
Criminal IP, a prominent Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently integrated with Cisco SecureX/XDR, empowering organizations to stay ahead of malicious actors by providing a comprehensive solution for threat intelligence and risk assessment.
In an era of ever-evolving cyber threats and vulnerabilities, this technical alliance is expected to be an essential safeguard, prioritizing threats, detecting malicious activity swiftly, and proactively mitigating potential risks.
Criminal IP as an Enrichment Tool in Threat Response
Cisco is a global leader in technology that delivers innovative software-defined networking, cloud, and security solutions, including secure access, vulnerability management, network segmentation, and threat response.
Its core product, Cisco SecureX, is a security platform with unified visibility and intuitive automation, allowing for robust threat detection, response, and recovery.
Source: Criminal IP
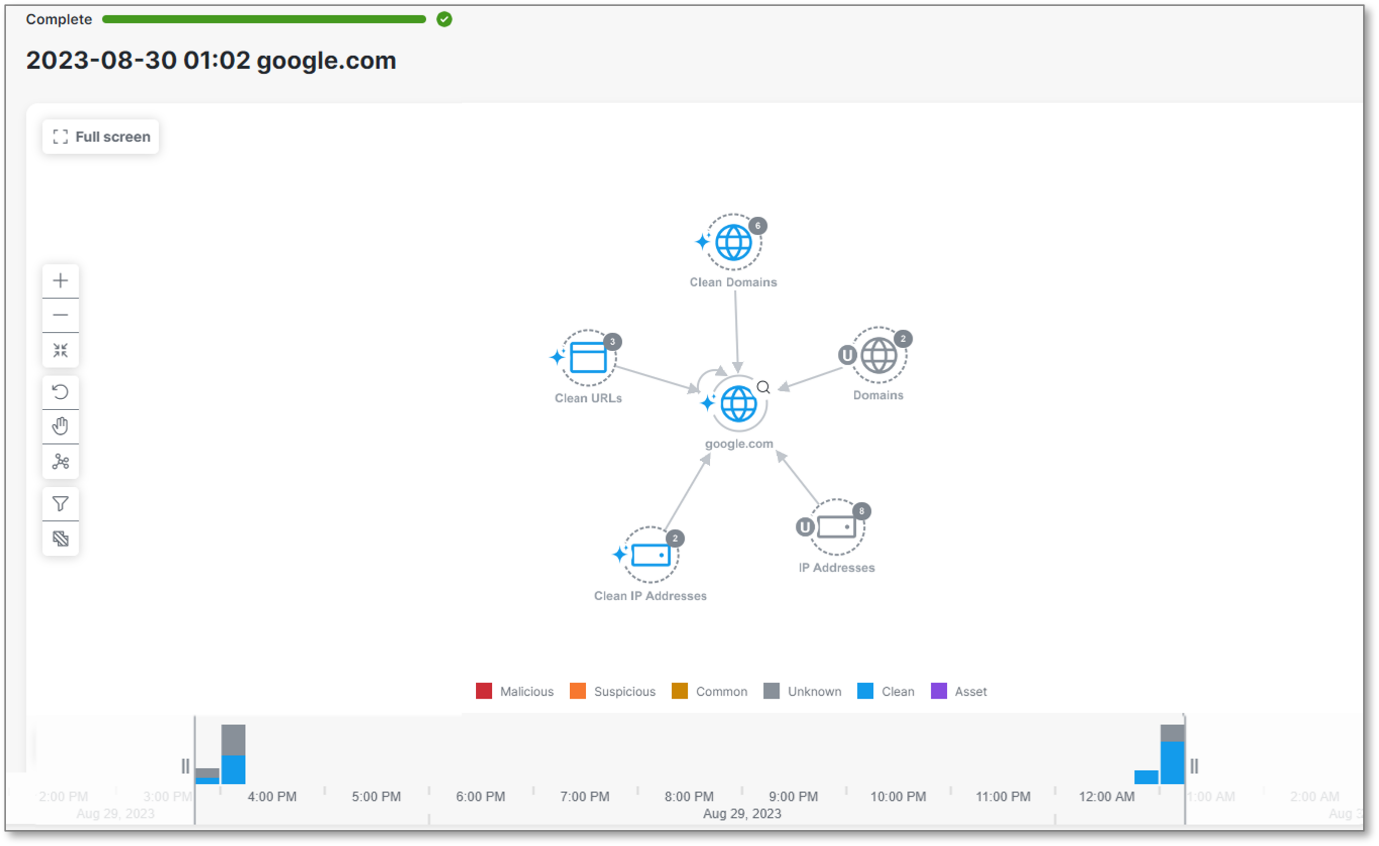
Criminal IP, a contributing tool in Cisco’s SecureX Threat Response and XDR, leverages threat intelligence to offer the latest data on all online assets. Users can directly investigate and assess risks through Criminal IP's API, with data displayed in a contextualized manner that facilitates the understanding of relationships between assets.
This integration is designed to enhance the security posture of the users’ networks, offering real-time insights and risk scoring for IP addresses and domains.
Source: Criminal IP
Comprehensive Threat Information Expertise from Criminal IP
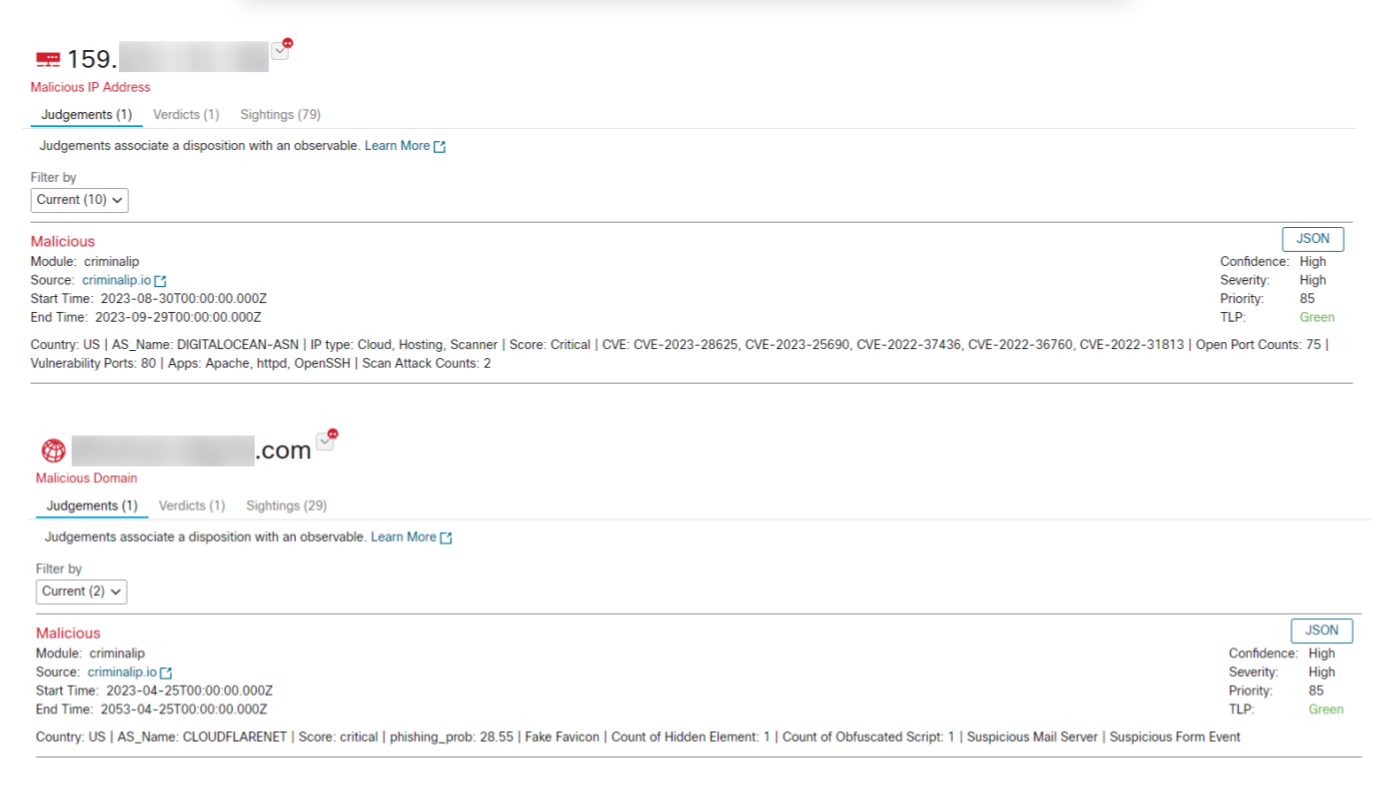
Key integration features of Criminal IP focus on providing critical information and analysis on IP addresses and domains. When utilizing the investigate search function in Cisco SecureX and XDR, users can uncover a summary of the threat information for the searched asset, gaining insight into the specific reasons it is identified as malicious.
Source: Criminal IP
Furthermore, clicking on the source unveils comprehensive search results within the Criminal IP UI. This encompasses details on open ports, Vulnerabilities and Exposures (CVEs), WHOIS data, connected domains in IP addresses, domain phishing scores, abuse history, and more.
This holistic perspective empowers cybersecurity professionals to adeptly prioritize and address potential threats.
The integration will soon be accessible to all XDR/SecureX users via the Integration Modules tab on the platforms. For those interested, you can request the integration code by contacting the support team at support@aispera.com.
About AI SPERA
AI SPERA launched its global cybersecurity service, Criminal IP on April 17, 2023, following a successful year-long beta phase. The company has established technical and business partnerships with acclaimed global security firms, including VirusTotal, Splunk, Anomali, LogRhythm, Datadog, and more.
Criminal IP presents a complete product line, including Criminal IP ASM (Enterprise Attack Surface Management Solution), Criminal IP FDS (Fraud Detection System), and Criminal IP SecOps (IP Address Threat Intelligence-Based Security Operations).
Offering compatibility with five languages (English, French, Arabic, Korean, and Japanese), the search engine provides a seamless service to all users worldwide.
Sponsored and written by Criminal IP.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now