Recent versions of the Cerber ransomware are behaving somewhat different from older variants, with the ransomware not deleting shadow volume copies, prioritizing specific folders and ignoring others.
This discovery comes via the Microsoft Malware Protection Center, who along with Heimdal Security picked up a series of Cerber distribution campaigns, via exploit kits and email spam.
The biggest change Cerber received is that the ransomware doesn't delete shadow volume copies anymore, opening the door for recovering at least a small number of files using special disk recovery software.
The reason why this happen is unknown, but this modification has been spotted only in recent variants, and it doesn't mean it won't be removed in a future version.
Cerber now encrypts certain files first
Additionally, recent Cerber variants have also started to prioritize certain folders when it comes to the encryption routine. As you can see from the folder paths below, a primer is on Office documents and Bitcoin data.
\excel\
\microsoft sql server\
\microsoft\excel\ (new)
\microsoft\microsoft sql server\
\microsoft\office\ (new)
\microsoft\onenote\ (new)
\microsoft\outlook\ (new)
\microsoft\powerpoint\ (new)
\microsoft\word\ (new)
\office\ (new)
\onenote\
\outlook\
\powerpoint\
\steam\
\the bat!\
\thunderbird\
\word\ (new)
Another change is that the list of exempt folders has also grown, as the Cerber crew decided it wasn't worth encrypting files in some of these locations:
\$recycle.bin\ (new)
\$windows.~bt\
\$windows.~ws\ (new)
\boot\
\documents and settings\all users\
\documents and settings\default user\
\documents and settings\localservice\
\documents and settings\networkservice\
\intel\ (new)
\msocache\ (new)
\perflogs\ (new)
\program files (x86)\
\program files\
\programdata\
\recovery\ (new)
\recycled\ (new)
\recycler\ (new)
\system volume information\ (new)
\temp\ (new)
\users\all users\
\windows.old\
\windows10upgrade\ (new)
\windows\
\winnt\ (new)
\appdata\local\
\appdata\locallow\
\appdata\roaming\ (made more generic)
\local settings\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Furthermore, Cerber has updated the list of files it targets for encryption. According to Microsoft, recent Cerber versions won't encrypt anymore the following file types:
.cmd
.com
.cpl
.dll
.exe
.hta
.msc
.msi
.msp
.pif
.scf
.scr
.sys
Despite removing some extensions, Cerber has also added 50 others, bringing up the ransomware's total to a whopping 493 extensions.
Other than these updates, Cerber is the same threat as before, still undecryptable. While Microsoft reports that the ransom screen appears to have changed because it now uses a red background highlight instead of green, this color choice change took place a few weeks back and was noted before.
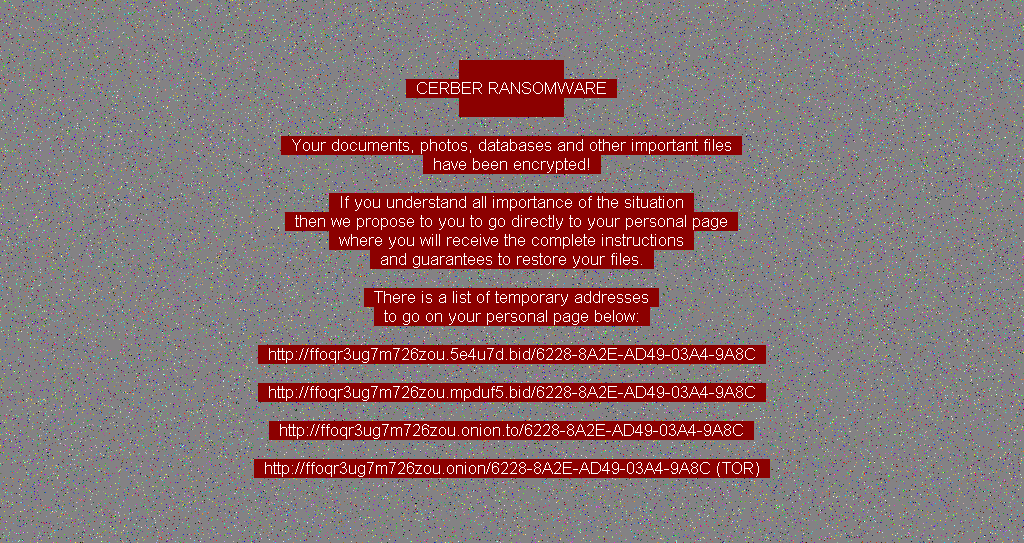
While most cyber-criminal malware operations have slowed down for the holiday season, the group behind Cerber appears is extremely busy, being currently engaged in different campaigns that leverage both spam floods and exploit kit activity.
According to reports from both Microsoft and Heimdal Security, the Cerber gang has been going strong this entire month, as we previously reported last week, when the Cerber gang was sending massive waves of spam peddling fake credit card reports.
Cerber delivered via exploit kits and Nemucod downloaders
One week later, Cerber campaigns are still active. According to Heimdal, the Cerber crew is using compromised websites.
These hacked websites are part of a bigger Pseudo Darkleech campaign, which uses a certain type of scripts injected on the compromised sites to redirect users to exploit kits that leverage Internet Explorer, Microsoft Edge, Flash Player and Silverlight exploits to infect the host with the Nemucod malware.
Nemucod, which is a generic first-stage downloader, will fetch the Cerber ransomware at a later point.
According to Heimdal Security, this campaign is currently passing undetected, with very low detection rates for the scanning engines listed on VirusTotal. The same low detection rate was also noted by MalwareHunterTeam.
Christmas came early for the Cerber guys.
— MalwareHunterTeam (@malwrhunterteam) December 23, 2016
2 of the 3 domains are already suspended.
The 3rd is still alive, and gives samples at 2/56. pic.twitter.com/ge7SdGNy3F
Cerber delivered via Flash exploit served via RIG exploit kit
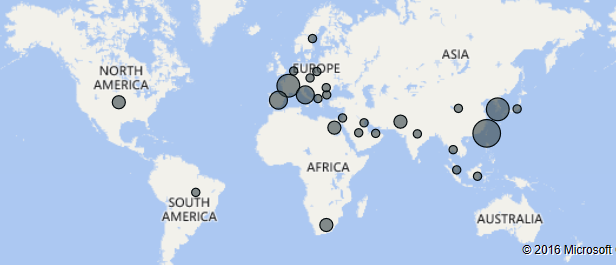
Similarly, the Microsoft Malware Protection Center is also reporting on another Cerber distribution campaign that leverages exploit kits. According to the Microsoft crew, the Cerber gang is using the RIG exploit kit to take advantage of the CVE-2015-8651 vulnerability in unpatched Adobe Flash Player installations.
This flaw allows the crooks to automatically install and run the Cerber ransomware. According to Microsoft, this latter campaign has made a lot of victims in Europe and Asia.
Cerber delivered via email spam
Besides these two very active distribution campaigns that leverage exploit kits, the Cerber gang is also relying on the classic method of email spam.
While last week the Cerber crew was using fake credit card reports to lure victims into downloading and opening malicious email attachments, this week they've returned to the classic theme of order deliveries.
Just like last week, the email attachment comes protected by a password, with the file's password listed in the email body itself. The reason for this is to avoid some security scanners that can't see through the password-protected file.
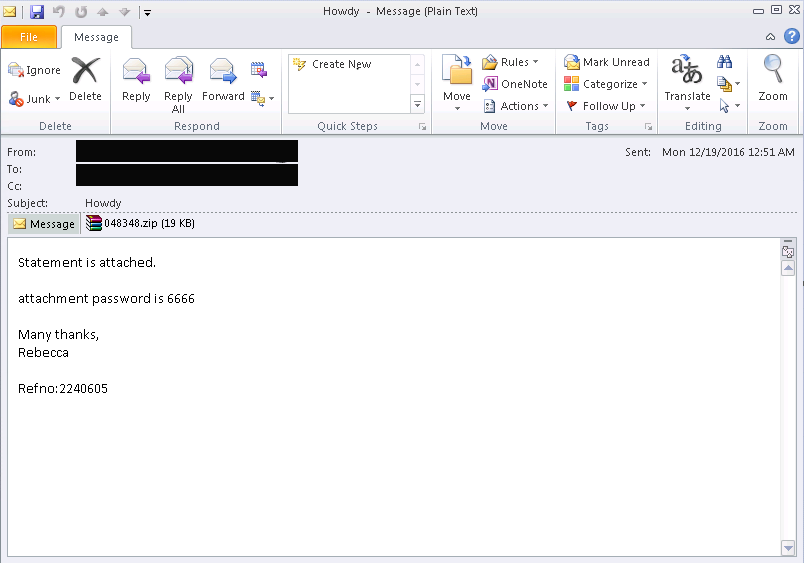
The file attachment users receive via the spam emails is your typical macro-malware, a Word file that asks users to allow a malicious macro script to execute. If allowed to run, the macro script downloads and installs the Cerber ransomware.
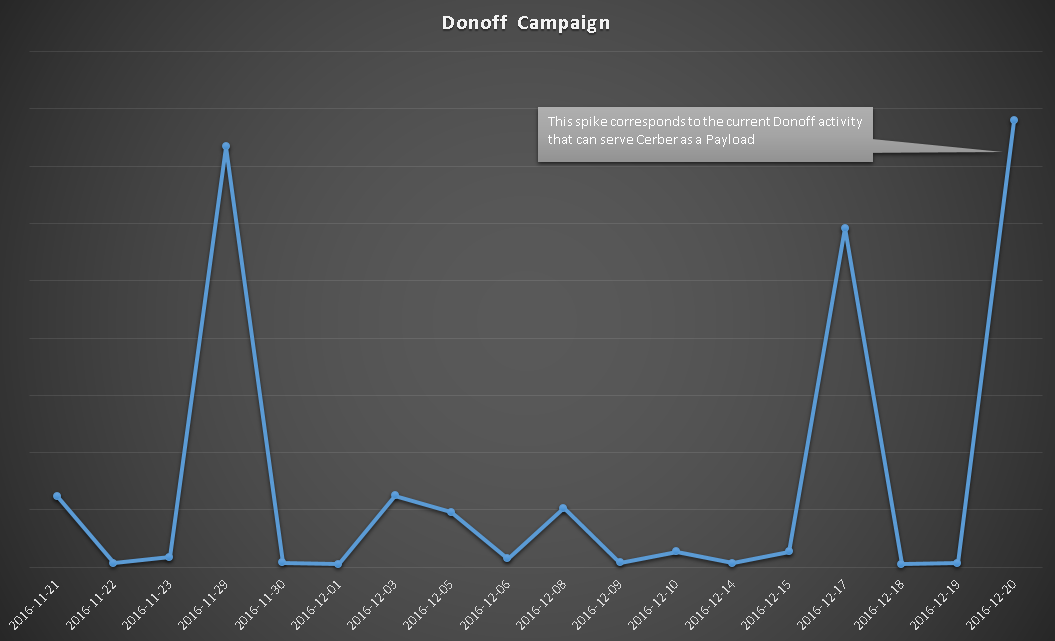
According to Microsoft, this campaign (tracked as Donoff) has seen a huge rise in numbers during the past few days.
Yet again, we are shown why it's so important that security firms keep a constant eye on ransomware families, as they tend to evolve quite rapidly.
Tracking Cerber's evolution may provide clues about its author, its coding style, upcoming features, and possible hints toward creating a decryptor.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now