
A nation-state threat actor known as 'Charming Kitten' (Phosphorus, TA453, APT35) has been observed deploying a previously unknown backdoor malware named 'Sponsor' against 34 companies around the globe.
One of the notable features of the Sponsor backdoor is that it hides its otherwise innocuous configuration files on the victim's disk so they can be discreetly deployed by malicious batch scripts, successfully evading detection.
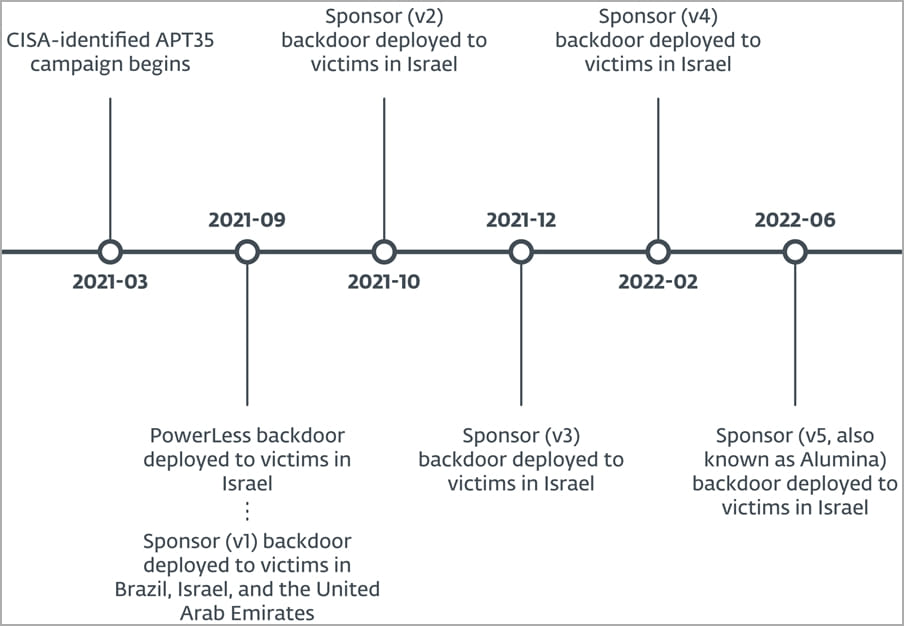
The campaign identified by ESET researchers spanned between March 2021 and June 2022, targeting government and healthcare orgs and firms engaged in financial services, engineering, manufacturing, technology, law, telecommunications, and more.
The most targeted countries in the campaign observed by ESET are Israel, Brazil, and the United Arab Emirates.
Targeting Microsoft Exchange flaws
ESET reports that Charming Kitten primarily exploited CVE-2021-26855, a Microsoft Exchange remote code execution vulnerability, to gain initial access to its targets' networks.
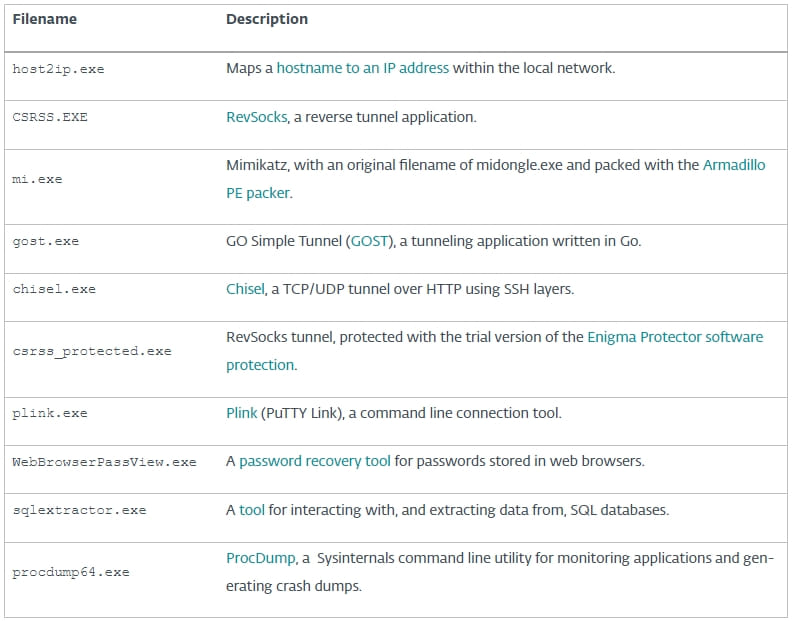
From there, the hackers used various open-source tools that facilitate data exfiltration, system monitoring, and network infiltration and also help the attackers maintain access to the compromised computers.
Before deploying the Sponsor backdoor, the final payload seen in these attacks, the hackers drop batch files on specific file paths on the host machine, which writes the required configuration files.
These files are named config.txt, node.txt, and error.txt to blend in with regular files and avoid raising suspicions.
The Sponsor backdoor
Sponsor is a C++ backdoor that creates a service upon launch as instructed by the configuration file, which also contains encrypted command and control (C2) server addresses, C2 contacting intervals, and the RC4 decryption key.
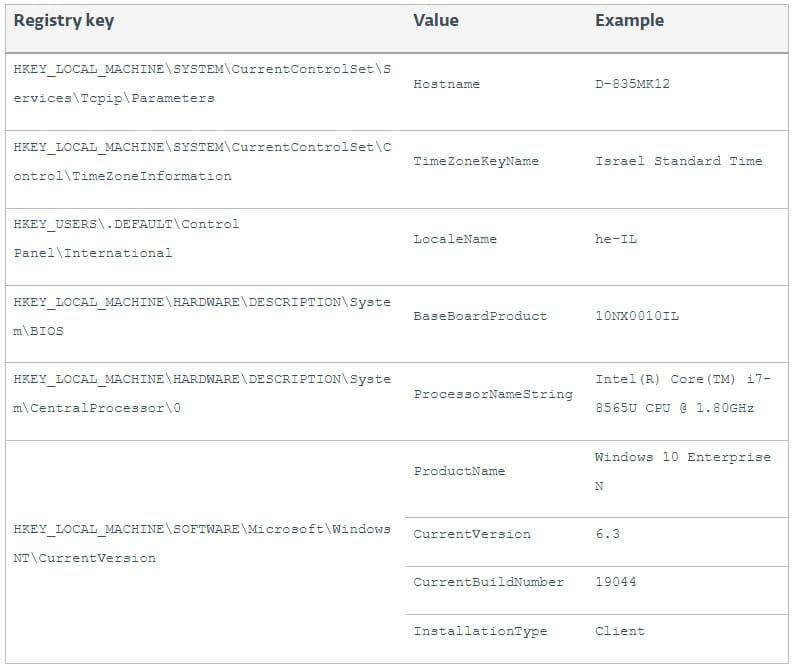
The malware gathers system information like the OS build (32 or 64-bit) power source (battery or plug) and sends it to the C2 via port 80, receiving a node ID back, which is written to the configuration file.
Next, the Sponsor backdoor enters a loop where it contacts the C2 in time intervals defined by the configuration file to acquire commands for execution on the host.
Here's a list of the supported commands:
- Sends running Sponsor process ID.
- Executes a specified command on Sponsor host and reports results to the C2 server.
- Receives and runs a file from C2 with various parameters and communicates success or errors to C2.
- Downloads and runs a file via Windows API and reports to C2.
- Runs Uninstall.bat from the current directory.
- Sleeps randomly before reconnecting with the C2 server.
- Updates C&Cs list in config.txt and reports to C2.
- Adjusts check-in interval in config.txt and reports to C2.
ESET has also seen a second version of Sponsor, which features code optimizations and a layer of disguise that makes it appear as an updater tool.
Although none of the IP addresses used in this campaign are online anymore, ESET has shared full IOCs to help defend against potential future threats that reuse some of the tools or infrastructure Charming Kitten deployed in that campaign.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now