
Updated: Added official statements from GitHub, GitLab, and Bitbucket at the end of the article. Also added links to a joint post-incident review blog issued by Atlassian Bitbucket, GitHub, GitLab.
Attackers are targeting GitHub, GitLab, and Bitbucket users, wiping code and commits from multiple repositories according to reports and leaving behind only a ransom note and a lot of questions.
The targets who had their repos compromised use multiple Git-repository management platforms, with the only other connection between the reports besides Git being that the victims were using the cross-platform SourceTree free Git client [1, 2, 3, 4].
While BleepingComputer couldn't get in touch with Atlassian, the company behind Bitbucket and SourceTree, one user supposedly received a statement from the company saying that:
"Within the past few hours, we detected and blocked an attempt — from a suspicious IP address — to log in with your Atlassian account. We believe that someone used a list of login details stolen from third-party services in an attempt to access multiple accounts."
After infiltrating the victims' repo and wiping out all commit history, the attackers will only leave behind one commit named 'WARNING' containing a single file with the following contents (the ransom note):
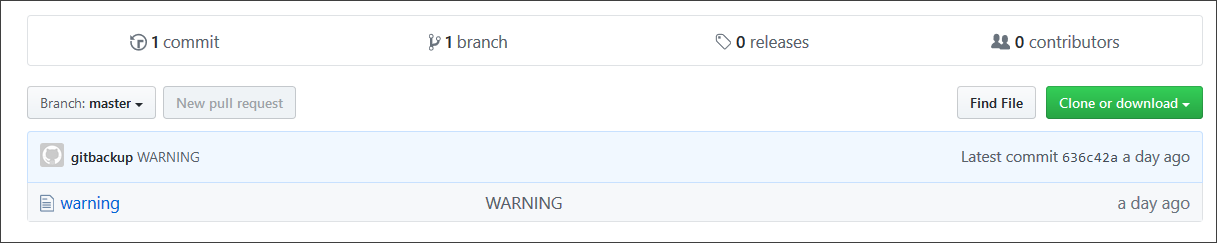
This "warning" ransom note asked victims to send a 0.1 BTC, which equivalent to roughly $568, in order get their data back.
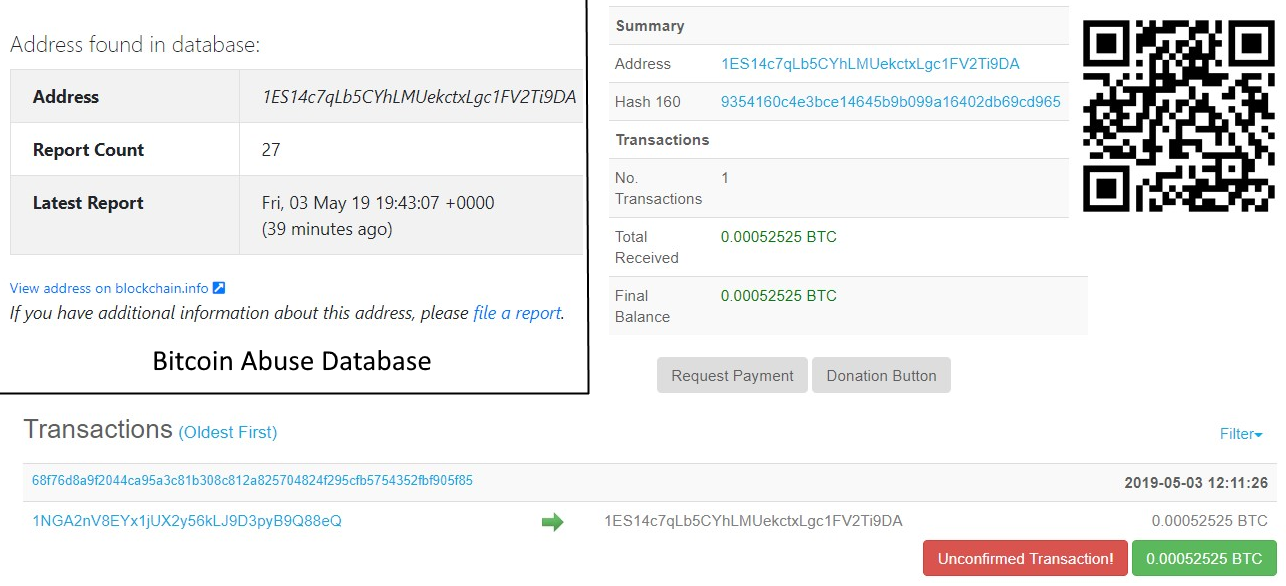
To recover your lost code and avoid leaking it: Send us 0.1 Bitcoin (BTC) to our Bitcoin address 1ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA and contact us by Email at admin@gitsbackup.com with your Git login and a Proof of Payment. If you are unsure if we have your data, contact us and we will send you a proof. Your code is downloaded and backed up on our servers. If we dont receive your payment in the next 10 Days, we will make your code public or use them otherwise.
On the BitcoinAbuse platform, the Bitcoin address used by the attackers already has 27 reports, with the first report having been filed on May 2.
However, when searching for it on GitHub we found 392 impacted repositories which got all their commits and code wiped using the 'gitbackup' account which joined the platform seven years ago, on January 25, 2012.
Despite that, none of the victims have paid the ransom the hackers have asked for, seeing that the Bitcoin address received only 0.00052525 BTC on May 3 via a single transaction, which is the equivalent of roughly $2.99.
There are no details at the moment on how the attackers were able to get access to their victims' accounts but, as one StackExchange user said, even though he had 2FA enabled, he "never got a text message indicating they had a successful brute login."
One report states that GitHub has been suspending accounts and investigating after the attacks have been detected: "GitHub suspended my account last night whilst they investigate, I should hopefully hear from them today. I might have just been lucky."
Additionally, while GitHub, GitLab, and Bitbucket haven't yet issued any statements regarding the ongoing attack, the users have been scrambling trying to find a solution to fix the issue, with an ongoing discussion being available HERE and a possible fix in this StackExchange post.
BleepingComputer has reached out to GitHub and GitLab for comment, but had not heard back by the time of this publication.
Update May 03 19:05 EDT: GitLab got back to BleepingComputer with the following response from the company's Director of Security Kathy Wang:
We identified the source based on a support ticket filed by Stefan Gabos yesterday, and immediately began investigating the issue. We have identified affected user accounts and all of those users have been notified. As a result of our investigation, we have strong evidence that the compromised accounts have account passwords being stored in plaintext on a deployment of a related repository. We strongly encourage the use of password management tools to store passwords in a more secure manner, and enabling two-factor authentication wherever possible, both of which would have prevented this issue.
Atlassian also provided a comment saying that they are "contacting all impacted Bitbucket Cloud users with the following statement. Only users impacted by this are getting the communication:"
Bitbucket Cloud Security Advisory: Unauthorized Access to your Repository
We are contacting you because your Bitbucket Cloud repository was recently accessed and deleted by an unauthorized third party.
We are in the process of restoring your repository and expect it to be restored within the next 24 hours.
We believe that this was part of a broader attack against several git hosting services, where repository contents were deleted and replaced with a note demanding the payment of ransom.
During this attack, a third party accessed your repository by using the correct username and password for one of the users with permission to access your repository. We believe that these credentials may have been leaked through another service, as other git hosting services are experiencing a similar attack.
We have not detected any other compromise of Bitbucket.
We have proactively reset passwords for those compromised accounts to prevent further malicious activity. We will also work with law enforcement in any investigation that they pursue.
We encourage you and your team members to reset all other passwords associated with your Bitbucket account. In addition, we recommend enabling 2FA on your Bitbucket account.
If you have any questions or would like further assistance, please contact our support.
Sincerely,
The Bitbucket Team
Update May 04 11:24 EDT: A GitHub spokesperson also got back to us with an official statement:
GitHub has been thoroughly investigating these reports, together with the security teams of other affected companies, and has found no evidence GitHub.com or its authentication systems have been compromised. At this time, it appears that account credentials of some of our users have been compromised as a result of unknown third-party exposures. We are working with the affected users to secure and restore their accounts. We encourage all developers and customers to use two-factor authentication and strong and unique login passwords as a standard practice.
Update May 14 14:21 EDT: Atlassian Bitbucket, GitHub, and GitLab published a joint post-incident review blog at:


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now