
Attackers are now using encrypted RPMSG attachments sent via compromised Microsoft 365 accounts to steal Microsoft credentials in targeted phishing attacks designed to evade detection by email security gateways.
RPMSG files (also known as restricted permission message files) are encrypted email message attachments created using Microsoft's Rights Management Services (RMS) and offer an extra layer of protection to sensitive info by restricting access to authorized recipients.
Recipients who want to read them must authenticate using their Microsoft account or obtain a one-time passcode to decrypt the contents.
As Trustwave recently discovered, RPMSG's authentication requirements are now being exploited to trick targets into handing over their Microsoft credentials using fake login forms.
"It starts with an email that originated from a compromised Microsoft 365 account, in this case from Talus Pay, a payments processing company," Trustwave said.
"The recipients were users in the billing department of the recipient company. The message shows a Microsoft encrypted message."
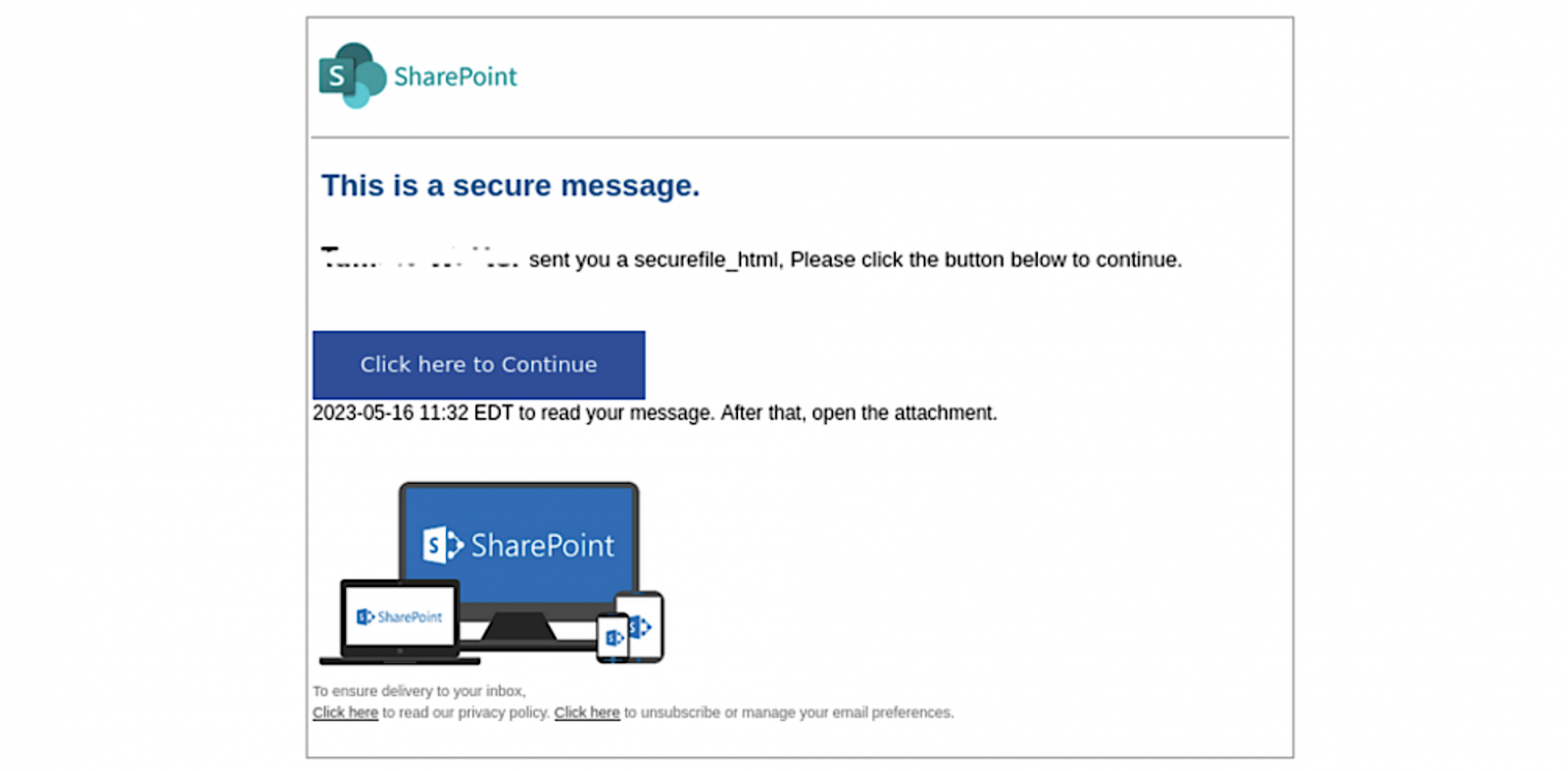
The threat actors' emails ask the targets to click a "Read the message" button to decrypt and open the protected message, redirecting them to an Office 365 webpage with a request to sign into their Microsoft account.
After authentication using this legitimate Microsoft service, the recipients can finally see the attackers' phishing email that will send them to a fake SharePoint document hosted on Adobe's InDesign service after clicking a "Click here to Continue" button.
From there, clicking "Click Here to View Document" leads to the final destination that displays an empty page and a "Loading...Wait" message in the title bar that acts as a decoy to allow a malicious script to collect various system information.
The harvested data includes visitor ID, connect token and hash, video card renderer information, system language, device memory, hardware concurrency, installed browser plugins, browser window details, and OS architecture.
Once the script is done collecting the targets' data, the page will show a cloned Microsoft 365 login form that will send the entered usernames and passwords to attacker-controlled servers.
Detecting and countering such phishing attacks can prove quite challenging due to their low volume and targeted nature, as observed by Trustwave researchers.
Moreover, the attackers' use of trusted cloud services such as Microsoft and Adobe to send phishing emails and host content adds an additional layer of complexity and trustworthiness.
Encrypted RPMSG attachments also conceal phishing messages from email scanning gateways, given that the only hyperlink in the initial phishing email directs the potential victims to a legitimate Microsoft service.
"Educate your users on the nature of the threat, and not to attempt to decrypt or unlock unexpected messages from outside sources," Trustwave advises companies that want to mitigate the risks posed by this type of phishing attack.
"To help prevent Microsoft 365 accounts being compromised, enable Multi-Factor Authentication (MFA)."


Comments
lwlopez1 - 10 months ago
So I have a question here. My client and I know not to put in credentials when asked. (Phished denied). But this threat came through very differently than anything I have ever seen(I have 40 years of looking and threats back before McAfee was free or even existed). The client was logged into a browser as Global Exchange Admin, they were also reading their email when a threat came across. The threat was inspected by the client and it launched IRM (Information Rights Management). It never prompted with the request for credentials. WTF. We don't know if the account was compromised, but we took the normal lock down precautions. What just happened? Looks like the link launched a IRM program or DLL without a prompt. This looks like the older days of CHM (Microsoft Help), Media Player, Java, ActiveX type launches. Google had that capability long ago without API permission to install when putting on Chrome. Also, when the message was received, it contained the recipient's email in the hard link. When the message forwarded to the next person, the link was auto-generated with the destination's email address hard linked to the forwarded recipient. Anyone? Bueller? When I say anyone, please no junk comments like "maybe you should check your computer or scan for a virus or fake scanner ads" Only people that actually know this bug intimately.
CeeBee71 - 10 months ago
Sounds like your client may have been targeted by someone trying to exploit CVE-2023-23397. Requires no user interaction; doesn't even require the message to be read, only delivered. Maybe I'm paranoid but that's my two cents.
https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-outlook-zero-day-used-by-russian-hackers-since-april-2022/
https://www.microsoft.com/en-us/security/blog/2023/03/24/guidance-for-investigating-attacks-using-cve-2023-23397/#:~:text=CVE%2D2023%2D23397%20is%20a,crafted%20message%20to%20a%20user.
y0ssarian69 - 10 months ago
I think what is happening is that your microsoft credentials can be cached, leading to auto opening the encrypted message. But user would still need to click on phishing links within.