DMA Locker is a new ransomware that was discovered last week by PhysicalDrive0 and analyzed by Malwarebytes malware analyst Hasherezade. This ransomware encrypts your data using AES encryption and then demands 4 bitcoins to receive your decryption key. Earlier versions were decryptable due to a flaw in the program, but newer versions have resolved this issue. DMA Locker includes some interesting features including the encryption of unmapped network shares and the targeting of any file that does not reside in a particular folder and or does not have a particular extensions.
DMA Locker targets unmapped network shares
One feature of DMA Locker, which has not been mentioned yet, is that it also has the ability to enumerate and encrypt data on unmapped network shares. This is not a feature we see too often in current ransomware infections even though it is not a complex feature to add. It should be expected that this will become standard for ransomware in the future, so system administrators should make sure all network shares are running at the most reduced set of file permissions that work for their environment.
The Encryption Process
Unlike most ransomware, when DMA Locker encrypts your data it does not target particular extensions to encrypt, but rather uses a white list of folders and extensions that it will not encrypt. Therefore, this ransomware will encrypt almost all non-system and non-executable related files that it finds on your system.
Folders and extensions that are white listed from being encrypted are:
\Windows\,\Program Files\,\Program Files (x86)\,Games,\Temp,\Sample Pictures,\Sample Music,\cache
.exe,.msi,.dll,.pif,.scr,.sys,.msp.com,.lnk,.hta,.cpl,.msc,.bat,.cmd
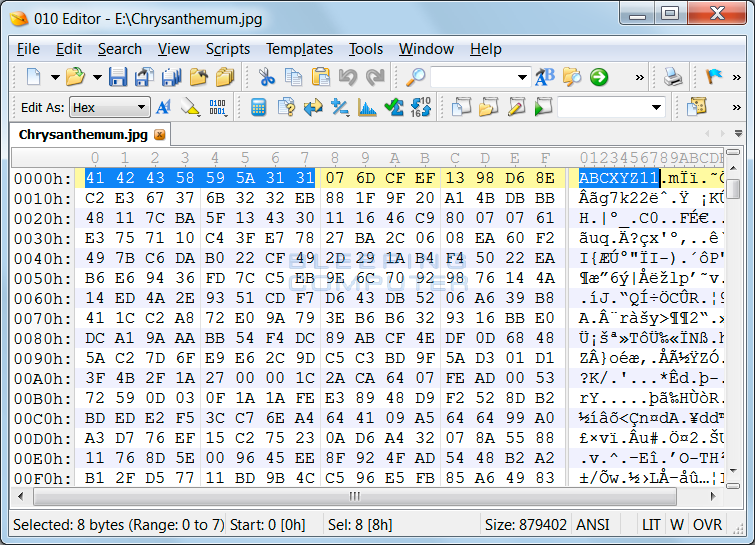
DMA Locker uses the AES encryption algorithm when encrypting your files, but will not add a custom extension to an encrypted file. Instead, DMA Locker will add an identifier into the header of every encrypted file so that DMA Locker can identify it as a file it encrypted. An example of an encrypted file with the highlighted identifier can be seen below.
Finally, when DMA Locker has finished encrypting your data, it will show you the lock screen where you can see instructions on how to pay the ransom and decrypt your files. This ransom information will also be saved in the C:\ProgramData\cryptinfo.txt and shown every time you login into the computer.
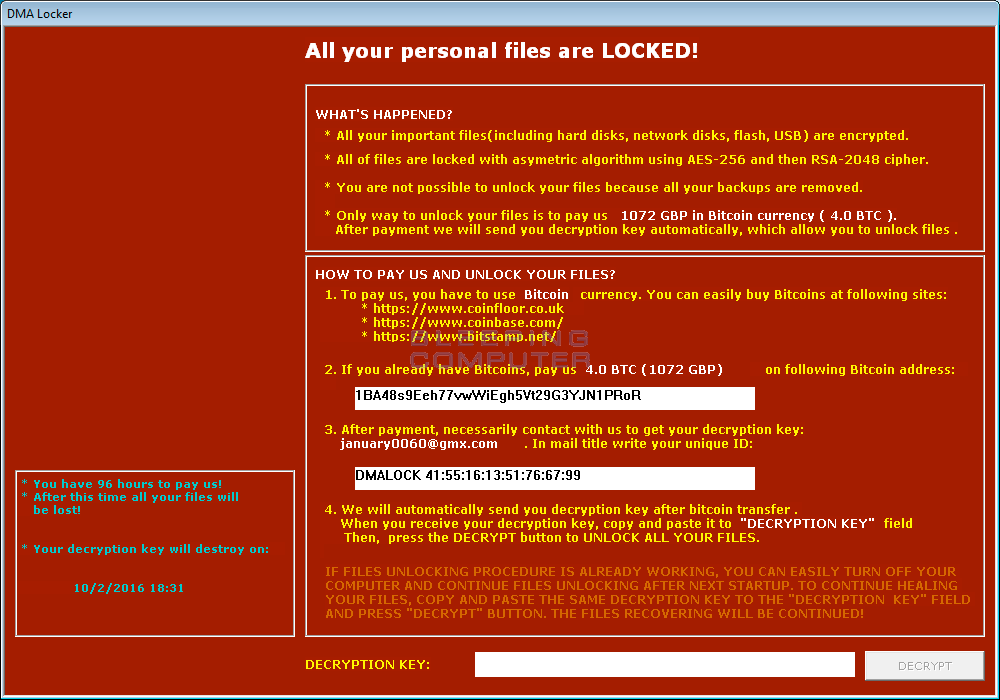
As DMA Locker uses a static bitcoin payment address of 1BA48s9Eeh77vwWiEgh5Vt29G3YJN1PRoR we are able to monitor how many ransom payments have been made. Unfortunately, at this time it appears that 5 victims have paid the ransom.
Protecting yourself from DMA Locker
Other than normal antivirus protection, you can also use a trick discovered by Hasherezade that causes DMA Locker not to encrypt any files on your desktop. When DMA Locker encrypts your computer it will also create two files that indicate that the program finished the encryption process. This way when it starts again, it does not encrypt your data a second time.
To trick DMA Locker into thinking your computer is already encrypted, you can create the following two files. It does not matter what these files contain, only that they exist, in order to trick DMA Locker into not encrypting your data.
C:\ProgramData\decrypting.txt
C:\ProgramData\start.txt
C:\Documents and Settings\All Users\decrypting.txt
C:\Documents and Settings\All Users\start.txt
DMA Locker Decrypted
If you are infected with earlier versions of DMA Locker, especially ones that contain the ID 41:55:16:13:51:76:67:99, it may be possible to decrypt them using a decrypter created by Fabian Wosar of Emsisoft. To see if your version is compatible with the decrypter, simple download download decrypt_DMA Locker.exe from the following link and save it on your desktop:
Decrypt DMA Locker Download
Once you have downloaded the executable, double-click on it to launch the program. When the program starts, you will be presented with a UAC prompt as shown below. Please click on Yes button to proceed.
You will then be presented with a license agreement that you must click on Yes to continue. You will now see the main DMA Locker Decrypter screen.
To test the decryption against a fiew files in a particular folder, you can click on the Clear objects button and then add the folder you wish to test with. If the tool can decrypt the folder, simply clear objects again and add the drives you wish to decrypt and then click on the Decrypt button. Once you click Decrypt, DMA Locker Decrypter will decrypt all the encrypted files and display the decryption status in a results screen like the one below.
Most of your files should now be decrypted. If you need any help using this tool, you can ask in the DMA Locker Ransomware Support Topic.
Files related to DMA Locker
C:\ProgramData\cryptinfo.txt
C:\ProgramData\date_1.txt
C:\ProgramData\decrypting.txt
C:\ProgramData\ntserver.exe
C:\ProgramData\start.txt
Registry entries related to DMA Locker
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\cryptedinfo notepad c:\ProgramData\cryptinfo.txt
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\cssys C:\ProgramData\ntserver.exe


Comments
craiggc - 8 years ago
how does this propagate and how can we block / prevent this from reaching our users ?
Lawrence Abrams - 8 years ago
Unfortunately, I am not aware at this time as to how it is being distributed.
shemone - 8 years ago
This decryption software just saved a site we've been trying to recover.
They were hit on the 29th by an attack from a compromised domain admin account, the attack came in via RDP from an unknown external IP,firstly the attacker encrypted all the data on the server using DMALocker, then proceeded to delete all backups locally and the ones stored on an internal NAS and let's just say off-site were not an option.
We've spent a week trying various methods of recovery, including deep recovery software - this proved fruitless as the attacker had ran Eraser on the server just after the encryption meaning everything we recovered was just nonsense data.
I figures I'd do a quick google today to see if DMA had started making the rounds and low and behold I found this link, after downloading the decrypter and running it we've been able to decrypt the TB or so of files.
Needless to say all account passwords have been changed and the client is now a little more interested in maintaining an offsite backup, thanks for the save.
thisisnotgood - 8 years ago
A client of ours Backup user with domain admin rights was compromised by this. We found that as soon as the backup ran, so did the virus. Unfortunately we hadn't discovered this until it hit for a second time,. We used ERARemover, which finds the culprit virus more or less immediately.
Once discovered we started off by disabling the compromised user, but have removed it completely including it's profile now. And obviously changed passwords on all Admin accounts just to make sure. We checked all important groups that grant higher rights just to make sure no other accounts had been created.
Interesting to note that the first time around the file ntserver.exe was used, the second time they were hit, the file was different. It became a svchosd.exe, I guess in an another attempt to look genuine. I haven't seen any mention of that second file anywhere so thought I'd mention it for anyone suspecting. It's found in program data just like the ntserver.exe
The client have recovered from backups twice so all is well, however I wish I'd discovered this article sooner so I could have tested the EMSISoft decrypter. This happened prior to this articles release though, so go figure.
I also suspect RDP being the reason for the compromise in the first place. Temporarily stopped all connections on RDP ports to investigate a little further.
Fuzzalina - 8 years ago
I just got this. Is there an updated version of the Decrypter? The one I downloaded here doesn't work.