How to crack your encrypted files yourself
For those who wish to try decrypting their own files, you can download TeslaDecoder and follow the instructions that are included in the download yourself. If you have a decent computer, then this is definitely the suggested method.
Instructions in Italian can be found here.
How to ask for help decrypting files encrypted by TeslaCrypt:
In order to request someone decrypt your files for you, you will need to register and validate a free account before you can reply to this topic.
Once you are registered, create a new reply to this topic requesting help. When creating the reply you should make sure you do the following steps.
Step 1: Start a Reply to this Topic
Click on the Reply to this Topic button and type in a request for help. Do not post the reply yet until you have followed all of the steps below.
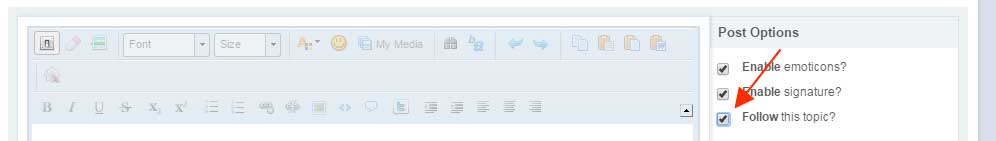
Step 2: Check the Follow Topic Option
Be sure to put a checkmark in the Follow Topic checkbox as indicated by the image below so that you receive notifications when someone replies to this topic.
Optional Step 3: Share and include a link to an encrypted file.
If you include a link in your reply to an encrypted file it will make it easier for a volunteer to help you and thus you will receive help quicker. It is suggested that you only publicly share a link to a file that contains no personal information. A good candidate for a generic non-personal image are the files located in C:\Users\Public\Pictures\Sample Pictures folder.
If you have encrypted files there, or other non-personal files, you can share a link to a encrypted file by uploading it to SendSpace. When the file has been uploaded, you will be shown a screen stating that the upload was succesful as shown below.
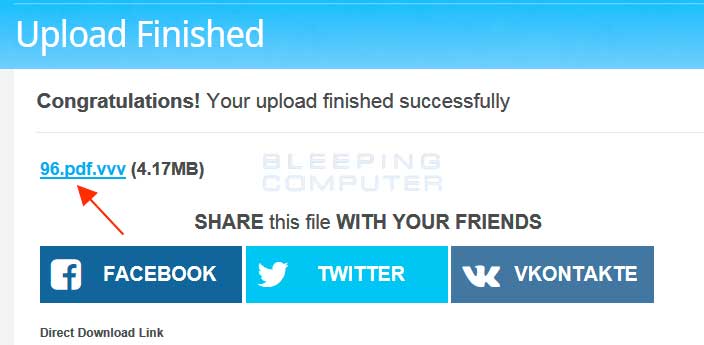
The filename link is indicated by the red arrow in the image above.
Now right click on the filename link and select Copy Shortcut as shown in the image below.
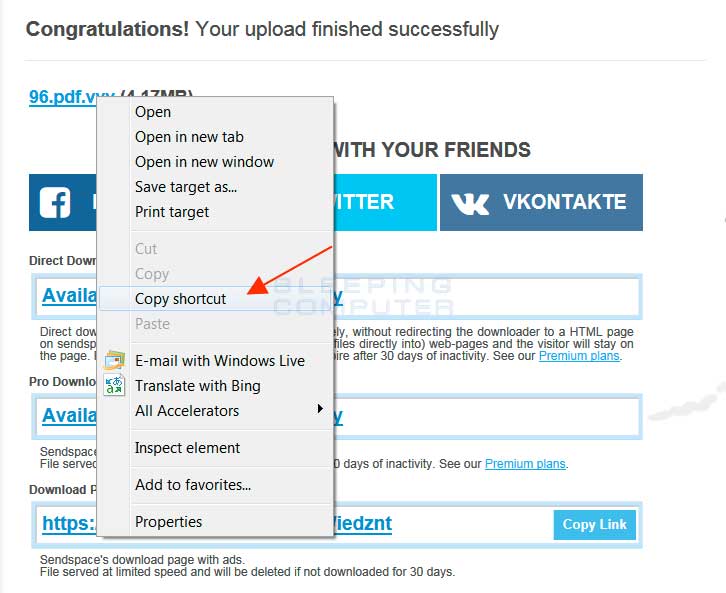
The shortcut you just copied should then be pasted into your reply requesting help.
Step 4: Post your topic and wait for a reply
When you have finished all of these steps, please click on the Add Reply button to post your request for help. Please remember that everyone who helps here is a volunteer, so please be patient while someone gets back to you. As always you can attempt to crack the file yourself by following the instructions in the TeslaDecoder file.




 Back to top
Back to top














