
Hackers are abusing an anti-cheat system driver for the immensely popular Genshin Impact game to disable antivirus software while conducting ransomware attacks.
The driver/module, "mhypro2.sys," doesn't need the target system to have the game installed, and it can operate independently or even embedded in malware, offering the threat actors a powerful vulnerability that can disable security software.
The vulnerable driver has been known since 2020 and gives access to any process/kernel memory and the ability to terminate processes using the highest privileges.
Researchers reported the issue to the vendor multiple times in the past. However, the code-signing certificate hasn't been revoked, so the program can still be installed on Windows without raising any alarms.
To make matters worse, there have been at least two proof-of-concept exploits [1, 2] on GitHub since 2020, with full details on how to read/write kernel memory with kernel mode privileges from user mode, enumerate threads, and terminate processes.
Abusing Genshin Impact's anti-cheat system
In a new report by Trend Micro, researchers have seen evidence of threat actors abusing this driver since late July 2022, with ransomware actors using it to disable otherwise properly configured endpoint protection solutions.
The threat actors used 'secretsdump' and 'wmiexec' against a targeted endpoint and then connected to the domain controller via RDP using the snatched admin credentials.
The first action taken on the compromised machine was to transfer mhyprot2.sys to the desktop along with a malicious executable 'kill_svc.exe,' which is used to install the driver.
Next, the intruders dropped 'avg.msi,' which in turn drops and executes the following four files:
- logon.bat – A batch file that executes HelpPane.exe, kills antivirus and other services, and executes svchost.exe
- HelpPane.exe – A malicious file masquerading as Microsoft Help and Support executable; similar to kill_svc.exe, it installs mhyprot2.sys and kills antivirus services
- mhyprot2.sys – The vulnerable Genshin Impact anti-cheat driver
- svchost.exe – The ransomware payload
Trend Micro comments that the threat actors tried and failed thrice to encrypt the files on the attacked workstation, but the antivirus services were successfully disabled. Eventually, the adversaries moved "logon.bat" on the desktop and executed it manually, which worked.
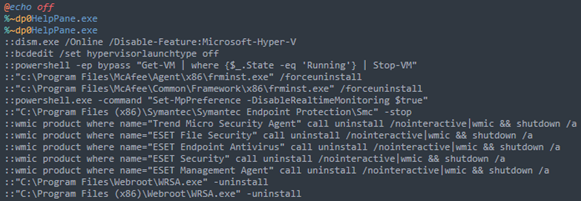
Finally, the threat actor loaded the driver, the ransomware, and the 'kill_svc.exe' executable on a network share for mass deployment, intending to infect more workstations.
.png)
Trend Micro did not share what ransomware was being used in these attacks.
Protecting your devices
Trend Micro warns that hackers' deployment of the anti-cheat module may increase, as even if the vendor responds and fixes the flaw, old versions of it will continue to circulate.
"It is still rare to find a module with code signing as a device driver that can be abused," comment the researchers.
Security research Kevin Beaumont advises that admins can defend against this threat by blocking the "0466e90bf0e83b776ca8716e01d35a8a2e5f96d3" hash on their security solution, which corresponds to the vulnerable mhypro2.sys driver.
Finally, defenders should monitor event logs for the specific service installation, named "mhyprot2."


Comments
GT500 - 1 year ago
I think we're going to be seeing this sort of thing a lot more, especially now that we're in the age of anti-cheats that run 24/7 on your PC even when no games are running (such as the ones that come with Valorant, League of Legends, modern Call of Duty games, etc).
NoneRain - 1 year ago
kernel-level anti-cheat... why would that be a bad idea? /s