
Orqa, a maker of First Person View (FPV) drone racing goggles, claims that a contractor introduced code into its devices' firmware that acted as a time bomb designed to brick them.
On early Saturday, Orqa started receiving reports from customers surprised to see their FPV.One V1 goggles enter bootloader mode and become unusable.
"We first started getting the reports from our pilots in Japan, very early in the morning while we were all still asleep (or partying -- it was Friday after all!). Then in the early morning hours here in Europe, we started getting reports from a race event in Turkey," the company said.
The company revealed hours after devices began getting bricked when powered up, the issue resulted from a firmware bug "caused by the date/time feature."
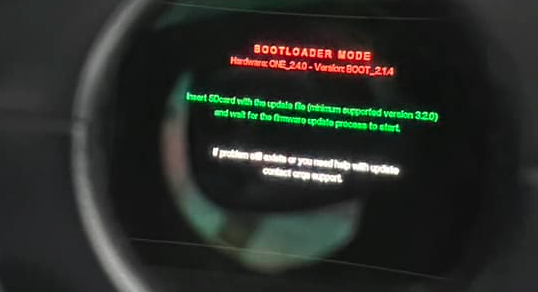
"Within 5 or 6 hours into this crisis, Saturday early afternoon, we found that this mysterious issue was a result of a ransomware time-bomb, which was secretly planted a few years ago in our bootloader by a greedy former contractor, with an intention to extract exorbitant ransom from the Company," Orqa said.
"The perpetrator was particularly perfidious, because he kept occasional business relations with us over these last few years, as he was waiting for the code-bomb to 'detonate', presumably so as not to raise suspicion and hoping that he will be able to extract more ransom as our business and our market share grew."
Orqa says the contractor behind the so-called "ransomware time-bomb attack" has allegedly posted an "unauthorised binary file" that should purportedly address the bug bricking FPV.One goggles since Saturday morning.
However, the company warned customers not to install unofficial firmware, and four hours ago, it added that an official version addressing the issue is now being tested with the help of a small number of beta testers.
"Since the perpetrator has gone public with what he did and posted what we fear is another compromised piece of firmware, we decided it is in our users' interest to be made aware of the situation and warned about the risks of installing a likely compromised firmware on their devices."
"In addition to that, our security review has found that only a fraction of the code was affected by this malware, and fixes are being done as we speak."
The fixed firmware is expected to be available until the end of the day after the new version is deemed safe for public release.
An Orqa spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today.
H/T Brett Callow


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now