|
|
|
ListCWall Download | |
|---|---|
| Author: | BleepingComputer |
| License: | Free |
| Operating System: | Windows XP/Vista/7/8 32-bit program. Can run on both a 32-bit and 64-bit OS. |
| Version: | 1.3 |
| File Size: | 447 KBs |
| Downloads: | 99,775 |
| Last Updated: | 11/15/18 02:40:12 AM EST |
Screenshots for ListCWall
BleepingComputer Review:
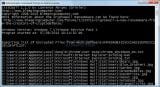
ListCWall, or ListCryptoWall, is a small utility that can be used to export and backup the list of files encrypted by the CryptoWall ransomware infection. When CryptoWall infects your computer it will encrypt your data and store a list of these encrypted files in your Windows Registry. ListCWall will export a sorted list of infected files into a text file so that you can easily find affected files.
Using ListCWall is easy. Simply download the program to a location on your hard drive and double-click on it. Once started, ListCWall will scan the Windows Registry for the registry key associated with CryptoWall. If one is found it will export the list of encrypted files to a log file named ListCWall.txt that will be located on your Windows desktop. You can then use this file to learn what files have been encrypted and then attempt to restore them from backups or using other methods.
In the ListCwall.txt log we will also include the Username and ComputerName of the PC that the list of encrypted files was exported from. This allows you to use ListCwall in login scripts to find the computer that has the CryptoWall infection.
Advanced Usage:
There are some more advanced features that are useful for consultants and an enterprise environment. These commands should be used from an Elevated Command Prompt.
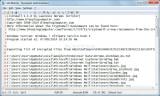
The first feature is the -q flag, which suppresses most output from the program. This allows you to use ListCwall as part of a domain login script to find the CryptoWall infected computer and export the list of files from it.
ListCwall also includes the ability to backup all of the encrypted files to a default folder of %Desktop%\ListCWall_Backup or to a user specified folder. When backing up files you can use either the -C flag, which will copy the encrypted files, or the -M flag which will move them. It is also possible to specify a specific folder that you wish to backup to using the -b
Last, but not least, the ListCwall logs will contain the username and computername where the program was run. This will make it easier for domain administrators to find the computer that has been infected with Cryptowall.
For a full list of command-line arguments, you can use the -h flag.