
Update 4/5/24: More information added about discovered Windows encryptors.
Chilean data center and hosting provider IxMetro Powerhost has suffered a cyberattack at the hands of a new ransomware gang known as SEXi, which encrypted the company's VMware ESXi servers and backups.
PowerHost is a data center, hosting, and interconnectivity company with locations in the USA, South America, and Europe.
On Monday, PowerHost's Chile division, IxMetro, warned customers that it suffered a ransomware attack early Saturday morning that encrypted some of the company's VMware ESXi servers that are used to host virtual private servers for customers.
Customers hosting their websites or services on these servers are currently down as the company attempts to restore terabytes of data from backups.
In the latest update, PowerHost apologized to customers, warning that it may not be possible to restore servers as the backups have also been encrypted.
When attempting to negotiate with the threat actors to receive a decryption key, the ransomware gang demanded two bitcoins per victim, which PowerHost's CEO says would equal $140 million.
❖ PowerHost CEO Ricardo Rubem.
For VPS customers impacted by the attack and who still have their website content, the company is offering to set up a new VPS so that customers can bring their sites back online.
The new SEXi ransomware
According to CronUp cybersecurity researcher Germán Fernández, PowerHost was attacked using a new ransomware that appends the .SEXi extension and drops ransom notes named SEXi.txt.
The known attacks by the threat actors have only been seen targeting VMWare ESXi servers so far, why the ransomware operation chose the name 'SEXi,' which is a wordplay on 'ESXi.’
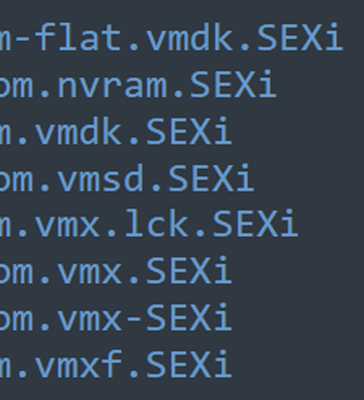
Source: Germán Fernández
As for the infrastructure of the ransomware operation, there is nothing special about it at this time. The ransom notes simply contain a message telling the victims to download the Session messaging app and to contact them at the listed address.
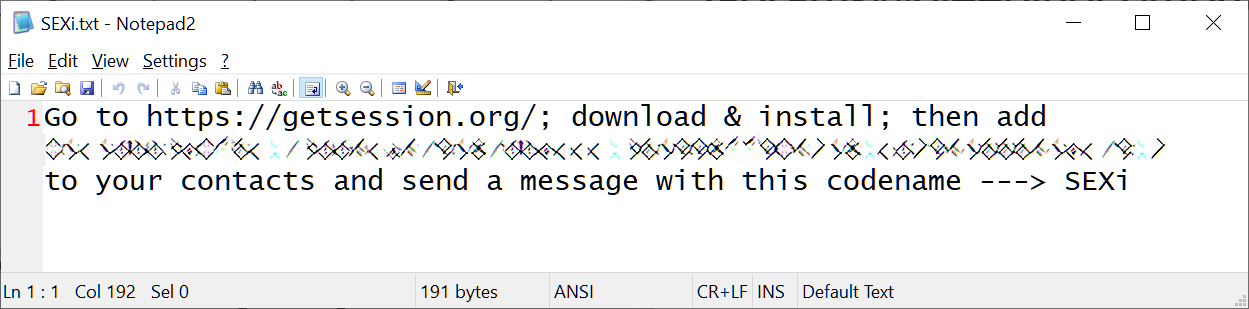
Source: BleepingComputer
While BleepingComputer has not been able to find a sample of the SEXi ransomware encryptor, SANS instructor Will Thomas found other variants that have been in use since February 2024.
These variants use the names SOCOTRA, FORMOSA, and LIMPOPO, with the LIMPOPO encryptor [VirusTotal] appending the .LIMPOPO extension to encrypted files.
It is unclear why the encryptors use these names, but SOCOTRA is an island of Yemen, FORMOSA is a republic that existed on the island of Taiwan in 1895, and LIMPOPO is a South African province.
The ransom notes in these samples and the SEXi attacks all share the Session contact ID, so there is nothing unique per victim in the ransom notes for all of these campaigns.
From the LIMPOPO sample shared by Thomas, we can see that they were created using the leaked Babuk ransomware source code, which has been used by numerous ransomware gangs to create ESXi encryptors.
BleepingComputer has not seen a Windows encryptor used in the new campaigns as of yet.
Furthermore, whether the attackers are stealing data to extort companies in double extortion attacks through data leak sites is unknown. However, as this is a very new ransomware operation, that could change at any time.
Update 4/5/24: Will Thomas found additional Windows encryptors related to this ransomware operation that were created using the leaked LockBit 3.0 source code.
The source code for LockBit 3.0, aka LockBit Black, was leaked by a developer for the ransomware operation who was upset with the gang's leadership.
The newly discovered Windows encryptors are for the FORMOSA and SOCOTRA campaigns and have slightly different ransom notes than the ESXi versions. These notes indicate that data was stolen in the attack and would be leaked if a ransom is not paid.
"We have exfiltrated all your valuable data. We are going to publish it on the dark web pretty soon," reads the Windows ransom note.
However, there is no known data leak site for this ransomware operation.
Update 4/4/24: Added more information about detected samples.
Update 4/5/24: Added information about found Windows encryptors.


Comments
senan - 2 weeks ago
we got the same attack like this
luxus555 - 2 weeks ago
Can you share more information how the managed to get access to Esxi?
Was that done through compromised SSH, or some known/unknown vulnerabilities?
senan - 2 weeks ago
we are not able to access our VM servers. the VMDK files are totally encrypted. in the investigation we found that the attacker came through the LAN pc and gain access to the servers and launched the attack. in your environment batter to disable the SSH and update necessary latest security patch for EXSI hots.
senan - 2 weeks ago
if anyone know to solution for decrypt please let me know