
The U.S. Department of Homeland Security's Cyber Safety Review Board (CSRB) has released a scathing report on how Microsoft handled its 2023 Exchange Online attack, warning that the company needs to do better at securing data and be more truthful about how threat actors stole an Azure signing key.
Microsoft believes that last May's Exchange Online hack is linked to a threat actor known as 'Storm-0558' stealing an Azure signing key from an engineer's laptop that was previously compromised by the hackers at an acquired company.
Storm-0558 is a cyberespionage actor affiliated with China that has been active for more than two decades targeting a wide range of organizations.
Almost 10 months after Microsoft started the investigation, the CSRB states there isn’t any definitive evidence on how the threat actor obtained the signing key, regardless of what Microsoft previously claimed.
"Big Yellow Taxi" alert
The CSRB conducted its analysis of the Microsoft Exchange Online hack in 2023 based on details obtained from impacted organizations, cybersecurity companies and experts, law enforcement agencies, and meetings with Microsoft representatives.
The report notes that Microsoft learned of the intrusion after being alerted by the U.S. State Department on June 16, 2023.
Signs of the intrusion on the State Department’s mail systems appeared a day earlier when the organization’s security operations center (SOC) observed anomalous access.
Multiple security alerts appeared the next day thanks to a custom rule, internally called “Big Yellow Taxi,” for analyzing the MailItemsAccessed log available through the Audit (Premium) service for extended record retention.
One capability of the MailItemsAccessed mailbox-auditing action is to track and record access to individual messages (bind operation).
Creating the “Big Yellow Taxi” rule was possible because the U.S. State Department purchased a Microsoft 365 Government G5 license that comes with enhanced logging through the premium tier of Microsoft’s Purview Audit service.
However, other breached organizations were unable to detect that their accounts were breached as they had not purchased the premium logging features.
This led to Microsoft working with CISA to offer critical logging features for free, so all customers could detect similar attacks.
In February, Microsoft decided to expand the default log retention period from 90 to 180 days for all Purview Audit standard customers and provide additional telemetry data to federal agencies.
The forgotten key and update
Starting mid-May 2023, email accounts of more than 500 individuals at 22 organizations were compromised in a cyberespionage campaign by Chinese hacking group Storm-0558.
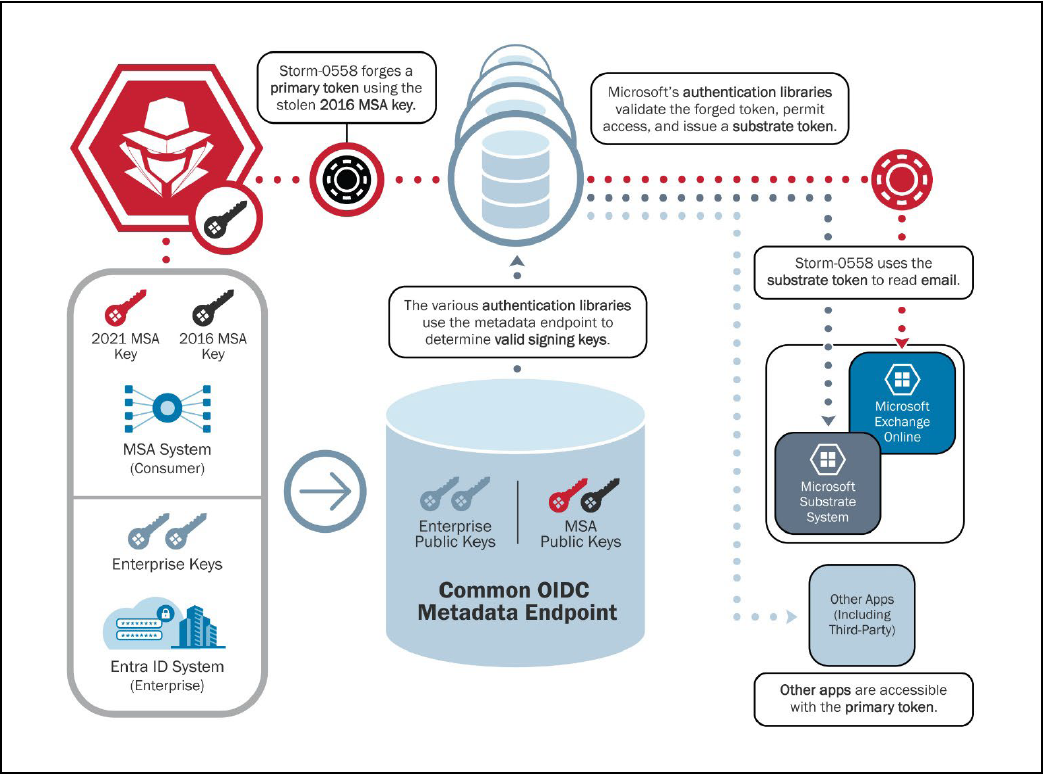
The hackers accessed the email accounts using forged authentication tokens signed with a Microsoft Services Account (MSA) consumer key the company created in 2016 and which should have been revoked in March 2021.
The reason for the key being still valid in 2021 is that rotating the keys was done manually for the consumer system at the time, unlike the automated process for enterprise.
After a major cloud outage because of the manual rotation, Microsoft stopped the process completely in 2021, leaving no system in place to alert employees of old, active signing keys in the consumer MSA service that should be retired.
Although the 2016 MSA key was designed to sign access tokens only for consumer accounts, a previously unknown vulnerability allowed Storm-0558 to use it with enterprise emails, too.
In a board meeting with CSRB, Microsoft explained that the issue was introduced with the creation of an OpenID Connect (OIDC) endpoint service that listed active signing keys for both enterprise and consumer identity systems.
Source: CSRB
However, the software development kits (SDKs) were not properly updated to distinguish on the endpoint between MSA signing keys for consumers and enterprises.
This allowed authentication for the email application through the Microsoft Entra identity and access management (IAM) system using either key type.
It is unclear how the threat actor discovered they could take advantage of the issue to forge tokens that worked for both consumer and enterprise accounts but Microsoft speculates they learned of the capability through trial and error.
Crash dumps from 2021
While Microsoft said in September that the threat actor likely obtained the 2016 MSA key from crash dumps, the company updated the initial blog post three months later on March 12, 2024, to clarify that it was a theory and did not find any evidence to support it.
During the investigation of the incident, Microsoft chased this scenario, which is one in a total of 46 that included an adversary with quantum computing capabilities that could break public-key cryptography.
The theory that Microsoft shared with the CSRB is that the 2023 Exchange Online hack is connected to another incident in 2021 where the same threat actor compromised its corporate network through an engineer’s account that had been hacked more than a year earlier, and provided access to sensitive authentication and identity data.
When the engineer’s device was compromised, they were working for Affirmed Networks, which Microsoft acquired in 2020 to consolidate its cloud platform with “fully virtualized, cloud-native mobile network solutions” for operators that wanted to deploy and maintain 5G networks more easily and with lower costs.
After acquiring Affirmed Networks and without running a cybersecurity audit, Microsoft provided corporate credentials to the engineer whose device Storm-0558 had already compromised.
However, the CSRB says that Microsoft has not been able to provide any evidence to support this theory and only updated its advisory with clarifications after receiving pressure to do so from the Board.
“Microsoft believes, although it has produced no specific evidence to such effect, that this 2021 intrusion was likely connected to the 2023 Exchange Online compromise because it is the only other known Storm-0558 intrusion of Microsoft’s network in recorded memory. During this 2021 incident, Microsoft believes that Storm-0558 gained access to sensitive authentication and identity data” - Cyber Safety Review Board
The CSRB says that, to this day, Microsoft still has no conclusive evidence as to how the threat actors stole the signing key, and that the investigation is ongoing.
Storm-0558 focuses on espionage
During the 2023 intrusion, the threat actor accessed emails from senior U.S. government representatives who were involved in national security matters:
- Commerce Secretary, Gina Raimondo
- U.S. Ambassador to the People’s Republic of China, R. Nicholas Burns
- Congressman Don Bacon
- Assistant Secretary of State for East Asian and Pacific Affairs, Daniel Kritenbrink
For at least six weeks, the hackers stole around 60,000 unclassified emails just from the U.S. Department of State.
Microsoft describes Storm-0558 as a China-based threat actor focused on espionage that operates as a distinct group but whose activities and methods show an overlap with other Chinese groups.
Its targets are mainly in the US and Europe and consist of “diplomatic, economic, and legislative governing bodies, and individuals connected to Taiwan and Uyghur geopolitical interests.”
The company notes that the hacker group shows high operational security and technical skills, an in-depth understanding of many authentication techniques and applications, and is well-informed of a target’s environment.
In a meeting with the CSRB, Google representatives said that its Threat Analysis Group (TAG) was able to link “at least one entity” related to Storm-0558 to the group behind Operation Aurora, a cyberattack in 2009 from China that compromised Google’s corporate infrastructure and resulted in the theft of intellectual property.
As part of Operation Aurora, which was the first large-scale sophisticated attack on the commercial sector, more than 20 other companies were compromised, including Yahoo, Adobe, Morgan Stanley, Juniper Networks, Symantec, Northrop Grumman, and Dow Chemical.
Microsoft says that the objective in most Storm-0558 campaigns is to obtain access to the email accounts of the targeted organization through methods varying from credential harvesting and phishing, to OAuth token attacks.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now