
A new macOS malware dubbed 'KandyKorn' has been spotted in a campaign attributed to the North Korean Lazarus hacking group, targeting blockchain engineers of a cryptocurrency exchange platform.
The attackers impersonate members of the cryptocurrency community on Discord channels to spread Python-based modules that trigger a multi-stage KandyKorn infection chain.
Elastic Security discovered and attributed the attacks to Lazarus based on overlaps with past campaigns concerning the employed techniques, network infrastructure, code-signing certificates, and custom Lazarus detection rules.
Targeting the crypto community
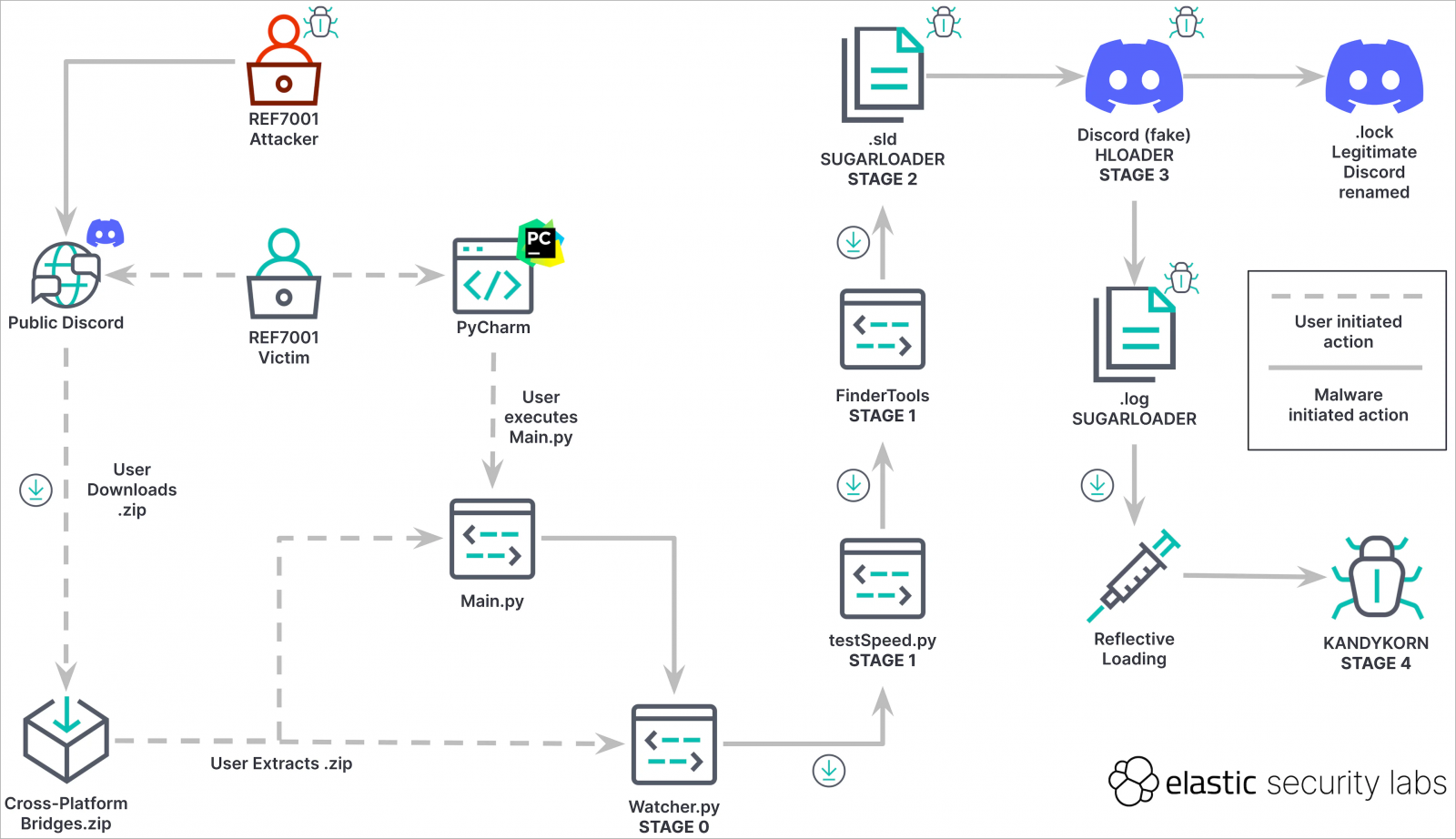
The attack, which starts on Discord, starts with social engineering attacks on targets to trick them into downloading a malicious ZIP archive named 'Cross-platform Bridges.zip.'
The victim is misled into believing they are downloading a legitimate arbitrage bot designed for automated profit generation from cryptocurrency transactions.
Instead, the contained Python script ('Main.py') will import 13 modules from an equal number of scripts in the ZIP, launching the first payload, 'Watcher.py.'
Watcher.py is a downloader that unpacks and executes a second Python script named 'testSpeed.py' along with another Python file named 'FinderTools,' downloaded from a Google Drive URL.
FinderTools is a dropper that fetches and launches an obfuscated binary named 'SugarLoader,' which appears under two names and instances, as an .sld and a .log Mach-O executables.
Sugarloader establishes a connection with the command and control (C2) server to get and load the final payload, KandyKorn, into memory using reflective binary loading.
macOS persistence trick
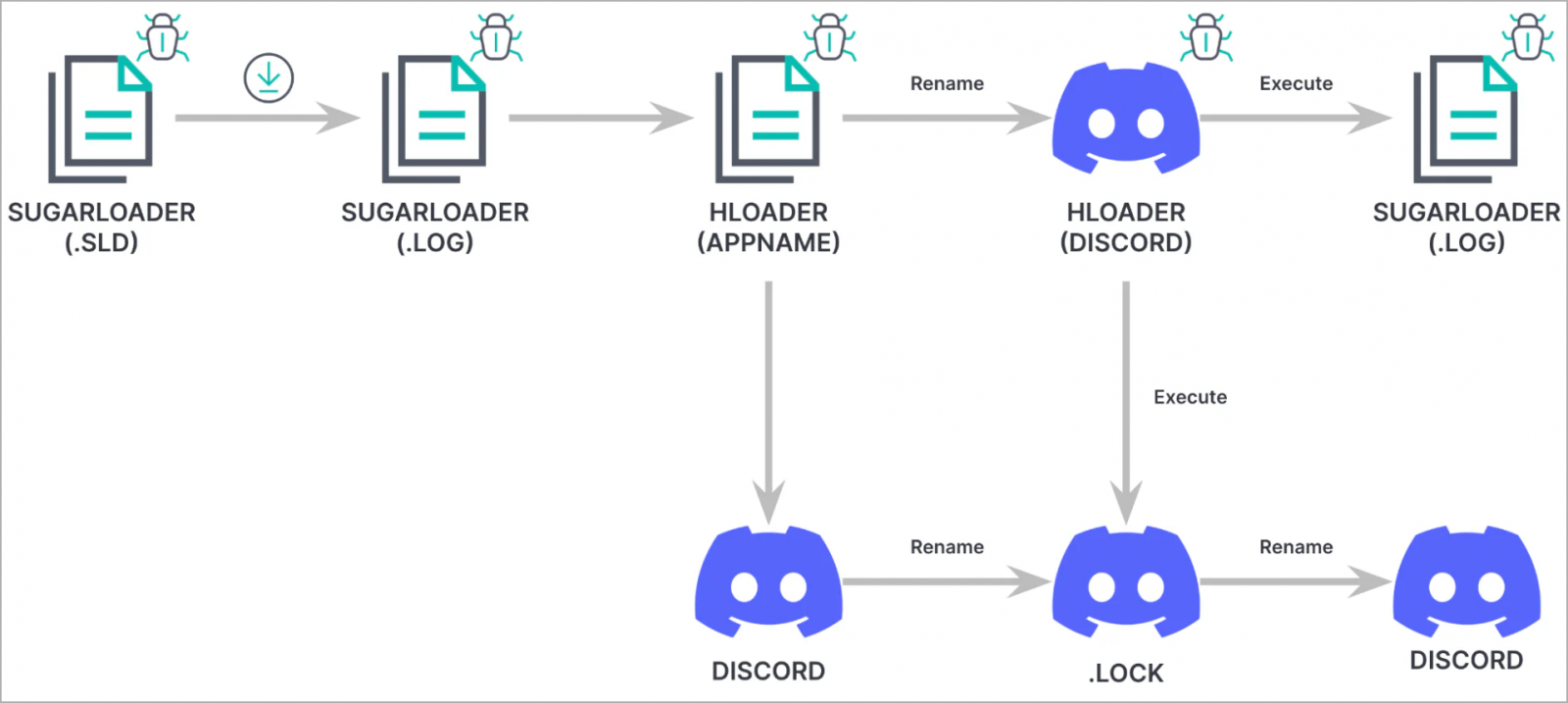
At the final stage of the attack, a loader known as HLoader is used, which impersonates Discord and uses macOS binary code-signing techniques seen in past Lazarus campaigns.
HLoader establishes persistence for SugarLoader by hijacking the real Discord app on the infected system, following a series of binary renaming actions.
"We observed the threat actor adopting a technique we have not previously seen them use to achieve persistence on macOS, known as execution flow hijacking," explains Elastic.
Specifically, HLOADER performs the following operations upon launch:
- Renames itself from Discord to MacOS.tmp
- Renames the legitimate Discord binary from .lock to Discord
- Executes both Discord and .log using NSTask.launchAndReturnError
- Renames both files back to their initial names
KandyKorn
KandyKorn is an advanced final-stage payload that enables Lazarus to access and steal data from the infected computer.
It operates in the background as a daemon, waiting for commands from the C2 server and avoiding sending heartbeats to minimize its trace on the system.
KandyKorn supports the following 16 commands:
- 0xD1: Terminates the program.
- 0xD2: Gathers system info.
- 0xD3: Lists directory contents.
- 0xD4: Analyzes directory properties.
- 0xD5: Uploads files from the C2 to the victim's computer.
- 0xD6: Exfiltrate files from the victim to the C2.
- 0xD7: Archives and exfiltrates directories.
- 0xD8: Securely deletes files using overwriting with zeros.
- 0xD9: Lists all running processes.
- 0xDA: Kills a specified process.
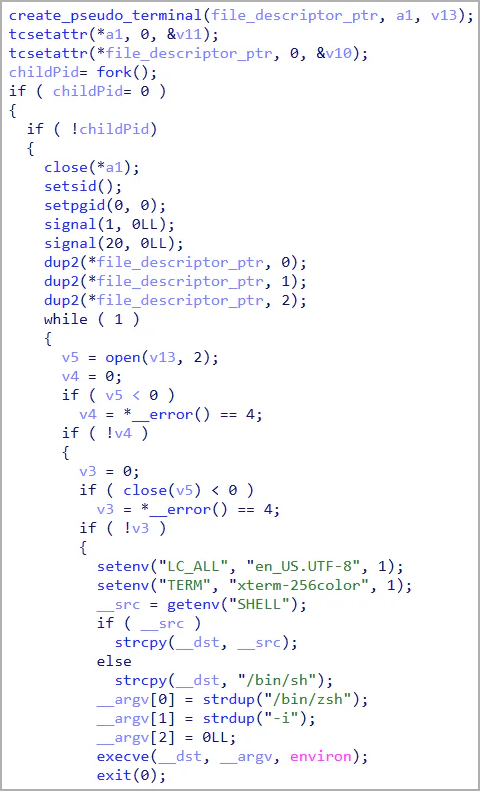
- 0xDB: Executes system commands via a pseudoterminal.
- 0xDC: Retrieves command outputs.
- 0xDD: Initiates an interactive shell.
- 0xDE: Retrieves current configuration.
- 0xDF: Updates C2 configuration.
- 0xE0: Pauses operations temporarily.
In summary, KandyKorn is a particularly stealthy backdoor capable of data retrieval, directory listing, file upload/download, secure deletion, process termination, and command execution.
The cryptocurrency sector remains a primary target for Lazarus, primarily motivated by financial gain rather than espionage, which is their other main operational focus.
The existence of KandyKorn underscores that macOS is well within Lazarus' targeting range, showcasing the threat group's remarkable ability to craft sophisticated and inconspicuous malware tailored for Apple computers.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now