
Image: Mahadevu Udaya Bhaskar
GitLab has addressed a critical severity vulnerability that could allow remote attackers to take over user accounts using hardcoded passwords.
The bug (discovered internally and tracked as CVE-2022-1162) affects both GitLab Community Edition (CE) and Enterprise Edition (EE).
This flaw results from static passwords accidentally set during OmniAuth-based registration in GitLab CE/EE.
"A hardcoded password was set for accounts registered using an OmniAuth provider (e.g. OAuth, LDAP, SAML) in GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to potentially take over accounts," the GitLab team explained in a security advisory published on Thursday.
GitLab urged users to immediately upgrade all GitLab installations to the latest versions (14.9.2, 14.8.5, or 14.7.7) to block potential attacks.
"We strongly recommend that all installations running a version affected by the issues described below are upgraded to the latest version as soon as possible," they said.
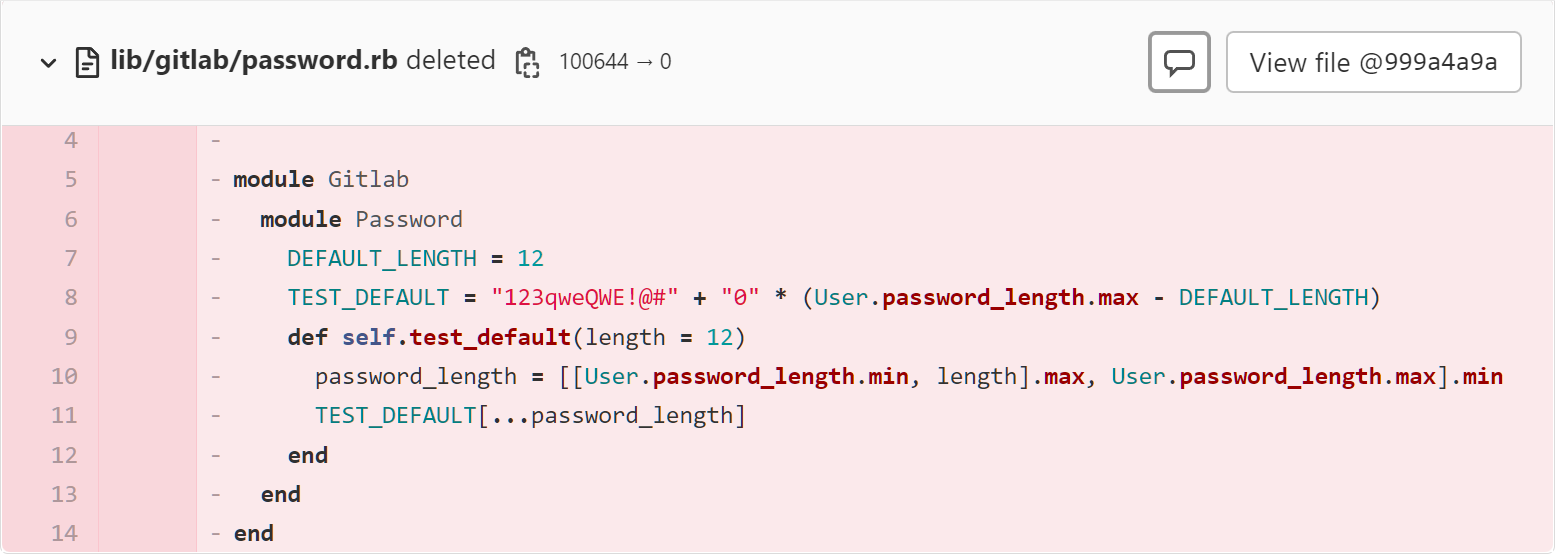
A code commit submitted two days shows that GitLab deleted the 'lib/gitlab/password.rb' file, which was used to assign a weak hardcoded password to the 'TEST_DEFAULT' constant.
Passwords reset for some GitLab users
GitLab also added that it reset the passwords of a limited number of GitLab.com users as part of the CVE-2022-1162 mitigation effort.
It also found no evidence that any accounts have been compromised by attackers using this hardcode password security flaw.
"We executed a reset of GitLab.com passwords for a selected set of users as of 15:38 UTC," the GitLab team said.
"Our investigation shows no indication that users or accounts have been compromised but we're taking precautionary measures for our users' security."
When asked to share the number of Gitlab.com users who had their passwords reset, a GitLab spokesperson shared the info already available in the advisory telling BleepingComputer that they only did it for "a selected set of users."
At this time, no malicious activity or compromise has been identified on https://t.co/C4mACZpLWf related to the potential Okta breach. We continue to monitor and investigate, and strongly recommend enabling MFA. You can see our response here: https://t.co/nlO7QcGq34
— GitLab (@gitlab) March 22, 2022
Script to identify affected user accounts
While GitLab says no user accounts have been breached so far, the company has created a script that self-managed instance admins can use to identify user accounts potentially impacted by CVE-2022-1162.
After identifying potentially affected user accounts, admins are advised to reset the users' passwords.
Over 100,000 organizations use its DevOps platform, according to GitLab, and the company estimates it has more than 30 million estimated registered users from 66 countries worldwide.
Update April 01, 12:08 EDT: Added CVE-2022-1162 script information.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now