
Update 4/5/25: ShadowServer says there are 16,000 exposed devices likely vulnerable to this flaw.
IT security software company Ivanti has released patches to fix multiple security vulnerabilities impacting its Connect Secure and Policy Secure gateways.
Unauthenticated attackers can exploit one of them, a high-severity flaw tracked as CVE-2024-21894, to gain remote code execution and trigger denial of service states on unpatched appliances in low-complexity attacks that don't require user interaction.
The vulnerability is caused by a heap overflow weakness in the IPSec component of all supported gateway versions.
While Ivanti said the remote code execution risks are limited to "certain conditions," the company didn't provide details on the vulnerable configurations.
"We are not aware of any customers being exploited by these vulnerabilities at the time of disclosure," Ivanti added.
Today, the company also patched three other security flaws, impacting the same products and exploitable by unauthenticated threat actors for DoS attacks:
- CVE-2024-22052: A null pointer dereference vulnerability in the IPSec component
- CVE-2024-22053: A heap overflow vulnerability in the IPSec component
- CVE-2024-22023: An XML entity expansion or XEE vulnerability in SAML component
Ivanti provides detailed instructions in this Knowledge Base Article on accessing and applying today's security patches.
Shodan, a search engine used to discover Internet-exposed services and devices, currently tracks over 29,000 Ivanti Connect Secure VPN gateways exposed online, while threat monitoring platform Shadowserver sees over 18,000.
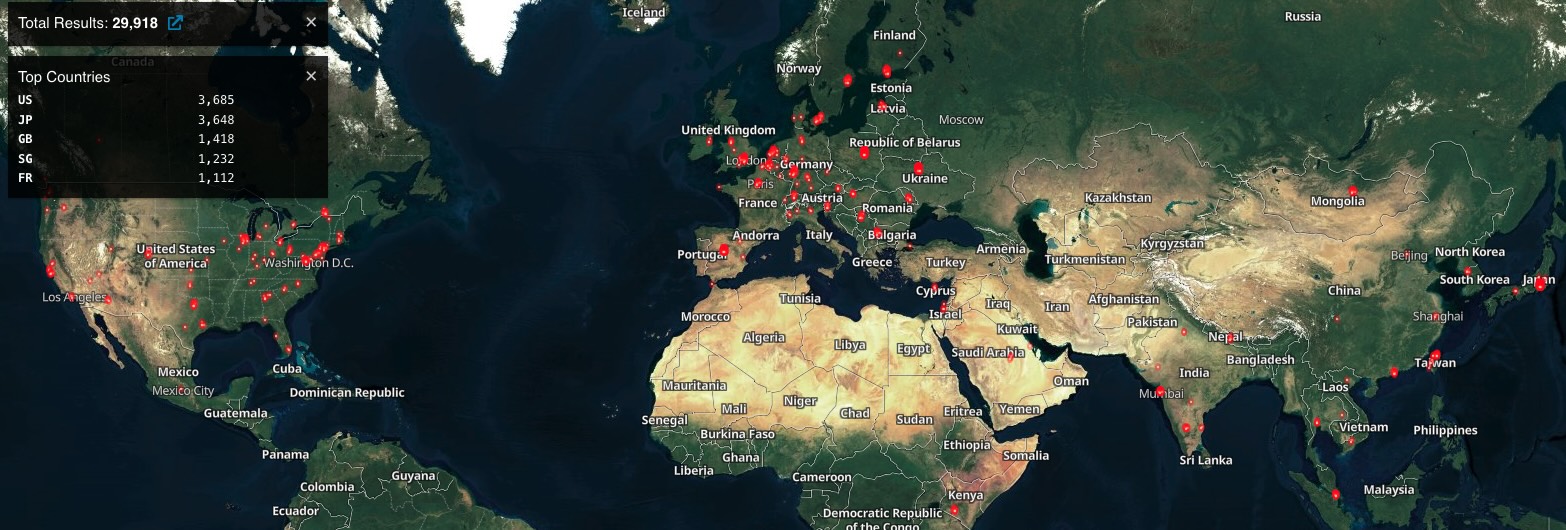
Nation-state actors have been exploiting multiple vulnerabilities in Ivanti software this year, and thousands of Ivanti Connect Secure and Policy Secure endpoints are still at risk.
These security vulnerabilities (i.e., CVE-2023-46805, CVE-2024-21887, CVE-2024-22024, and CVE-2024-21893) were used as zero-days before other attackers exploited them in widespread attacks to spread custom malware.
In response, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive to federal agencies ordering them to secure their Ivanti systems against attacks using the zero-day flaws.
The directive was later amended to require agencies to disconnect vulnerable Ivanti VPN appliances and rebuild them with patched software before bringing them back online.
Three years ago, suspected Chinese threat groups exploited another Connect Secure zero-day (CVE-2021-22893) to breach dozens of government, defense, and financial organizations across the United States and Europe.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now