CryptoSearch

CryptoSearch (beta) is a program I have created to help find what files were encrypted by a particular ransomware, and allow the user to copy/move the files to another location for archiving (for hopes of future decryption).
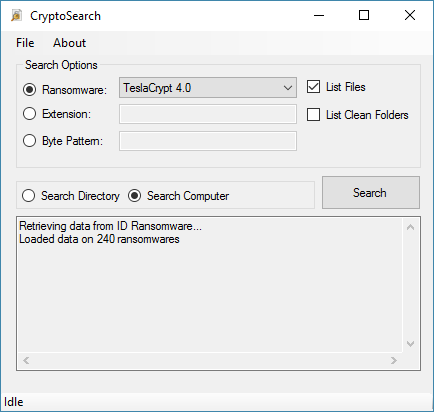
This program is powered by my service ID Ransomware, and thus is always updated with definitions on the latest known ransomwares and their signatures. This also allows it to be flexible in detecting the encrypted files, as it uses the exact same data ID Ransomware uses for identifying variants. It will identify files by known filename pattern or extension, or for some variants, the hex pattern in the encrypted file.
When CryptoSearch is first launched, it will contact the website, and pull down the latest information on known extensions and byte patterns; this is the only network activity done with the program, and no information about your system is uploaded or stored at all. If you have a network issue with reaching the website, the "Refresh Network" button is available to try again.
As of v0.9.2.0, CryptoSearch will save the definitions it uses to a local file in the same directory as the program. The next time you run the program, it will load this file for offline use if it cannot reach ID Ransomware. This will allow you to use it on a computer that has been quarantined and is offline.
You may also use the tool to manually search for a particular extension or byte pattern by use of the Search Options.
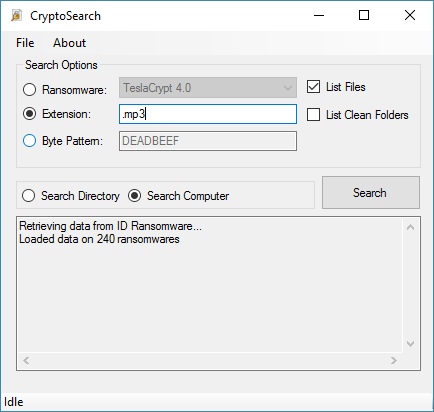
The following options are also available via the checkboxes on the right, and the radio buttons next to Search:
- List Files - lists the encrypted files, uncheck to only list folders that include encrypted files
- List Clean folders - will also list folders that are clean and do not have encrypted files
- Search Directory - search a specified directory
- Search Computer - search the whole computer (all drive letters found, including mapped drives)
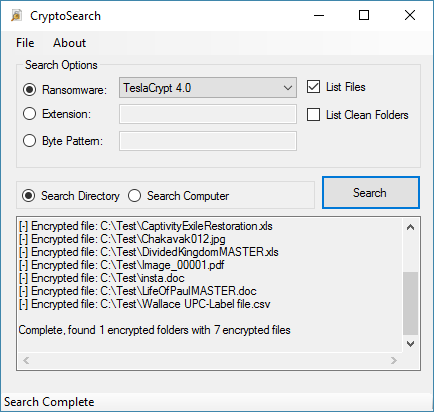
Once the scan has completed, the File menu will allow the following options:
- Export List - saves a list of the encrypted files to a text file
- Archive Files - allows you to copy or move the encrypted files to another location for archiving
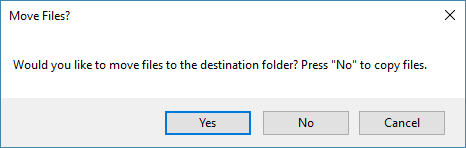
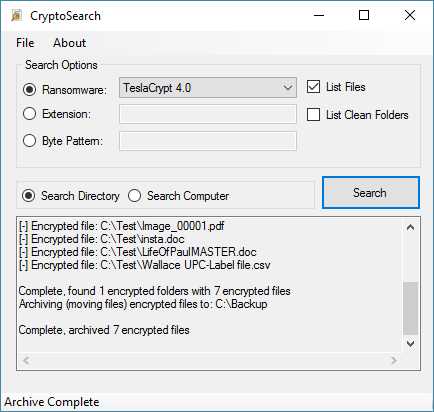
The archived files retain the full folder structure, including the drive letter. For example, these files were moved to "C:\Backup\C\Test".
Please note that this program does not decrypt data. It is simply a tool for users to find exactly what files were encrypted, and optionally move them to another location before cleaning or formatting a system.
You may download CryptoSearch here: https://download.bleepingcomputer.com/demonslay335/CryptoSearch.zip
Please note, the password for the zip file is "false-positive". This is a temporary response to false positives being triggered by Google SafeBrowsing and antivirus.
Please let me know if you run into any issues, or any recommendations for the program. I hope it is of some use to helping victims cleanup their systems, and for sysadmins to determine the extent of damages on servers (my original inspiration for this project). ![]()
Edited by Demonslay335, 17 January 2017 - 06:46 PM.







 Back to top
Back to top
















