In December 2018, a new ransomware called Djvu, which could be a variant of STOP, was released that has been heavily promoted through crack downloads and adware bundles. Originally, this ransomware would append a variation of the .djvu string as an extension to encrypted files, but a recent variant has switched to the .tro extension.
When first released, it was not known how the ransomware was being distributed and a sample of the main installer could not be found. When discussing the infection with the numerous victims who reported it in our forums and elsewhere, a common theme was noted; most of the victims stated that they became infected after downloading a software crack.
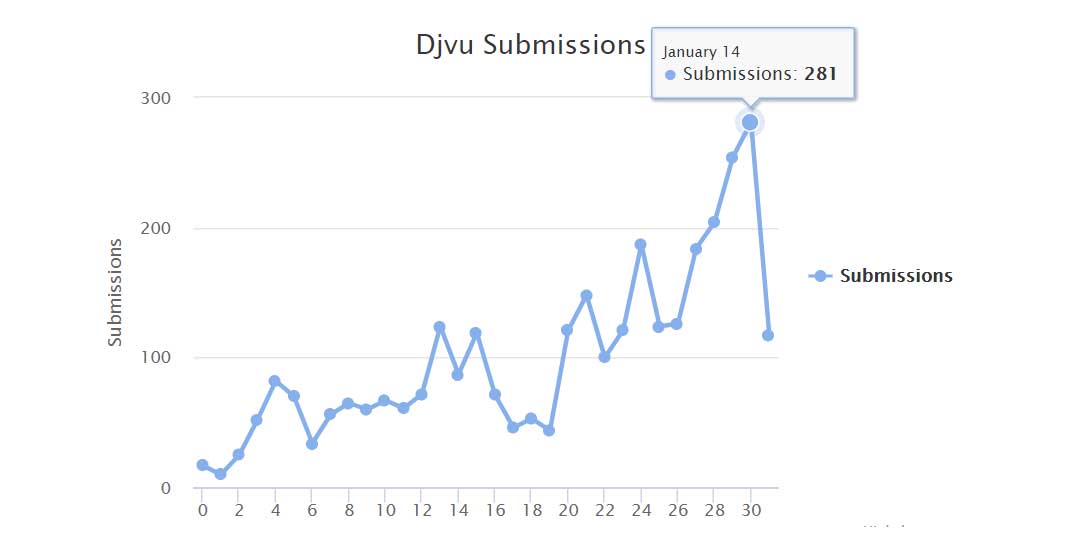
This campaign has been very successful, with ID-Ransomware reporting numerous victims submitting files to their system on a daily basis.
The good news is that it may be possible to receive help in recovering your files for free. If you are infected with STOP Ransomware (.djvu, .tro, or .rumba), please see this post about using Michael Gillespie's decryptor.
If that fails to help, then please register an account and post the following information in a new reply to our dedicated STOP Ransomware Support & Help topic:
- Network card's MAC address. This can be gotten from using the command getmac /v. If you are not sure which MAC address to use, feel free to copy the entire output.
- A link to two encrypted files. You can use the Wetransfer service for this.
- Your personal ID from the ransom note.
After you submit this information, we will try and help you, but please be patient..
If you have any questions or need help, feel free to ask here or in our dedicated STOP Ransomware Support and Help topic.
How the Djvu Ransomware encrypts a computer
Certain cracks and adware bundles are installing this ransomware onto victim's computers. When these cracks are installed, the main installer will be installed as %LocalAppData%\[guid]\[random].exe and executed. This program is the main ransomware component and will first download the following files to the same folder:
%LocalAppData%\[guid]\1.exe
%LocalAppData%\[guid]\2.exe
%LocalAppData%\[guid]\3.exe
%LocalAppData%\[guid]\updatewin.exe
When executed, 1.exe will execute various commands that remove the definitions for Windows Defender and disable various functionality. This executable will also execute a PowerShell script called Script.ps1, which disabled Windows Defender's real-time monitoring using this command:
Set-MpPreference -DisableRealtimeMonitoring $true
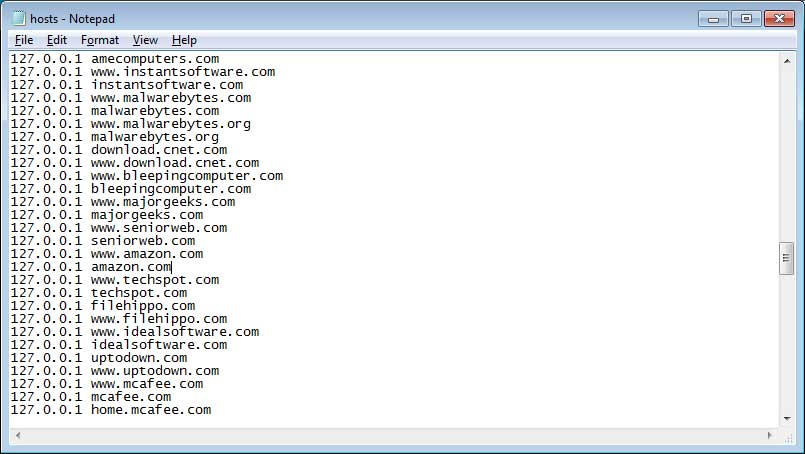
The ransomware will then execute 2.exe, which adds numerous security sites and download sites to the Windows HOSTS file so that victims are unable to connect to them for help. BleepingComputer is one of the sites added to the HOSTS file as shown below.
A file called 3.exe will then be executed, which we have not been able to find a sample of, so are unsure as to what it does.
During this process, the ransomware will generate a unique ID for the machine, which according to Michael Gillespie is a MD5 of the system's MAC address, and connect to it's Command & Control server at the url http://morgem[.]ru/test/get.php?pid=[machine_id]. The server would then reply back with the encryption key that should be used to encrypt a victim's files.
If you are using sflow, netflow, or sniffing traffic on your network then it may be possible to recover your encryption key when the C2 server sends it to the victim's computer.
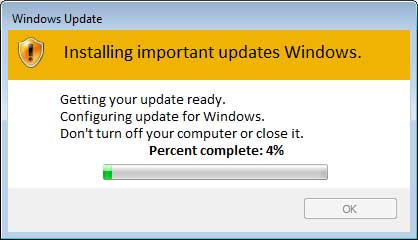
The ransomware will now begin to encrypt the files on the computer and at the same time execute the updatewin.exe. Updatewin.exe will display a fake Windows Update screen in order distract the user while their files are being encrypted and to make it seem normal that disk activity has increased.
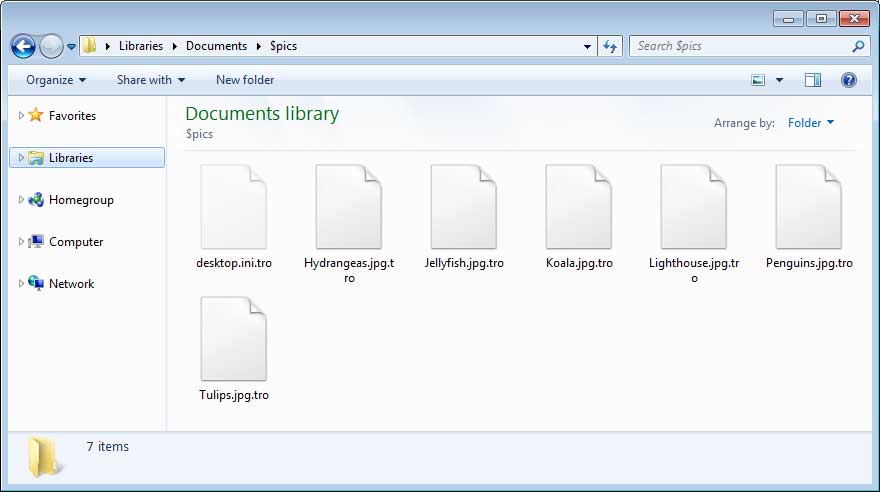
During encryption, the ransomware will encrypt almost all files on the computer, including executables. When encrypting files, the older variant would append a variant of the string .djvu to the encrypted file's name. For example, test.jpg would be encrypted and then renamed to test.djvu, test.djvus, or test.djvut.
Newer variants are instead appending the .tro extension to encrypted file's names as shown by the image below.
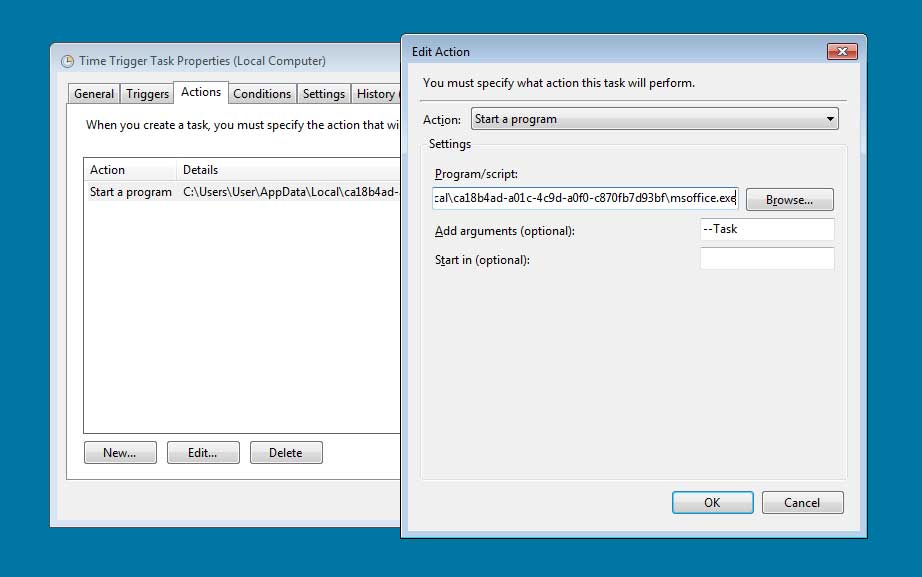
Finally, the ransomware will create a scheduled task named "Time Trigger Task". This task will launch the ransom at various intervals in order to encrypt any new files that are created.
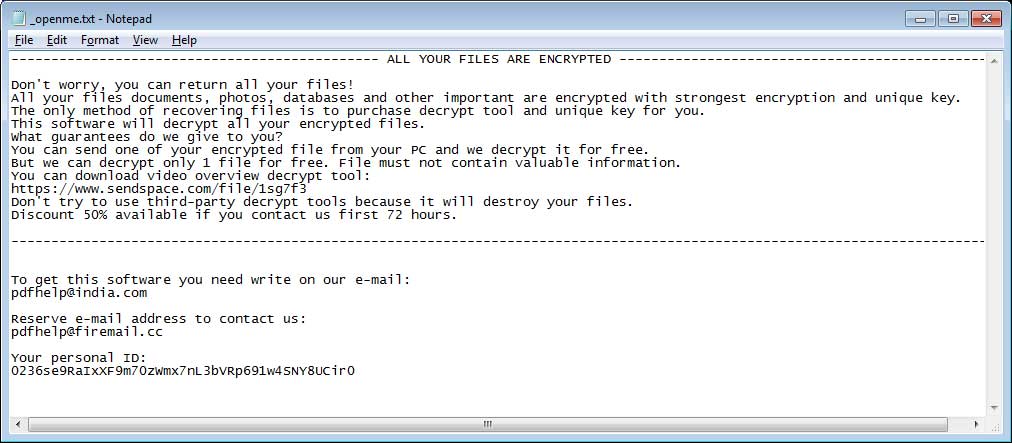
While encrypting files, it will drop ransom notes named _openme.txt in each folder that files are encrypted. This ransom note will contain information regarding what happened to the victim's files and two email addresses that they should contact in order to receive payment instructions.
As previously stated, if you are infected with this ransomware, then it may be possible to recover your files for free. To request help, please see the instructions at the beginning of this article.
IOCs
Hashes:
Main installer: 5d294a14a491dc4e08593b2f6cdcaace1e894c449b05b4132b9ba5c005848c58
1.exe: 6966599b3a7786f81a960f012d540866ada63a1fef5be6d775946a47f6983cb7
2.exe: 91a1122ed7497815e96fdbb70ea31b381b5243e2b7d81750bf6f6c5ca12d3cee
updatewin.exe: 74949570d849338b3476ab699af78d89a5afa94c4529596cc0f68e4675a53c37
Associated Files:
%LocalAppData%\[guid]\[random_numbers]tmp.exe
%LocalAppData%\[guid]\1.exe
%LocalAppData%\[guid]\2.exe
%LocalAppData%\[guid]\3.exe
%LocalAppData%\[guid]\updatewin.exe
C:\Windows\System32\Tasks\Time Trigger Task
Associated Registry Entries:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SysHelper
Associated Email Addresses:
restoredjvu@india.com
restoredjvu@firemail.cc
helpshadow@india.com
helpshadow@firemail.cc
pdfhelp@india.com
pdfhelp@firemail.cc
Network Traffic:
api.2ip.ua
morgem.ru
Ransom Note Text:
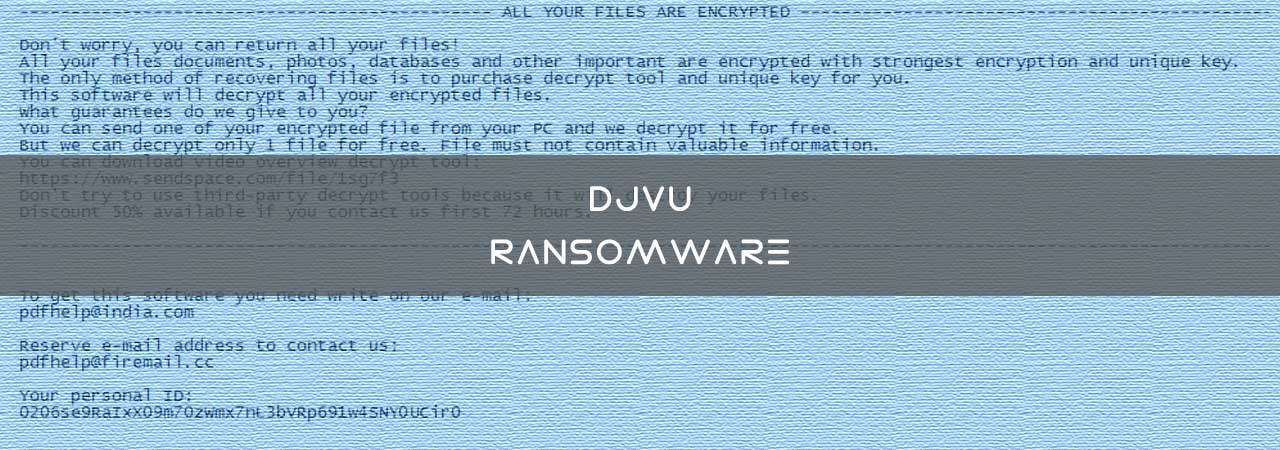
---------------------------------------------- ALL YOUR FILES ARE ENCRYPTED -----------------------------------------------
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can download video overview decrypt tool:
https://www.sendspace.com/file/1sg7f3
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
Your personal ID:
[id]


Comments
MostafaHafez - 5 years ago
i need a helpe please
some one help me
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
personal ID:
028jBiklStLuQGkRlMTrsOAMK1ZRvzmpVZbH9P9M3Wz
nikmocska - 5 years ago
Dear team! my files (photos) are infected with the .djvut virus, but unfortunately this does not help the problem .. :( My Code: 022YiBNHccc3ttXOh7iTHCASK5Yj3nQAQhy9TmR5z48). I've seen many people have the same code in another post! I once hope to find a solution once! Please help me:)
bo3j4n6 - 5 years ago
Please help me to provide STOPDecrypter with Personal ID MjzighkxNnHApe4H3EdOXSIOVhB6GUdnv7c5aEKE
TQ
Andyvee - 5 years ago
I also needs help with the same issue. "Your personal ID:
027HCU6UgT88XLUvUolAP5WuYJFO1DZDdERyg7LGoUF". please mail me in avz.pad@gmail.com if you have a solution.
Many thanks
sadwn06 - 5 years ago
Please help me to provide STOPDecrypter Your personal ID:
027e9vDsY32giKyDIix2kVOrJlJj1M9CMWpP73kUBQh
please mail me in sattr240@gmail.com
bejo21 - 5 years ago
Please help me to provide STOPDecrypter that personal ID:
024kmmkv0lq0hG00eefV3l4IiJhAoKvqgCLCZ68ZryZ
please mail me at kurniawan.wk48@gmail.com
pashkale - 5 years ago
Please help me to provide STOPDecrypter that personal ID:
6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
pashkale@gmail.com
Thank You
talat2019 - 5 years ago
Please help me encrypt all file in .pdff personal ID:
023CRpu5jVGmeNkLFMByWXle6NgeOvFd9qP0Qk6afNw
miliamrin@gmail.com
Thank you.
DarwishSukri - 5 years ago
I have the 3.exe file but I don't know what to do with it and how to send it to you guys
fikri_akbar - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-1aaC7npeV9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
030GHsgdfT7878YsY9gsafJungTBaCmBkpUEcw4QmZSuHfHZS1Zafyl07cvDOc
cleyton - 5 years ago
"ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:https://we.tl/t-1aaC7npeV9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
030GHsgdfT7878YsY9gsafJungTBaCmBkpUEcw4QmZSuHfHZS1Zafyl07cvDOc"
Did you find a way to recover the encrypted files?
hawie - 5 years ago
---------------------------------------------- ALL YOUR FILES ARE ENCRYPTED -----------------------------------------------
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://files.danwin1210.me/uploads/01-2019/Decrypt%20Software%20Overview.avi
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
Your personal ID:
027D02NfEP94dKUO3faH1jwqqo5f9uqRw2Etn2lP3VB
konstantinos88 - 5 years ago
please help me udjvu extention
personal ID:
0177S7ySky4EWij6b2TP0DI4trkWbED9gCcU0VzuXY7
mac E0-D5-5E-2F-3D-2B
asenshui - 5 years ago
PLease help me .blower extention
personal ID : 031Gjhd45hGJGjsdyans4b8aG5ZOwulUVTjVFeoEyhvqgYQTmWVWsp0FyEpV
my email budibsi@ymail.com
Thank You
minjusaif - 5 years ago
Please help me. my pc effected by .tfude
Personal ID: 024PAquh2SWivNpqUw5O49yoiuA8bBMk1YaCpFUryRK
My email: iservicesbd@gmail.com
thanks you
ReemHas - 5 years ago
Helllo
This my personal virus ID :
0163piygIbtv20i2mWq2gSLlLLBbJHHKd6uYaD4Ci8F
and i uploaded the note and 2 infected files :
https://drive.google.com/open?id=1nPvUm72tYInU18o0OVzUaT92EkQyALNi
ReemHas - 5 years ago
plz help me <<<<djvuu encrypted all my files
where can i send u the note and infected file .....
my email is reem.hasanein95@gmail.com
yns8864 - 5 years ago
Hi there,
My all files have also been infected by this type of cryptolocker virus. So I need help.
Please help me restore my files.
Given personal id:
023bgM2ni6VQTp4DWKrpRtXBY2cOo2UMrsYHe15x70n
023bgM2ni6VQTp4DWKrpRtXBY2cOo2UMrsYHe15x70n
Im awating for your urgent solution.
elshaer - 5 years ago
I want to help me decrypt my files with djvuq extensions
The name of the ransom file
This is the content of the ransom file
---------------------------------------------- ALL YOUR FILES ARE ENCRYPTED -----------------------------------------------
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can look online overview decrypt tool:
https://vimeo.com/306940477
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
restoredjvu@india.com
Reserve e-mail address to contact us:
restoredjvu@firemail.cc
Your personal ID:
019Y64ZwwM4CGeUwnkE0OhPqP9RhBCssOF1GrtpgFpF
khaledwinged - 5 years ago
---------------------------------------------- ALL YOUR FILES ARE ENCRYPTED -----------------------------------------------
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can download video overview decrypt tool:
https://www.sendspace.com/file/1sg7f3
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 72 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
Your personal ID:
024HHiNGOVG2mZ80EokBEMRwhYzbqvRCvqjcI7Tw2zz
please help me to get my files back
nayzaw - 5 years ago
PLease help me .blower extention
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
031Gjhd45hGJGjsdyansWpjEq9SJRB8FhTTPZcCZ2bTtnkOvIEWfRaIx5sfm
hoanganhtruong77 - 5 years ago
My files have a * .adobee extension, and I tried STOPDecrypter.zip of Demonslay335 but couldn't. Hope to help me. Thank you!
MuhammadIqbalS - 5 years ago
please help me .blower extention
personal ID : 031Gjhd45hGJGjsdyans6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
my email : MuhammadIqbalSodikin@gmail.com
AlLor4523 - 5 years ago
please help me .promorad extention
personal ID : 6gZ7d34LgX7fU5OWjEMPiyWXK14ws81o5qW61CtM
my email : rednaxela4523@gmail.com
Skizy - 5 years ago
Please help me. my pc affected by : Djvu
Personal ID : q0K1LaHFJaIDZ8jL746nksBh85pZmedMfXO07wGR
My Email : mirandadeebro@live.fr
Thank you
wupohsien - 5 years ago
Please help me. my pc affected by : .promok
Personal ID :037Sdjo43dfIf9sfbBCxQuN3FgcTe50tbsj6JKHrZRDC1gy9WjR8XN5p
My Email : wps7096@gmail.com
Thank you
He4x - 5 years ago
Please help me. my pc affected by : .promok
Your personal ID: 037Sdjo43dfIf9sfdE7pDYD1Snvdo7Hc8gCbsIrSbhoDLP1IbpbpwLRy
My Email :keeleemeen@gmail.com
Thank you!
vianchinieto - 5 years ago
Please help me. my pc affected by : .promok
Your personal ID: 035ALsdhiegSDGftHm30JDd1DU9jztVggcPLV0ujw8ZoXuLBL8BfTKDQ
My Email :vianchi.nieto@gmail.com
Thank you!
vilso - 5 years ago
por favor me ajude djvu extention promoz
pessoal ID:
034OspdywaduiShdktrec4G0PbPjRjqnL75RJYicon5uAWW5jZC3ICsGeiCTV
vilsorodrigues@hotmail.com
kolyokilly - 5 years ago
Please help me. my pc affected by : .tfudet
Your personal ID: 034OspdywaduiShdktrec2OoQsCDszkJVfRqrMyJ9QxG5S3vd38rstXlo3rdN
My Email :kolyoalvaro@gmail.com
Thank you!
tekcesar - 5 years ago
Please help me. my pc affected by : .promorad2
Your personal ID: aoElBzykKF1CJZUqPaT8mfeKuS7CUZooYeZOKZTp
and i uploaded the note and 2 infected files :
https://wetransfer.com/downloads/8d58e8ca3435d9d64945ea7ef2b9e17520190310021730/0def92ad7fbb439a005ce6531577dc4c20190310021730/9baf5c
My Email :teken178@hotmail.com
Thank you!
amerchi - 5 years ago
Hi
My files encrypted with blower Ransomware any help to recover it and decrypted.
Mac
Connection Name Network Adapter Physical Address
Ethernet Realtek PCIe GB 38-D5-47-B7-69-5C
Wi-Fi 802.11n USB Wir E8-94-F6-12-C8-54
Personal ip
031Gjhd45hGJGjsdyansA1SqojfT8xjjLQbI0Z208FHledtcx5mTiVB0cXQX
Wetransfer link
https://we.tl/t-jZZ2eMf6ig
Thanks
macrabocwb - 5 years ago
Por favor me ajude djvu extention promoz
pessoal ID:
034OspdywaduiShdktrec
macrabocwb@hotmail.com
towhidulislam - 5 years ago
My gmail: towhidulislam1@gmail.com
My MAC Address:
Windows IP Configuration
Host Name . . . . . . . . . . . . : DESKTOP-P3TS97K
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Ethernet 2:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Kaspersky Security Data Escort Adapter
Physical Address. . . . . . . . . : 00-FF-26-45-30-58
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Wi-Fi:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : 802.11n USB Wireless LAN Card
Physical Address. . . . . . . . . : D4-6E-0E-11-FD-FB
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Local Area Connection* 2:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Wi-Fi Direct Virtual Adapter
Physical Address. . . . . . . . . : D4-6E-0E-11-FD-FD
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Realtek PCIe GBE Family Controller
Physical Address. . . . . . . . . : 6C-62-6D-5D-9B-A0
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::f5e3:5b29:ca74:2330%5(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.0.105(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Tuesday, March 12, 2019 8:21:22 PM
Lease Expires . . . . . . . . . . : Tuesday, March 12, 2019 10:21:22 PM
Default Gateway . . . . . . . . . : 192.168.0.1
DHCP Server . . . . . . . . . . . : 192.168.0.1
DHCPv6 IAID . . . . . . . . . . . : 74211949
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-1A-5A-58-6C-62-6D-5D-9B-A0
DNS Servers . . . . . . . . . . . : 192.168.0.1
NetBIOS over Tcpip. . . . . . . . : Enabled
Tunnel adapter isatap.{4EF72EFC-40FB-4EDF-A519-D99BA5C67C08}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Tunnel adapter Teredo Tunneling Pseudo-Interface:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Teredo Tunneling Adapter
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : 2001:0:2851:78dd:2cff:1056:8ef4:c639(Preferred)
Link-local IPv6 Address . . . . . : fe80::2cff:1056:8ef4:c639%8(Preferred)
Default Gateway . . . . . . . . . : ::
DHCPv6 IAID . . . . . . . . . . . : 318767104
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-1A-5A-58-6C-62-6D-5D-9B-A0
NetBIOS over Tcpip. . . . . . . . : Disabled
Ransom note:
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-qE5J2sY0BY
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
040JsdhuwabdaHSakdakroOlxDM8YPKcu3eVOjWSx6M9zW6kjsYElIrRubql
Hi, I could not find your email address so I could not send you two of my encrypted files.
Pls help me. I have lost all of my important documents.
kevincc93 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-PkTh0Y7Koy
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
039OspdywaduiShdktrecs0NXCUGBIvWpnUAUMnIrYbN5N8QO4dTq5FzNWDGo
Espero me pueda ayudar yo guardare la información dañada en un disco duro y la separare de mi pc,creo que esperare una solucion,gracias
n200279 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-T9WE5uiVT6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
046Sdsd3273yifhsisySD6eTEtoMIoEOKdORPmfOaJxpeH3EUpxIYgNZd3nVt6
neofix - 5 years ago
"ATTENTION!
write mail
mmbe1000 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-flMQaa7Bd2
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
031Gjhd45hGJGjsdyans6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
joravalbe - 5 years ago
Hello I'm from Venezuela and all my files were encrypted :(
Part of the Readme.txt
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
046Sdsd3273yifhsisySD60h7mFQcjRC3pDgsRcrWZ7K7bdAgvgDos224DmXt1
also in the StopDecrypter
No key for ID: 0h7mFQcjRC3pDgsRcrWZ7K7bdAgvgDos224DmXt1
My Mac Address : A4:4E:31:60:9E:FC
the extension file is kropun
arif_kleden - 5 years ago
personal ID:
052Asduih734yuDGdsf73yidNemxeJkNdboLZJ2wDBi7D5RwN13M7YQ2NH5X8
Mac Address :
38-2C-4A-74-F0-D9
email :
arif.rifai.bin.muhammad@gmail.com
arif_kleden - 5 years ago
personal ID:
052Asduih734yuDGdsf73yidNemxeJkNdboLZJ2wDBi7D5RwN13M7YQ2NH5X8
Mac Address :
38-2C-4A-74-F0-D9
email :
arif.rifai.bin.muhammad@gmail.com
Atlants - 5 years ago
HELP ME GUYS
MAC- 24-F5-AA-F2-12-F1 –LAN
MAC- 98-83-89-04-6C-3D –WLAN
POST SCAN with DECRYT tool
File: C:/SISMARC.cab.pulsar1
[-] No key for ID: BwbeFYNyqrHffN2gRQZoH30idbTZFqGefjQFXuq6
RANSOM NOTE
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-T9WE5uiVT6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:041GFbnsfuyxcBwbeFYNyqrHffN2gRQZoH30idbTZFqGefjQFXuq6
Nirmol - 5 years ago
Hi,
My all files have also been infected by this type of .RUMBA virus. So I need help.
Please help me restore my files.
Im awating for your urgent solution.
uncut - 5 years ago
Hi,
My all files have also been infected by this type of .DOPLES virus. So I need help.
Please help me restore my files.
_readme.txt:
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-W8DuFk4wwu
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
049JSdie374yHduf74YybbTCb7pjWiws7oVW6SJEx9q4kb89FqnFwzZT8p
ID Ransomware:
Identified by
ransomnote_email: blower@firemail.cc
sample_extension: .doples
sample_bytes: [0xC968 - 0xC982] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
my email: uncutdot@gmail.com
mac: 00-E0-4C-36-1C-33
HELP ME GUYS
mk78 - 5 years ago
hi, I need help with this f*cking ransomware
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-W8DuFk4wwu
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
052Asduih734yuDGdsf73rdSXuFaXQZ5zsBX7nzxYC2hgkTkducsD7tuV95t1
mail: fefendes@gmail.com
thanks very much
robsonsantos - 5 years ago
PLease help me .blower extention
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
049JSdie374yHduf74pgWeqjCfZdui2ITlZUpsFGBcwAb1oMTEAjr5Sp4I
E-Mail: robsonluis.2012@gmail.com
zamrong - 5 years ago
plz help me .grovas extention
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-hK4tAv2Ed9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
058dfgdgydktrecbOhzH7bsm08gUSpzmkOriPikDQsibD586U2JU1Tv
email: zamrong@gmail.com
mediaart - 5 years ago
plz help me .grovas extention
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-hK4tAv2Ed9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
058dfgdgydktrecdybbpRUjaC6ZtcJn4iDSJfzuEWLl5oE3fC8yCeIh
my email : madsu.jaya@gmail.com
smile2174 - 5 years ago
plz help me .grovas extention
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
058dfgdgydktrecFOmqfZMudFslerMkx6uKfP0PGqJ66jZZqIS6bCIE
my email : mohamedsayed2174@gmail.com
GoofyGoof - 5 years ago
infect with (.grovas)
My personal ID:
058dfgdgydktrecESuYP95awwGfzTM11rgY5HKXZMiYskpIVCMf4GEB
No key for ID: ESuYP95awwGfzTM11rgY5HKXZMiYskpIVCMf4GEB (.grovas )
MAC: F4-6D-04-E9-27-75
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
GoofyGoof - 5 years ago
infect with (.grovas)
My personal ID:
058dfgdgydktrecESuYP95awwGfzTM11rgY5HKXZMiYskpIVCMf4GEB
No key for ID: ESuYP95awwGfzTM11rgY5HKXZMiYskpIVCMf4GEB (.grovas )
MAC: F4-6D-04-E9-27-75
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
delta469 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-hK4tAv2Ed9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
056dhfgrtycbnalvYbOypJyfAIco2fdzXC6eLoJOpOo3UOTDKSV9bdC
(.tronas)
expertomz - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-1LFQOfI0Se
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
059AKshdyuhSdwjj9WNurlzTlydDFeNZIwpC2ZjEJfp6WeIdqDP08T
email : tomi.hartedi@gmail.com
Thank You For Your Help
zainlr - 5 years ago
can anybody help me i am fed up now with this ransomware attack. all my family details and pics are on it. included my portfolio and etc.
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-T9WE5uiVT6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
046Sdsd3273yifhsisySD6F7LWv0zYdztkRI33YBcGa7QjC3osDxtwjNNGdaiP
Please help me my email is zainlr@gmail.com... PLEASE PLEASE PLEASE.
kabbua - 5 years ago
ช่วยผมด้วยครับ งานที่สำคัญสำหรับการเรียนผมมากครับ ผมไม่เก่งภาษา า kabbua1@gmail.com /
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-hK4tAv2Ed9
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
058dfgdgydktrecAjbMdBSEqyVuIpyYdUHNwlE5FUKsE0kYuJF8Etnh
qwanraja2019z - 5 years ago
Dear Sir,
Please help me, my all files infected with (.grovas)
I need to recover all my files
Thanks
My personal ID:
058dfgdgydktrec35yNkWVlaFR9mMlJyY089fUCAsXPNtjFBUtao8gw
MAC: 90-2B-34-97-3D-E2
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
058dfgdgydktrec35yNkWVlaFR9mMlJyY089fUCAsXPNtjFBUtao8gw
DAIZERD - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-xuSAEnnA8P
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@india.com
Reserve e-mail address to contact us:
vengisto@firemail.cc
Your personal ID:
065btydsljfhsFfwNlhLnztKcEv8wK2i0DeTsRcp6g4lb3f8hZi6ULU
Xbenx99 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-xuSAEnnA8P
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@india.com
Reserve e-mail address to contact us:
vengisto@firemail.cc
Your personal ID:
065btydsljfhsFfz7OAPIhNFblb8opzkr2TkSQ3Jd09wpaM00eFed47
(.guvara)
mahmo - 5 years ago
Dear Sir,
Please help me, my all files infected with (.guvara)
.
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-xuSAEnnA8P
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@india.com
Reserve e-mail address to contact us:
vengisto@firemail.cc
Your personal ID:
065btydsljfhsFf81PxYfUZxMhnQiibgFdsZ1rQ5zmaZdp0I9Ufbm9w
djerryzaunga - 5 years ago
Please Help Me
Windows 10 Pro 64-bit os
No keys were found for the following IDs:
[*] ID: 99tuOIDHp9g7XMKf2VuTBm0EQkZiINdbHzMGrVGd (.jpg )
[*] ID: 99tuOIDHp9g7XMKf2VuTBm0EQkZiINdbHzMGrVGd (.refols )
Please archive these IDs and the following MAC addresses in case of future decryption:
[*] MAC: 96:EE:A4:22:C7:6E
This info has also been logged to STOPDecrypter-log.txt
Microsoft Windows [Version 10.0.17134.706]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\user>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : DESKTOP-RV88OIM
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Ethernet:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Realtek PCIe GBE Family Controller
Physical Address. . . . . . . . . : 98-29-A6-8A-3D-01
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Local Area Connection* 3:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Wi-Fi Direct Virtual Adapter #2
Physical Address. . . . . . . . . : AC-ED-5C-85-4F-63
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Local Area Connection* 4:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Wi-Fi Direct Virtual Adapter #3
Physical Address. . . . . . . . . : AE-ED-5C-85-4F-62
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Wi-Fi:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) Dual Band Wireless-AC 3165
Physical Address. . . . . . . . . : 96-EE-A4-22-C7-6E
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::497d:eaec:4f9:aa2a%19(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.1.2(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Senin, 15 April 2019 08.52.51
Lease Expires . . . . . . . . . . : Selasa, 16 April 2019 08.52.51
Default Gateway . . . . . . . . . : fe80::1%19
192.168.1.1
DHCP Server . . . . . . . . . . . : 192.168.1.1
DHCPv6 IAID . . . . . . . . . . . : 328658596
DHCPv6 Client DUID. . . . . . . . : 00-03-00-01-96-EE-A4-22-C7-6E
DNS Servers . . . . . . . . . . . : 118.98.44.100
118.98.44.10
NetBIOS over Tcpip. . . . . . . . : Enabled
Ethernet adapter Bluetooth Network Connection:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Bluetooth Device (Personal Area Network)
Physical Address. . . . . . . . . : AC-ED-5C-85-4F-66
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
C:\Users\user>
...........................
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-vpovVceDWN
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
merosa@india.com
Reserve e-mail address to contact us:
merosa@firemail.cc
Your personal ID:
061OspdywaduiShdktrec99tuOIDHp9g7XMKf2VuTBm0EQkZiINdbHzMGrVGd
JOSEVI - 5 years ago
Hi, I need your help. Thanks in advance.
Your personal ID:
028d2fnv4LVB810gCvHGkaDADuTbmq3dQsdSXyZT2bs
My computer data are:
Dirección física. . . . . . . . . . . . . : B8-AE-ED-F7-9F-FA
Dirección IPv4. . . . . . . . . . . . . . : 192.168.1.42 ( Prefered)
Extensions: .adobe
qwanraja2019z - 5 years ago
Dear Sir,
Please help me, my all files infected with (.grovas)
I need to recover all my files
Thanks
My personal ID:
058dfgdgydktrec35yNkWVlaFR9mMlJyY089fUCAsXPNtjFBUtao8gw
MAC: 90-2B-34-97-3D-E2
I have upload encrypted file and original file at link :
https://drive.google.com/drive/folders/1z3TX9iuJsBVEeKS6TSOsHsFKTr8HROO7?usp=sharing
Failed when Using STOPDecrypter version 2.0.23
[!] No keys were found for the following IDs:
[*] ID: 35yNkWVlaFR9mMlJyY089fUCAsXPNtjFBUtao8gw (.grovas )
Please archive these IDs and the following MAC addresses in case of future decryption:
[*] MAC: 90:2B:34:97:3D:E2
CuisineSoftware - 5 years ago
Good day hope someone can help please?
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
067vtdsUezls8UewKOimuncHsxHIrDko23pqvlDGbX4DiKTinccJ9
Log from StopDecrypter:
No key for ID: UewKOimuncHsxHIrDko23pqvlDGbX4DiKTinccJ9 (.norvas )
Unidentified ID: UewKOimuncHsxHIrDko23pqvlDGbX4DiKTinccJ9 (.norvas )
MAC: FC:AA:14:14:89:2E
Decrypted 0 files, skipped 1
My email: support@cuisinesoftware.com
Thank You
diego87 - 5 years ago
Good day sir. I need your help please.
All my files were infected with the extension .norvas
I have recieved this txt file in every folder:
*-----------------------------------------------------------------------------*
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
067vtdsUezls81hVfLtryFr7TgWczZu6lliYOgyhs0QRIWXiLw0U6
*-------------------------------------------------------------------------------------------------------------*
My MAC direction: 50:B7:C3:D7:40:00
My email : diegoyakkov@gmail.com
Any help will be so much appreciated. Thank you.
ginthu - 5 years ago
https://we.tl/t-caaWisUkSc
this file i found in my folders and i think this one do the encryption., please check this lets if can find any solution from here
FahadIqbal - 5 years ago
Hi Dear Sir my Computer has completely Damaged by newest Ransomware virus extention
" .norvas ". This extention has been attached with all of my computer files pictures videos pdf software. Though virus has removed after using Malwarebytes Anti Malware (https://www.malwarebytes.com/mwb-download/ ) But now my all personal data is not decrypting due to this " .norvas " extention virus. Please help me thanks. I received the following data from the hackers:
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
067vtdsUezls8Uig31Hixxc5bejvqNRRzTwW9I8pWges9qcoFXixG
Now my personal Files are in the following shape:
AutoCAD Certificate Copy Front Side.png.norvas
Course Outline of DAE Civil Technology.html.norvas
AutoCAD Draftsman CV-MFAHADIQBAL---07-JAN-2016.doc.norvas
etc etc
fastosh21 - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
068Sdah83763FSsdfasuiD2yB9JiYh6O2p3M7pdnNaYUl7RK8Jr3PkrW33zMd
rokibih - 5 years ago
Please help me. Please, Please.
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
068Sdah83763FSsdfasuinMHrfCN1wfAt44q4UjDOwzTAbw6RLGw5YbEr3m4G
AdrianoOliveira8 - 5 years ago
ID: 067vtdsUezls8B1bHFni91axMHzjG2codNyyGcb8OjpG3AgibLCG8
MAC: C0:38:96:A3:C:2B
Dear Sir, may all data has ecryted by this virus".norvas" Please HELP ME!
namthanh13 - 5 years ago
ID: 065btydsljfhsFfk4LaKHFZA0uvaY9X4WEtcIy3zeAfpLR3ZaLyGOvn
MAC: 18:D6:C7:07:8E:D8
".guvara"
please, help me. Thanks so much
yanaribowo - 5 years ago
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
068Sdah83763FSsdfasuiU5CAUsaVTZswlzA5i55QCXyn9NuYckFTNez0ozSc
PLASE HELP ME , all data has ecryted by this virus .norvas ...THANKS SO MUCH
jonysrb - 4 years ago
Today my all files was encrypted with .HROSES any idea for decrypt files?
ReemHas - 4 years ago
Hello
All files are attached
1-Ransomware Note
2-sample of infected files
3- mac Address
4- Virus type .Djvuu
My email: Reem.hasanein95@gmail.com
Please help me i attached everything u need
https://drive.google.com/open?id=1nPvUm72tYInU18o0OVzUaT92EkQyALNi
RendiIrawan - 4 years ago
plz help me .ldxdsmoms extention
ATTENTION!
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-lQ7jXsWgdB
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
Your personal ID:
0296se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
my email : rendiirawan668@gmail.com
please, help me. Thanks so much
mersimoy - 4 years ago
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.guvara )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.jpg )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.mp3 )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.DAT )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.wav )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.exe )
No key for ID: PC44tYNt1aTkKsPCnK74khN5EdAKqbaqMr8chiyo (.doc )
MACs: F4:30:B9:80:67:45, B0:35:9F:71:B7:A5, B0:35:9F:71:B7:A4, B0:35:9F:71:B7:A8
Please Help, Thanks in advance
GURPREET00786 - 4 years ago
HI MY NAME IS GURPREET SINGH.PLEASE HELP ME DJVU
ID
Decrypted 0 files!
Skipped 4 files.
[!] No keys were found for the following IDs:
[*] ID: y957MPLYgY011TXC6vsX57pU6bTktkLFIXfhWVLQ (.lanset )
Please archive these IDs and the following MAC addresses in case of future decryption:
[*] MACs: 2C:60:0C:F3:0B:2D, 32:52:CB:24:13:5D, 30:52:CB:24:13:5D
This info has also been logged to STOPDecrypter-log.txt