
A new Android banking malware named 'SoumniBot' is using a less common obfuscation approach by exploiting weaknesses in the Android manifest extraction and parsing procedure.
The method enables SoumniBot to evade standard security measures found in Android phones and perform info-stealing operations.
The malware was discovered and analyzed by Kaspersky researchers, who provide the technical details on the methods the malware uses to take advantage of the Android routine to parse and extract APK manifests.
Tricking Android's parser
Manifest files ('AndroidManifest.xml') are present in each app's root directory and contain details about components (services, broadcast receivers, content providers), permissions, and app data.
While there are Zimperium various compression tricks malicious APKs can use to fool security tools and evade analysis, Kaspersky analysts found that SoumniBot uses three different methods that involve manipulation of the manifest file's compression and size, to bypass parser checks.
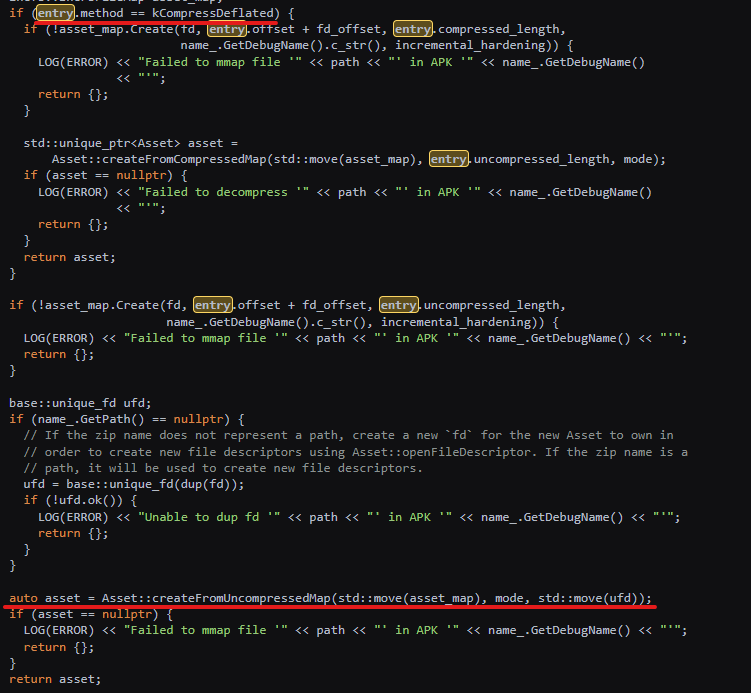
First, SoumniBot uses an invalid compression value when unpacking the APK's manifest file, which diverges from the standard values (0 or 8) expected by the Android 'libziparchive' library tasked with the role.
Instead of treating these values as unacceptable, the Android APK parser defaults to recognizing the data as uncompressed due to a bug, allowing the APK to bypass security checks and continue execution on the device.
(Kaspersky)
The second method involves misreporting the size of the manifest file in the APK, supplying a value larger than the actual figure.
Since the file has been marked as uncompressed in the previous step, it is copied directly from the archive, with junk "overlay" data filling the difference.
Kaspersky explains that while this extra data does not directly harm the device since Android is set to ignore it, it plays a crucial role in confusing code analysis tools.

(Kaspersky)
The third evasion technique is to use very long strings for the names of XML namespaces in the manifest file, making it very difficult for automated analysis tools to check them, which often lack enough memory to process them.

(Kaspersky)
Kaspersky has informed Google about the inability of APK Analyzer, Android's official analysis utility, to handle files using the above evasion methods.
BleepingComputer has also contacted Google for a comment, and a spokesperson has responded with the following statement:
Based on our current detection, no apps containing this malware are found on Google Play. Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services.
Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play. - Google spokesperson
The SoumniBot threat
Upon launch, SoumniBot requests its configuration parameters from a hardcoded server address and sends profiling information for the infected device, including number, carrier, etc.
Next, it initiates a malicious service that restarts every 16 minutes if stopped, and transmits stolen data from the victim every 15 seconds.
The exfiltrated details include IP addresses, contact lists, account details, SMS messages, photos, videos, and online banking digital certificates.
The data exfiltration is controlled by commands the malware receives via an MQTT server. These commands also order functions such as:
- Deleting existing or adding new contacts
- Sending an SMS message (forwarding)
- Setting ringtone volume levels
- Turning silent mode on or off
- Turning the debug mode on the device on or off
It is unclear how SoumniBot reaches devices but methods may vary from distribution over third-party Android stores and unsafe websites to updating with malicious code legitimate apps in trusted repositories.
SoumniBot targets Korean users and like many malicious Android apps, it hides its icon after installation to make it more difficult to remove it. However, it remains active in the background, uploading data from the victim.
Kaspersky provides a short set of indicators of compromise, which includes hashes for the malware and two domains that malware operators use for command and control activity.
Update 4/18 - Added Google comment


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now