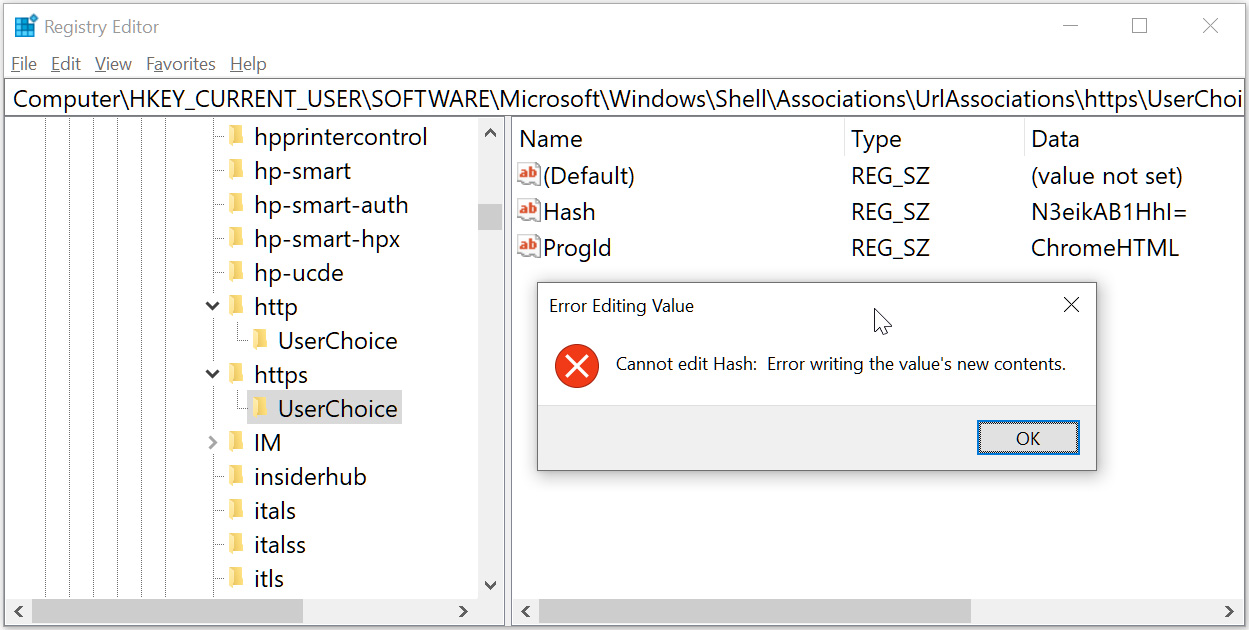
However, with the Windows 10 and Windows 11 February updates installed, Kolbicz noted that these Registry keys have now been locked down, giving errors when modified outside the Windows Settings.
For example, using the Windows Registry Editor to modify these settings gives an error stating, "Cannot edit Hash: Error writing the value's new contents."
Source: BleepingComputer
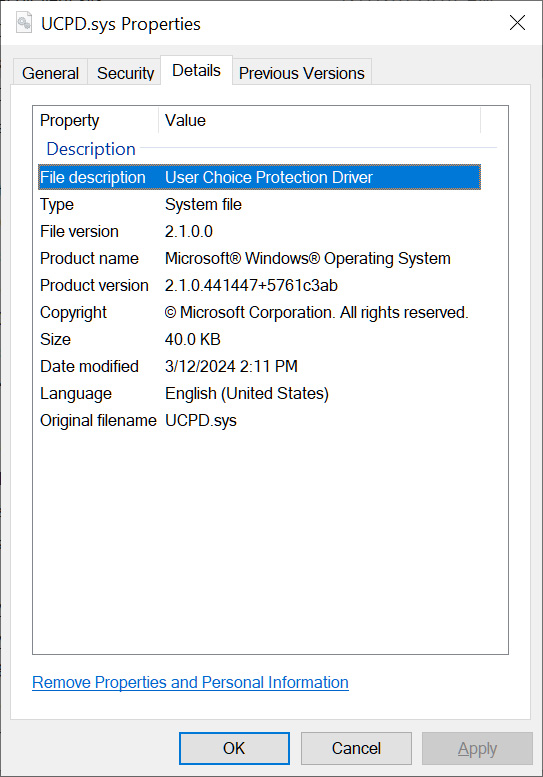
After further research, Kolbicz discovered that Microsoft introduced a new Windows filter driver (c:\windows\system32\drivers\UCPD.sys) as part of the February updates.
Source: BleepingComputer
This driver is described as a "User Choice Protection Driver," and when loaded, prevents direct editing of the Registry keys associated with the HTTP and HTTPS URL associations and the .PDF file association.
The associated Registry keys are:
HKCU\Software\Microsoft\Windows\Shell\Associations\UrlAssociations\http\UserChoice
HKCU\Software\Microsoft\Windows\Shell\Associations\UrlAssociations\https\UserChoice
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\UserChoice
It should be noted that in BleepingComputer's tests, the driver was rolled out to our Windows 11 and Windows 10 devices, but it only locked down the Registry keys on our Windows 10 devices.
In a blog post, Kolbicz explains that while you cannot unload the driver, you can disable it in the Registry.
"We cannot simply unload this driver, BUT we can of course disable it! this can be done by this one-liner – in an elevated PowerShell followed by a reboot.
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\UCPD” -Name “Start” -Value 4 -PropertyType DWORD -Force
This brings back the functionality of SetUserFTA, but sadly requires administrative permissions and a reboot."
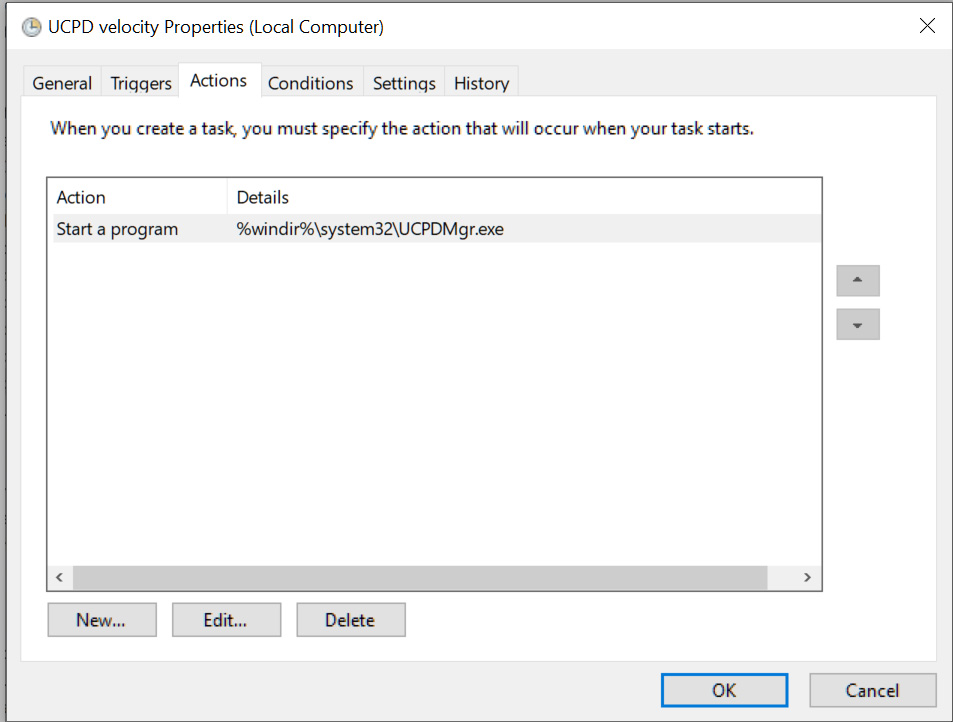
❖ Christoph KolbiczHowever, a blog post by Gunnar Haslinger explains that a newly created 'UCPD velocity' scheduled task under \Microsoft\Windows\AppxDeploymentClient will automatically enable the service again if disabled.
Source: BleepingComputer
Due to this, the only way to disable the driver is to turn it off via the Registry and delete/disable the Scheduled Task.
Possibly related to DMA compliance
Kolbicz believes this change may be to comply with Europe's Digital Markets Act (DMA), which aims to ensure fair competition and the prevention of anti-competitive practices by six large companies, known as "gatekeepers."
These designated gatekeepers are Alphabet, Amazon, Apple, ByteDance, Meta, and Microsoft, who had until March to comply with the new regulations.
In November 2023, Microsoft outlined changes coming to Windows in March 2024 to comply with the new DMA regulations.
These changes included new default browser policies for users in the European Economic Area (EEA) that force Windows to use users' default browser when opening a link rather than using Microsoft Edge.
"In the EEA, Windows will always use customers' configured app default settings for link and file types, including industry standard browser link types (http, https)," explained Microsoft.
"Apps choose how to open content on Windows, and some Microsoft apps will choose to open web content in Microsoft Edge."
However, this new driver has also rolled out to Windows 10 and Windows 11 devices in the USA that do not have to comply with the DMA act, shedding doubt on this theory.
Furthermore, even when the Registry settings are locked down and the device's default browser is Google Chrome, Windows still opened operating system links in Microsoft Edge in our tests.
In 2021, Mozilla also reverse engineered the Windows default browser hashing to make it easier for users to configure Firefox as the default browser.
Some have speculated that this change was introduced to block competing browsers from configuring itself as the default browser outside of the Windows Settings. Others said it could have been added as a security feature to prevent malware from making itself the default browser.
BleepingComputer contacted Microsoft about the lockdown of these Registry keys in March, but they said they had nothing to share at this time.
Update 4/7/24: Clarified to explain that manually meant manually through registry modifications and reiterated that you can still change the default browser via the Windows settings. Added further information on locked down browsers being ignored for operating system links in our US-based tests.


Comments
mikebutash - 2 weeks ago
Sounds like just yet another excuse to reset everyone's browser to Edge in some coy attempt at switching people back to their spyware engine to complete the trifecta of parsing everything you do or look at natively. Opps, we did it again, sorry-not-sorry!
gunnarh - 2 weeks ago
Nice Writeup of the excellent Blog-Post of Chistoph Kolbicz. Thanks for citing me as person and and my Blog-Post https://hitco.at/blog/windows-userchoice-protection-driver-ucpd/
Jimmymm - 2 weeks ago
Let's just hope this service prevents Windows from switching our default apps back to malware infested Microsoft versions.
chadness - 2 weeks ago
This explains why my way of associating programs via registry for my end users quit working recently. Seems like the best way to do this now is via DISM. https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/export-or-import-default-application-associations?view=windows-11
JimmyKwagzog - 2 weeks ago
Would be quite the turn of events if it was supposedly implemented to comply with the DMA and respect users' default app choices, since it effectively does exactly the opposite for any user in a non-persistent VDI environment. It broke VMware's DEM product and hijacks the https, http, and pdf file extensions back to Edge even if the user manually sets them in Settings, since it prevents DEM from caching the changes at logoff.
Thank you for the possible workaround though! Will be interesting to see if it works when applied to the parent images on our pools.
RaunchyButts - 2 weeks ago
But the DOJ goes after Apple for green message bubbles.
Pathetic.
Chris Cosgrove - 2 weeks ago
@ RaunchytButts
And the relevance of your comment to this article is ? Non-existant ?
jeffaaron - 2 weeks ago
It's relevant because the DOJ goes after Apple for something that Apple users actually want. Yet, Microsoft is consistently anti-competitive. The world basically sued Microsoft in the 90s because of how anti-competitive they were about Internet Explorer. What they are doing now with Edge is so far beyond what they ever did with IE.
TonyNes - 2 weeks ago
Another tactic by Microsoft to be in control. No problem. Some Geek will have an article on "how to modify the registry."
b1k3rdude - 2 weeks ago
Well micro$haft can do what they like, as I always force remove edge via the cmd line. So there is nothing to default to other than the currently set default browser, which in this case is firefox.
Sgtkeebler - 2 weeks ago
Honestly, if Microsoft didn't fill their browser with useless garbage, I would probably use it a lot more. Microsoft, I do not care nor want the side bar filled with games, and advertisements, I do not want Ai, I do not want pop-ups in my browser every time I open it letting me know about more worthless features. Stop loading your browser with garbage and maybe people would use it more.
ThomasMann - 2 weeks ago
"...Some have speculated that this change was introduced to block competing browsers from configuring itself as the default browser outside of the Windows Settings. ..."
NO !!! M$ would never do anything like that. Even worse is, that they are so stupid to believe that no one wil lnotice it and find out.
God... please do us poo rhumans a favor, and let those Linux people finally come up with one REALLY usable OS....
DyingCrow - 2 weeks ago
This is not terrible. It may prevent "unintentionally downloaded" browsers to set themselves as default, wave browser comes to mind. I've seen that garbage in quite a few computers, running as a portable app - bypassing admin permissions to install - while users didn't even notice the differences between that and chrome.
If this mitigates or prevents crap like that, it deserves a thumbs up. But we know better. M$ will use this to their own benefit and shove edge into ppl's throats because they can.
mikebutash - 2 weeks ago
"This is not terrible. It may prevent "unintentionally downloaded" browsers to set themselves as default, wave browser comes to mind."
Coming from M$, I only interpret it as a trojan horse, wolf in sheep's clothing. Looks good on the outside, like they're doing something nice for security, but then they'll "accidentally" randomly push updates that revert this in some wave of managers holding the edge team accountable to increase numbers again.
Lina Khan in the FTC now seems intent to stir the pot with all these companies over antitrust, it would be nice for them to investigate M$ again over their painfully obvious Edge browser shenanigans. This isn't even as bad as them "accidentally" upgrading the OS of people, or sending malware-ish popups to people to coerce upgrade without a clear option to NOT do so.
Grumpy-J - 2 weeks ago
Wow, Microsoft **REALLY** wants to drive people away from their software. If so that could be a good thing, maybe MSWin will die the death it should have died 25 or more years ago.