
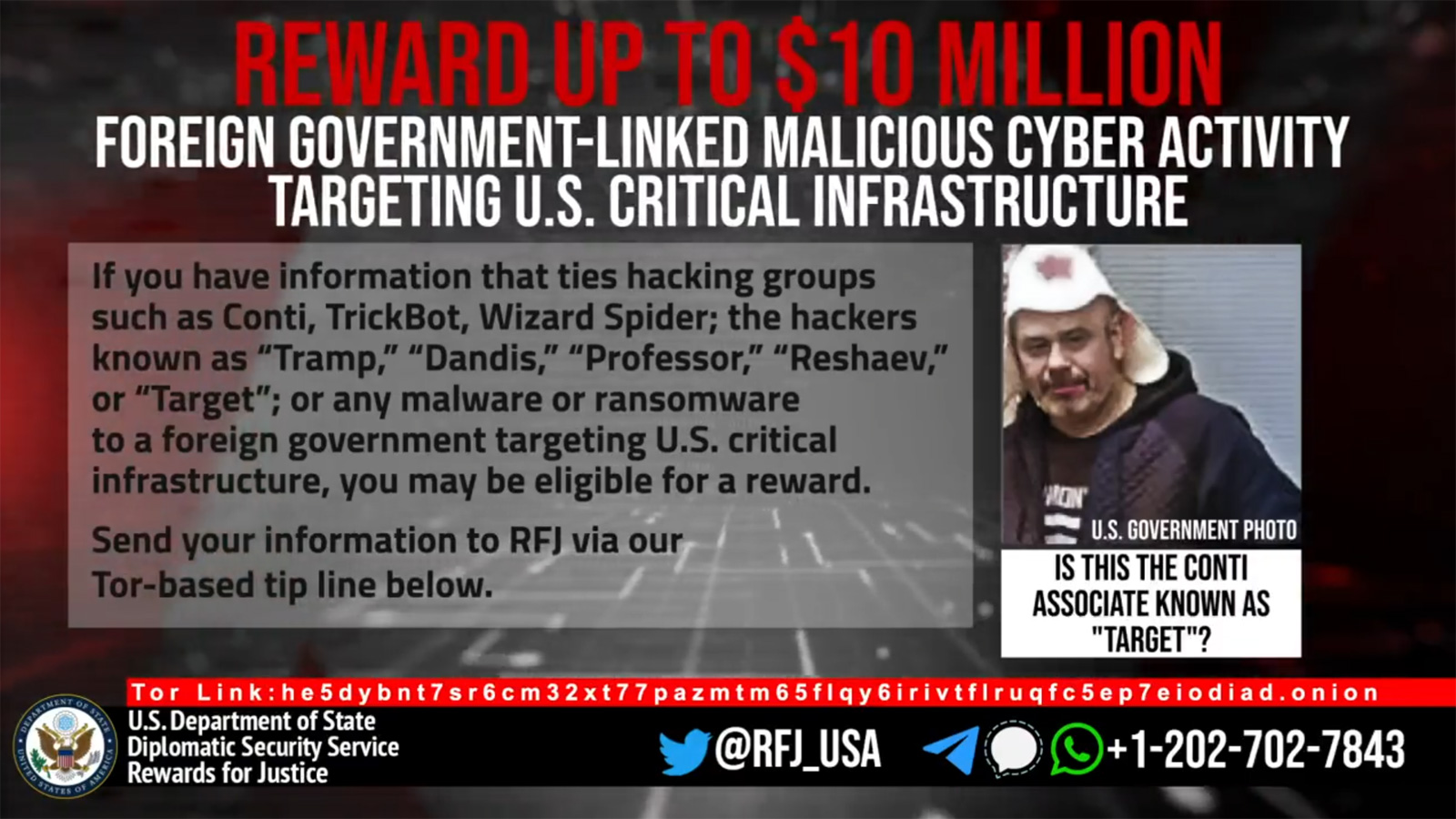
The U.S. State Department announced a $10 million reward today for information on five high-ranking Conti ransomware members, including showing the face of one of the members for the first time.
The Rewards of Justice program is a U.S. Department of State program where monetary rewards are offered for information related to threat actors affecting the national security of the USA.
Launched initially to gather information on terrorists targeting U.S. interests, the program has expanded to offer rewards for information on cyber criminals, such as the Russian Sandworm hackers, REvil ransomware, and the Evil Corp hacking group.
U.S. govt reveals the first face of a Conti member
Today, for the first time, the State Department revealed the face of a known Conti ransomware operator known as 'Target,' offering rewards of up to $10 million for information on him and four other members known as 'Tramp,' 'Dandis,' 'Professor,' and 'Reshaev.'
The Conti Ransomware is a notorious ransomware operation believed to be responsible for over 1,000 attacks worldwide and receiving ransom payments of over $150 million.
After rebranding from Ryuk to Conti in the summer of 2020, the ransomware gang quickly rose in prominence as they attacked high-profile victims, including City of Tulsa, Broward County Public Schools, Advantech, and Ireland's Health Service Executive (HSE) and Department of Health (DoH).
However, after siding with Russia over the invasion of Ukraine, a Ukrainian security researcher began leaking over 170,000 internal chat conversations between the Conti ransomware gang members and the source code for the Conti ransomware encryptor. Collectively this data breach is known as the 'Conti Leaks.'
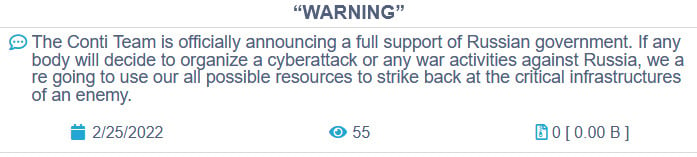
Source: BleepingComputer
This data breach not only led to the eventual shutdown of the Conti ransomware brand but the internal conversations also allowed cybersecurity researchers and law enforcement to quickly determine who was in charge of the operation and their responsibilities.
Some Conti members stood out as those who played a significant role in the operation and are now being targeted by the Rewards of Justice program.
AdvIntel CEO Vitali Kremez told BleepingComputer that the member targeted in today's announcement had the following roles in the Conti operation:
- Tramp is the owner/leader of the BlackBasta ransomware operation and previously one of the leaders of the Conti ransomware operation. He is also the owner and administrator of the Qbot malware command-and-control infrastructure and operation.
- Dandis is the technical manager and leader managing operators and pentesters for the ransomware operation.
- Professor is one of the Ryuk leaders responsible for the ransomware operation from a tactical level.
- Reshaev is the core leader/developer and operator of the Ryuk/Conti ransomware, staging the web builder for the payload and providing frontend and backend support for the ransomware operation.
- Target is the office manager and a team leader operating the "Ryuk/Conti" office. He was responsible for the physical operation of the cybercrime group. He is notable for having a law enforcement background.
While the Conti ransomware brand has shut down, the members are still fully active and operating in other ransomware operations and extortion groups.
Due to this, the Rewards for Justice program hopes to prevent future attacks by enticing people, including Russians who may recognize Target's picture, to submit tips for a million-dollar reward.
Wired, who first reported on the new rewards, says the State Department is looking for the members' physical locations and vacation and travel plans.
While Russia was not known to help the USA in their cyber investigations in the past, they are even less likely to do so now.
However, many of these threat actors might leave Russia to go on vacations, visit family, or for other reasons, where US allies can arrest them at the border.
To submit a tip, the State Department has set up a dedicated Tor SecureDrop server that can be used to submit information on the wanted Conti members anonymously.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now