
Attackers are hacking into poorly secured and Interned-exposed Microsoft SQL (MS-SQL) servers to deploy Trigona ransomware payloads and encrypt all files.
The MS-SQL servers are being breached via brute-force or dictionary attacks that take advantage of easy-to-guess account credentials.
After connecting to a server, the threat actors deploy malware dubbed CLR Shell by security researchers from South Korean cybersecurity firm AhnLab who spotted the attacks.
This malware is used for harvesting system information, altering the compromised account's configuration, and escalating privileges to LocalSystem by exploiting a vulnerability in the Windows Secondary Logon Service (which will be required to launch the ransomware as a service).
"CLR Shell is a type of CLR assembly malware that receives commands from threat actors and performs malicious behaviors, similarly to the WebShells of web servers," AhnLab says.
In the next stage, the attackers install and launch a dropper malware as the svcservice.exe service, which they use to launch the Trigona ransomware as svchost.exe.
They also configure the ransomware binary to automatically launch on each system restart via a Windows autorun key to ensure the systems will be encrypted even after a reboot.
Before encrypting the system and deploying ransom notes, the malware disables system recovery and deletes any Windows Volume Shadow copies, making recovery impossible without the decryption key.
First spotted in October 2022 by MalwareHunterTeam and analyzed by BleepingComputer, the Trigona ransomware operation is known for only accepting ransom payments in Monero cryptocurrency from victims worldwide.
Trigona encrypts all files on victims' devices except those in specific folders, including the Windows and Program Files directories. Before encryption, the gang also claims to steal sensitive documents that will get added to its dark web leak site.
Additionally, the ransomware renames encrypted files by adding the ._locked extension and embeds the encrypted decryption key, the campaign ID, and the victim ID (company name) in every locked file.
It also creates ransom notes named "how_to_decrypt.hta" in each folder with information about the attack, a link to the Trigona Tor negotiation website, and a link that contains the authorization key needed to log into the negotiation site.
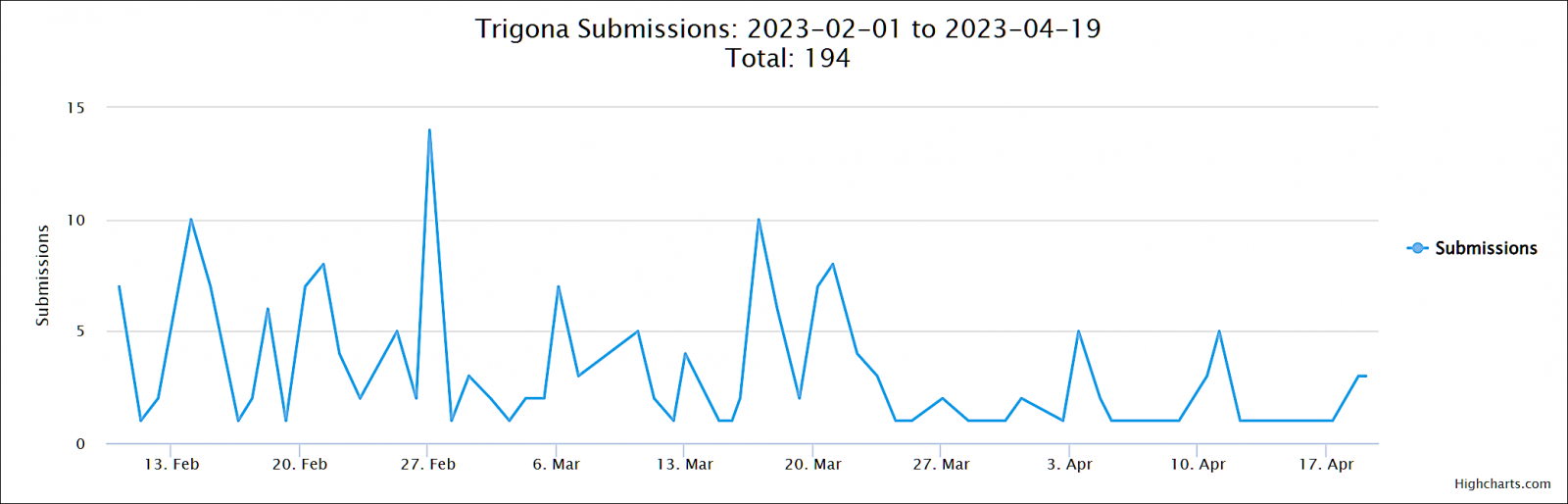
The Trigona ransomware gang has been behind a constant stream of attacks, with at least 190 submissions to the ID Ransomware platform since the start of the year.


Comments
Icepop33 - 1 year ago
It looks like Trigonagetu © (I'm open to negotiations of my own ;)
It's time to beef up those 20 year old crappy passwords.
11 char min, incl numbers, upper and lower case letters and punctuation to increase entropy.
Randomize or have software do a better job than you ever could.
Just like P@ssword1 is a shitty password, "I think I want to go to the beach today": is not a good passphrase, nor is "battery horse staple" at this point rofl.
Use 2FA when available.
Hope those websites with your financial info use easy methods to deter brute force attacks, something as simple as a lockout after several unsuccessful login attempts from the same IP or introducing a wait time of a few seconds after each attempt. This will make the bot sit and spin. This may not be good advice in the future as even a lowly scumbot getting "pissed off" could have repercussions for humanity. Right now they are happy to drop some virtual acid and "hallucinate". That gives us some breathing room.
If you use a manual password list, re-encrypt after each use. This take massive discipline and aversion to taking shortcuts. IOW, don't do it, unless you are more than human.
Use a password manager that stores the encrypted password vault locally, no cloud storage that can be compromised in tomorrow's article.
Put the master password in a safe or safe place.
If you're so inclined, you can even apply further cryptography. You can nest simple ciphers (of your own design) to increase their effectiveness. Hide the clues in different places.
The cloud would come in handy if you had a stroke or your safe wasn't that fireproof.or you need to login remotely.
Don't give anybody your password whom you don't trust with your testicles (or equivalent :).
Don''t reuse passwords across sites, not even once.
Hope this helps a bit.