
Image: Eduardo Mallmann
The Federal Bureau of Investigation (FBI) says the Black Cat ransomware gang, also known as ALPHV, has breached the networks of at least 60 organizations worldwide between November 2021 and March 2022.
The FBI's Cyber Division revealed this in a TLP:WHITE flash alert released on Wednesday in coordination with the Cybersecurity and Infrastructure Security Agency (DHS/CISA).
The flash alert is part of a series of similar reports highlighting the tactics, techniques, and procedures (TTPs) used by and indicators of compromise (IOCs) linked to ransomware variants identified during FBI investigations.
Since the start of the year, the FBI has issued other alerts underlining how ransomware gangs, including BlackByte, Ragnar Locker, and Avoslocker, are targeting and have already breached dozens of US critical infrastructure organizations.
BlackCat/ALPHV "is the first ransomware group to do so successfully using RUST, considered to be a more secure programming language that offers improved performance and reliable concurrent processing," the FBI said.
BlackCat's ransomware executable is also highly customizable, and it comes with support for multiple encryption methods and options that make it easy to adapt attacks to a wide range of corporate environments
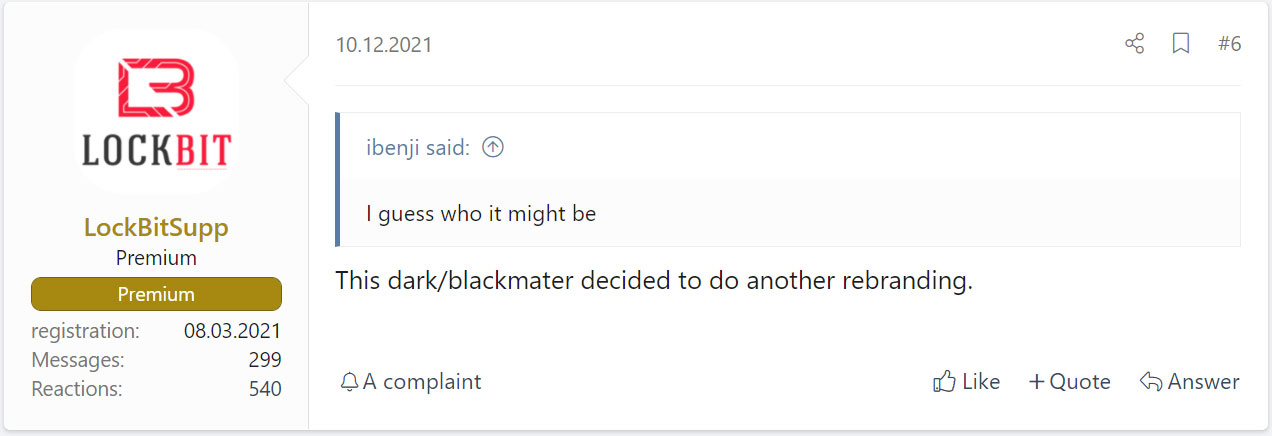
BlackCat ransomware, a BlackMatter rebrand
"Many of the developers and money launderers for BlackCat/ALPHV are linked to Darkside/Blackmatter, indicating they have extensive networks and experience with ransomware operations," the FBI also added.
The DarkSide RaaS operation launched in August 2020 and was shut down in May 2021 after law enforcement agencies' efforts to take down the gang following the widely publicized attack on Colonial Pipeline.
While they rebranded as BlackMatter on July 31st, they were soon forced to shut down again in November 2021, after Emsisoft found and exploited a weakness in the ransomware to create a decryptor, and the gang's servers were seized.
A representative of the LockBit ransomware gang was first to expose the BlackCat / BlackMatter link one month after BlackCat ransomware's November 2021 launch.
The BlackCat gang also established a connection in an interview with The Record published several months later, in February 2022, but did not confirm the actual rebrand from BlackMatter.
While BlackCat claims they are just a DarkSide/BlackMatter affiliate who launched their own Ransomware-as-a-Service (RaaS) operation, some security researchers are not buying it, especially after finding similarities in features and configuration files.
Victims asked to report attacks and not to pay ransoms
In the Wednesday flash alert, the FBI also asked admins who detect BlackCat activity to share any related info with their local FBI Cyber Squad.
Helpful information that would help track down and identify the threat actors behind this ransomware group includes "IP logs showing callbacks from foreign IP addresses, Bitcoin or Monero addresses and transaction IDs, communications with the threat actors, the decryptor file, and/or a benign sample of an encrypted file."
The FBI said that it doesn't encourage paying BlackCat ransoms since victims have no guarantee that this will prevent future attacks or leaks of stolen data.
However, the federal agency did acknowledge the damage inflicted by ransomware attacks, which may force company executives to pay the ransom and protect shareholders, customers, or employees.
The FBI also shared mitigation measures to help network defenders block such attacks and strongly urged all BlackCat victims to report such incidents to their local FBI field office.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now