Security experts from MindPoint Group, an information security firm, have hijacked over 2,000 subdomains from legitimate websites while researching possible security flaws in Amazon's CloudFront CDN service.
Experts found that CloudFront's CDN routing mechanism that linked a site's domain and subdomains to a specific server contained a flaw that allowed attackers to point misconfigured subdomains to their own endpoint instead, effectively hijacking the subdomain from legitimate CloudFront users.
Custom script hijacks over 2,000 official subdomains
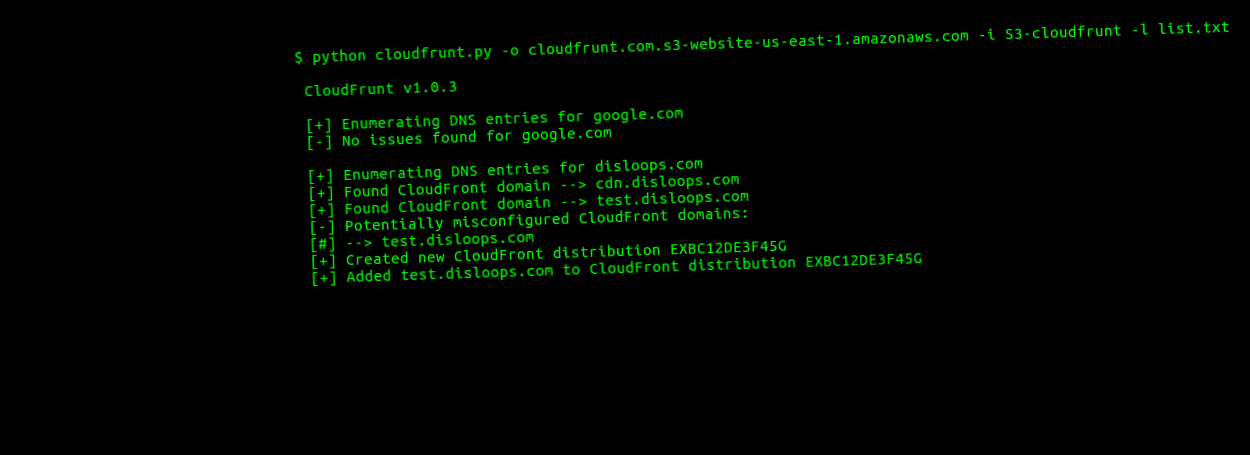
MindPoint security analyst Matt Westfall coded and deployed a proof-of-concept Python script that automatically scanned CloudFront domains and hijacked vulnerable subdomains, pointing the servers to a demo page he created.
Westfall says he hijacked over 2,000 subdomains over the period of a few days just by using his script. Some of the most high-profile subdomains belonged to companies such as the Red Cross, Bloomberg, Reuters, Dow Jones, Harvard, University of Maryland, the Commonwealth Bank of Australia, and two US government agencies.
"When subdomains from a high-trust domain are hijacked, they can be set up as a watering hole for delivering malware that has a high likelihood of bypassing filtering mechanisms," Westfall says.
Furthermore, these subdomains are perfect for spear-phishing attacks, being almost impossible to detect even by the most astute and security-hardened user.
Amazon has taken ownership of the hijacked subdomains
The researcher says he notified Amazon of his findings, and in the span of three days, he transferred ownership of these vulnerable subdomains back to Amazon, who is now running a warning on the subdomains, hoping that the legitimate owners rectify the misconfigured CDNs.
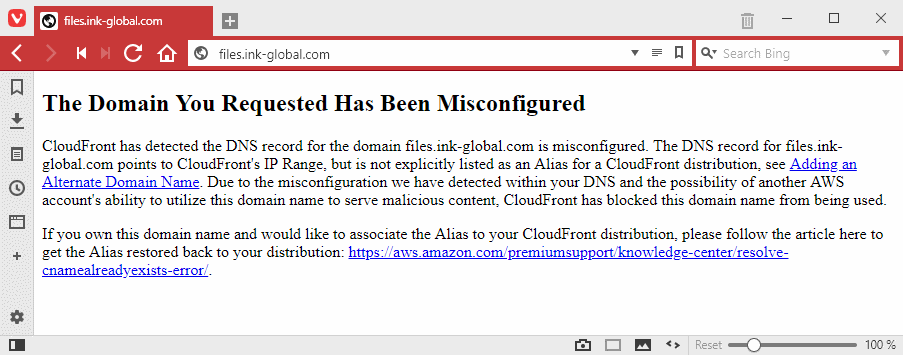
"A number of discussions with both the AWS Security team and the CloudFront engineers have followed," Westfall said in a blog post detailing the hijacking attack's technical details.. "The CloudFront team accepts that the nuances of CloudFront’s routing mechanism that led to this condition leave room for improvement. However, AWS has deemed that this is not a vulnerability in the CloudFront service."
Instead, starting yesterday, Amazon has begun showing a popup in the AWS CloudFront console when a user removes a CNAME from a CloudFront distribution, alerting the user to keep DNS records in sync with their CloudFront distribution, a setting that would prevent the CloudFront distribution's subdomain from getting hijacked.
Amazon also launches new AWS security-focused tools
This new popup alert is part of a large number of security updates Amazon rolled out to customers yesterday.
⌦ Amazon rolled out a new service named AWS Firewall Manager that simplifies the management of AWS WAF firewalls across multiple accounts and servers.
⌦ Amazon rolled out a new service named Private Certificate Authority (CA) that lets customers use private certificates without the need for specialized infrastructure.
⌦ Amazon added support for encrypting data in transit for the Amazon Elastic File System (EFS).
Last year, Amazon also rolled out significant changes to the AWS dashboard, adding visible warnings for situations when customers were leaving AWS buckets exposed to the public, a common misconfiguration that was at the base of many data breaches in the past few years.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now