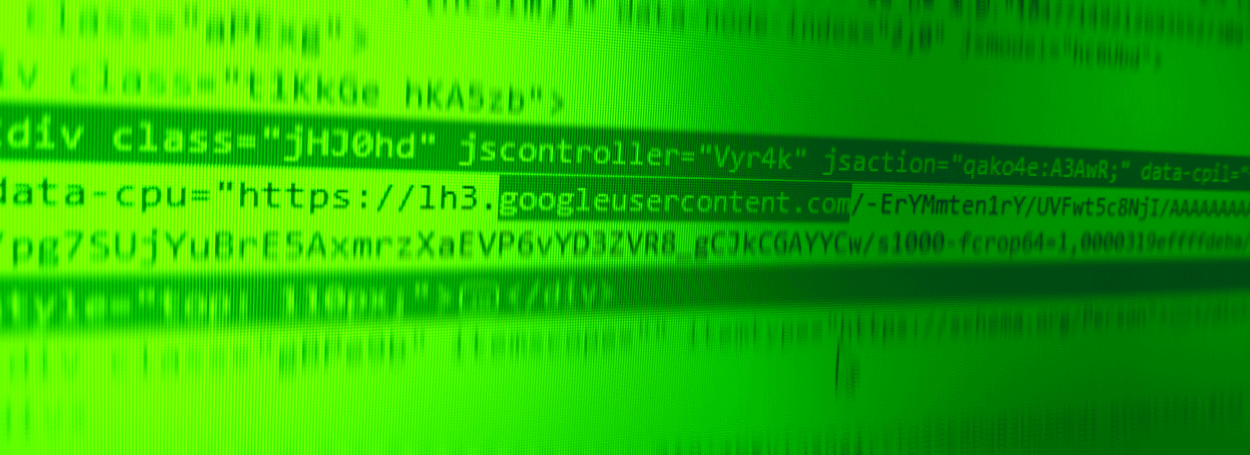
Hackers are hiding malicious code inside the metadata fields of images hosted on Google's official CDN (content delivery network) —googleusercontent.com.
The type of images that are being hosted on this domain are usually the photos uploaded on Blogger.com sites and the Google+ social network.
Denis Sinegubko, a security researcher with web security firm Sucuri (now part of GoDaddy), has recently discovered one malware distribution campaign where the GoogleUserContent CDN was used to host one such malicious image.
From EXIF field to web shell
In a report published on Wednesday, Sinegubko says he found a malware operation focused on stealing PayPal security tokens (for bypassing PayPal authentication) where crooks were loading an image hosted on googleusercontent.com, extracting and then executing code found in its "UserComment" EXIF metadata field.
The code contained in that field was a Base64-encoded string that when decoded multiple times would end up being a script that could upload a predefined web shell on the compromised server, along with various other files.
This web shell could then be used for defacing the server, and emailing the addresses of successfully exploited sites back to the attacker.
Issues with taking down the malicious image
What drew Sinegubko's attention to this case was not the trick of hiding malicious code inside an image's EXIF fields, but the use of the GoogleUserContent CDN to host these files.
Crooks have hidden malicious code in image metadata fields before, or in the image itself (a technique known as steganography).
Hosting the images on the GoogleUserContent CDN was a unique approach, one that gave the Sucuri researcher quite a few headaches.
The biggest was that there was no simple way to report the malicious image to Google, which has forms set up for reporting copyright infringement, but not security issues.
"Google has many tools to remove content but it’s not obvious how to report malware in images," Sinegubko said. "Most of their tools require providing links to original posts, pages, or comments that contain the infringing content. The image here is not a part of some known public content."
Researchers can't identify source of the malicious upload
"We don’t even know which user created it. It could be an image uploaded for a Blogger post, Google+ post, or even a public picture from Google Photos," the researcher added. "It’s hard to say where the images originate from, as their URLs are anonymized and have the same format."
Sinegubko says that malicious code hidden in images uploaded on Google sites outlives malware hosted on other public sites such as the malware uploaded on GitHub, Pastebin, Twitter, or other similar services.
Furthermore, the researcher also draws a sign of alarm regarding security scans of image files, which are usually ignored by most web-based security scanners.
Such tools usually look for malware in text-based files such as HTML, PHP, JS, or other typical server files, but do not scan the metadata of images hosted or loaded on a site.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now