The STOP ransomware has seen very heavy distribution over the last month using adware installers disguised as cracks. This campaign continues with a new variant released over the past few days that appends the .rumba extension to the names of encrypted files.
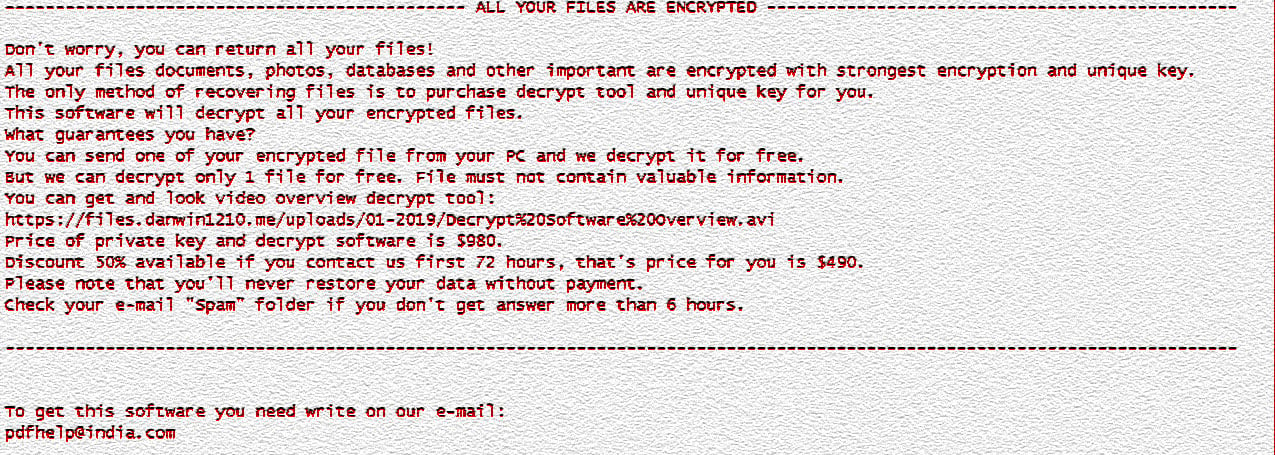
Using adware bundles and software cracks as a new distribution method, STOP has become one of the most prolific ransomware infections we have seen in quite a while. First starting with the .djvu extension, then switching to the .tro extension, this latest .rumba variant continue to be heavily distributed as can be seen by the chart from ID Ransomware below.
A common practice used by sites that distribute software cracks is to utilize adware bundles in order to generate revenue. These bundles will normally install unwanted extensions, adware, clickers, and miners, but one bundler appears to be turning a blind eye and has started distributing the STOP Ransomware as well.
Some of the reported cracks that are installing this ransomware include Windows activation cracks such as KMSPico, Cubase, Photoshop, antivirus software, and cracks for many other popular copyrighted software. From reports by infected users, it does not appear to be one particular crack site that is affected, but many different ones who are pushing similar adware bundles.
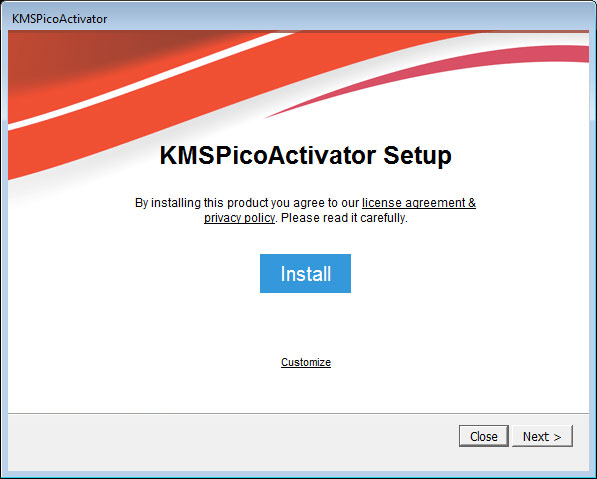
In this new variant, not much has changed and the developers continue to use the same approach as outlined in our DJVU article. The main difference is in this version the ransomware will append the .rumba extension to a file's name after it is encrypted as shown below.
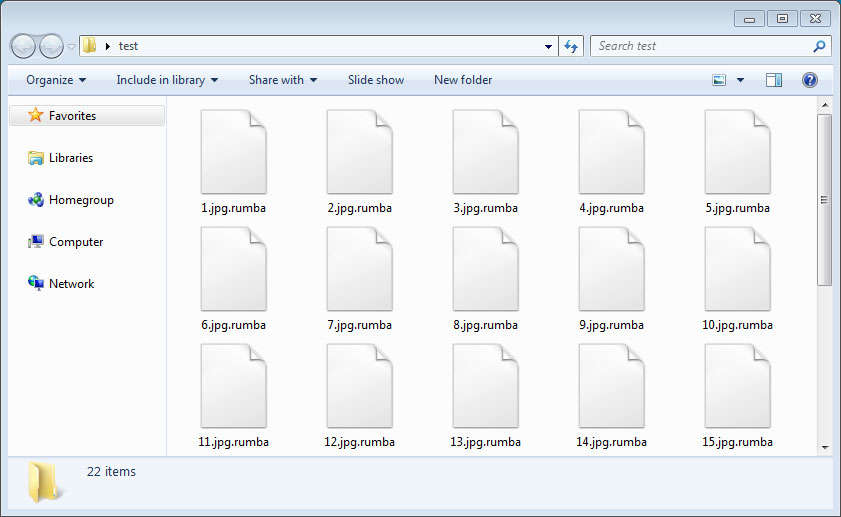
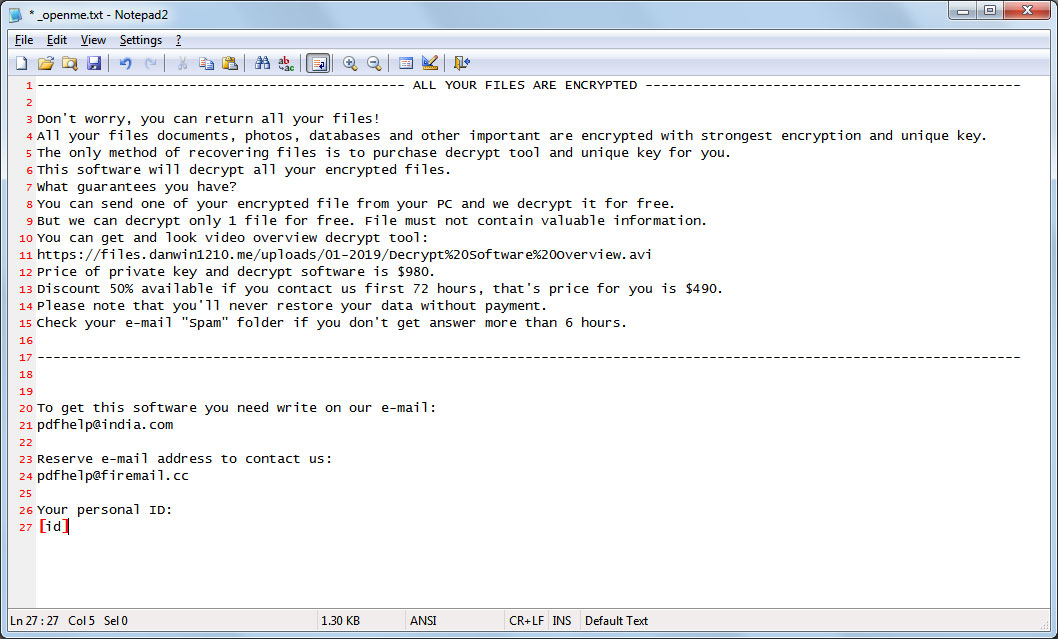
In each folder that a file is encrypted, the ransomware will create a ransom note named _openme.txt that contains instructions on how to contact the attacker for payment instructions.
The good news is that it may be possible to receive help in recovering your files for free. If you are infected with STOP Ransomware (.djvu, .tro, or .rumba), please see this post about using Michael Gillespie's decryptor.
If that fails to help, then please register an account and post the following information in a new reply to our dedicated STOP Ransomware Support & Help topic:
- Network card's MAC address. This can be gotten from using the command getmac /v. If you are not sure which MAC address to use, feel free to copy the entire output.
- A link to two encrypted files. You can use the Wetransfer service for this.
- Your personal ID from the ransom note.
After you submit this information, we will try and help you, but please be patient..
IOCs
Hashes:
2b43163fdbeab448c292abb4e34dc395175b80328232d4fd884011ee525cedb6
Ransom Note:
---------------------------------------------- ALL YOUR FILES ARE ENCRYPTED -----------------------------------------------
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://files.danwin1210.me/uploads/01-2019/Decrypt%20Software%20Overview.avi
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
---------------------------------------------------------------------------------------------------------------------------
To get this software you need write on our e-mail:
pdfhelp@india.com
Reserve e-mail address to contact us:
pdfhelp@firemail.cc
Your personal ID:
[id]


Comments
BobPony - 5 years ago
Yesterday, I wanted to do an experiment in a VM since I was bored and curious so I've looked that stuff up on purpose to try to get it infected and I briefly saw an installer looking like that for a second before it disappeared, but oddly I didn't get the ransomware since apparently it gives an error message saying connection failure even tho it was connected to the internet. It makes me wonder if there's a secret block from preventing the ransomware happening.
Lawrence Abrams - 5 years ago
If anything, probably a geo block or VM detection in the adware bundle itself rather than the ransomware.
abolfazl2736 - 4 years ago
Please help me all my files are encrypted (.Rumba)
these are my details
Your personal ID:
0277aTI7lbVkipYAZazfUzV90bLDL7jy9YgeCPRx9hP
Mac ID Should be this :: 60:45:CB:26:77:6D
other all info at this link sample images ransome note decryter log etc :
.rumba encipted files: https://we.tl/t-u5RRFAAJlw
orginal file: https://we.tl/t-ttLQWfjOkh
Please HELP ME
Thanks in advance