The new DeadBolt ransomware is targeting QNAP devices and appending the .deadbolt extension to encrypted file's names.
The ransomware is also hijacking the QNAP login screen to display a ransom note demanding 0.03 bitcoins, worth approximately $1,100.
Each victim receives a unique bitcoin address and there is no confirmation that paying a ransom will provide a decryption key.
Update 1/26/22: Below is new information received from victims and by analyzing a sample of the ransomware shared with BleepingComputer.
When a QNAP device is compromised a random named file will be created at /mnt/HDA_ROOT/. For exmaple, /mnt/HDA_ROOT/27855.
This random named file is the Linux ransomware executable used to encrypt and decrypt your device.
When executed, it will take a command line argument in the form: [random_file_name] -e <config> <dir>
If QNAP has a command line history, please check for the existince of this command and let us know as a reply to this topic.
When launched it will encrypt the following targeted file extensions:
.3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .ab4, .accdb, .accdc, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .ads, .agdl, .ait, .apj, .arw, .asf, .asm, .asp, .aspx, .asx, .avhd, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bay, .bdb, .bgt, .bik, .bin, .bkf, .bkp, .blend, .bpw, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfp, .cgm, .cib, .class, .cls, .cmt, .conf, .cpi, .cpp, .cr2, .craw, .crl, .crt, .crw, .csh, .csl, .csr, .csv, .dac, .dat, .db3, .db4, .db_journal, .dbc, .dbf, .dbx, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .design, .dev, .dgc, .disk, .djvu, .dng, .doc, .docm, .docx, .dot, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .edb, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fhd, .fla, .flac, .flv, .fpx, .fxg, .gdb, .git, .gray, .grey, .gry, .hbk, .hdd, .hpp, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .iso, .jar, .java, .jpe, .jpeg, .jpg, .jrs, .kc2, .kdbx, .kdc, .key, .kpdx, .lua, .m4v, .mail, .max, .mdb, .mdbx, .mdc, .mdf, .mef, .mfw, .mkv, .mmw, .moneywell, .mos, .mov, .mp3, .mp4, .mpg, .mrw, .msi, .myd, .ndd, .nef, .nk2, .nop, .nrg, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nsn, .nwb, .nx2, .nxl, .nyf, .obj, .oda, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .oil, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .ova, .ovf, .p12, .p7b, .p7c, .p7r, .pages, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pio, .piz, .plc, .pmf, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prf, .ps1, .psafe3, .psd, .pspimage, .pst, .ptx, .pvi, .pvk, .pyc, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .r3d, .raf, .rar, .rat, .raw, .rdb, .rtf, .rw2, .rwl, .rwz, .s3db, .sas7bdat, .say, .sd0, .sda, .sdb, .sdf, .sl3, .sldm, .sldx, .spc, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tar, .tex, .tga, .thm, .tiff, .tlg, .txt, .vbk, .vbm, .vbox, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmem, .vmfx, .vmsd, .vmx, .vmxf, .vob, .vsd, .vsdx, .vsv, .wallet, .wav, .wb2, .wdb, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlk, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xvd, .ycbcra, .yuv, .zip
DeadBolt will also replace the /home/httpd/index.html file so that when you access the device you will see a ransom screen instead.
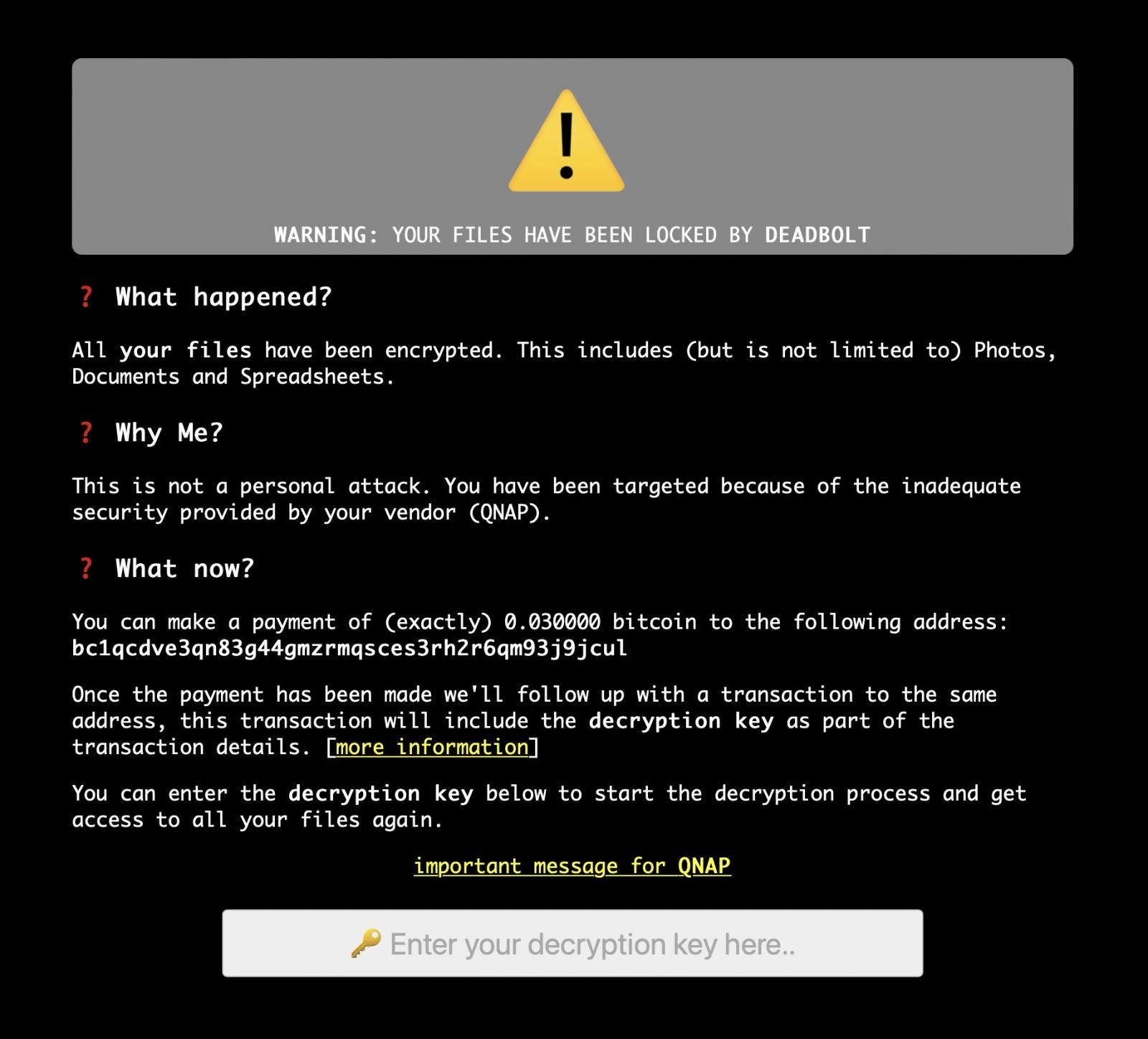
This will prompt you to enter a decryption key that can be obtained by sending 0.03 bitcoins to a listed bitcoin address.
After payment, the threat actors will create another bitcoin transaction to the same address that has the decryption key for your device. The decryption key is located under the OP_RETURN output, as shown below.
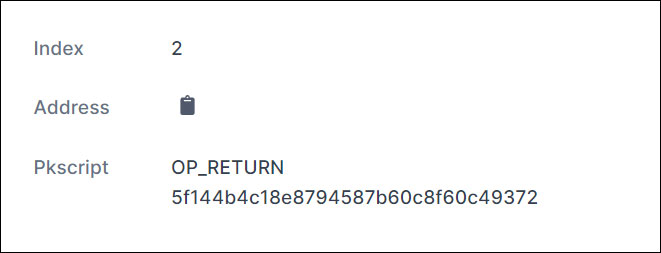
When you enter this key into the ransom note screen, the web page will convert the key into a SHA256 hash.
If that SHA256 hash matches the SHA256 hash of your device's decryption key, it will decrypt the device with that key.
If that SHA256 hash matches the SHA256 hash of the master decryption key, it will decrypt the device with that key.
The SHA256 hash for the master decryption key is 93f21756aeeb5a9547cc62dea8d58581b0da4f23286f14d10559e6f89b078052.
Multiple victims have reported paying the ransom and receiving a decryption key that has successully decrypted their files.
QNAP has told BleepingComputer that users can bypass the ransom screen and gain access to their admin page by using the http://nas_ip:8080/cgi-bin/index.cgi or https://nas_ip/cgi-bin/index.cgi URLs.
QNAP further told us that their Product Security Incident Response Team (PSIRT) is investigating the attack vectors now and that owners should follow these steps to protect their data and NAS.




 Back to top
Back to top










