
In addition to encrypting a victim's files, the STOP ransomware family has also started to install the Azorult password-stealing Trojan on victim's computer to steal account credentials, cryptocurrency wallets, desktop files, and more.
The Azorult Trojan is a computer infection that will attempt to steal usernames and passwords stored in browsers, files on a victim's desktop, cryptocurrency wallets, Steam credentials, browser history, Skype message history, and more. This information is then uploaded to a remote server that is under the control of the attacker.
When we first covered the DJVU variant of the STOP Ransomware being distributed by fake software cracks in January, we noted that when the malware was executed it would download various components that are used to perform different tasks on a victim's computer. These tasks include showing a fake Windows Update screen, disabling Windows Defender, and blocking access to security sites by adding entries to Windows's HOSTS file.
When ransomware researcher Michael Gillespie tested some recent variants he noticed that an Any.Run install indicated that one of the files downloaded by the ransomware created traffic that was from an Azorul infection. Gillespie further told BleepingComputer that four different samples all showed network traffic associated with Azorult.
BleepingComputer downloaded and installed a sample of the STOP Promorad Ransomware variant to see if Azorult would be installed.
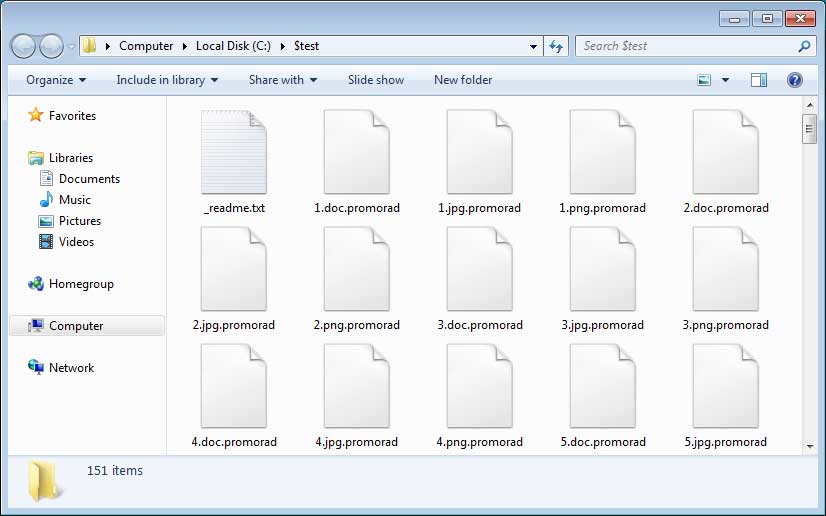
When we executed the ransomware, it proceeded to download the files listed in the IOCs below and encrypt the computer. In this particular variant, when files are encrypted it will append the .promorad extension to encrypted files and create ransom notes named _readme.txt as shown below.
The Promorad Ransomware variant samples we tested also download a file named 5.exe and executed it. When executed, the program will create network traffic that is identical to known command & control server communications for the Azorult information-stealing Trojan.
Furthermore, when this file was scanned using VirusTotal, numerous security vendors detect this file as a password-stealing Trojan.
Being a victim of ransomware is bad enough, but to know that your passwords and documents may be stolen as well just adds another layer of issues that victims need to be concerned about.
Victims who have been infected with a STOP Ransomware variant should immediately change the passwords to any online accounts that are used, especially ones that are saved in the browser. Victims should also change passwords in software such as Skype, Steam, Telegram, and FTP Clients. Finally, victims should check any files stored on the Windows desktop for private information that may now be in the hands of the attackers.
STOP Ransomware has become a prolific extension with numerous variants and it is not currently known how long they have been installing Azorult. Therefore, to be safe all victims of STOP should perform the above remediation.
The known list of STOP extensions include:
.blower
.djvu
.infowait
.promok
.promorad2
.promos
.promoz
.puma
.rumba
.tro
If you have any concerns or questions regarding this ransomware, feel free to post in our dedicated STOP Ransomware Support & Help topic.
IOCs
Hashes:
Ransomware: 1dabaae66931e6414803313adee4d7b5305acba3ad539f49b6aba65f10f809a6
Azorult: 5c258f35e2b9b6997464631e1178841d090a47f3b43d1f6f54621128d352d2f3
Network Traffic:
http://ymad.ug/tesptc/ck/updatewin1.exe
http://ymad.ug/tesptc/ck/updatewin2.exe
http://ymad.ug/tesptc/ck/updatewin.exe
http://ymad.ug/tesptc/ck/3.exe
http://ymad.ug/tesptc/ck/4.exe
http://ymad.ug/tesptc/ck/5.exe
http://ymad.ug/1/index.php
Ransom Note Text:
ATTENTION!
Don't worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-ll0rIToOhf
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
blower@india.com
Reserve e-mail address to contact us:
blower@firemail.cc
Your personal ID:
[id]


Comments
manuel77 - 4 years ago
what should i do sir
manuel77 - 4 years ago
I have turn on my computer these morning and someone hacked my computer and even all the hardrives i have incred by windows
they encrypte all my files HELP and they also let me a note saying it look
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-IbdGyCKhdr
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
salesrestoresoftware@firemail.cc
Reserve e-mail address to contact us:
salesrestoresoftware@gmail.com
Your personal ID:
0176Asd374y5iuhldORwK7D30sUxCgje1OdRXZbKmfAPxHtaP6d4uEzFH
I want to open it my files what should i have do to !!!
manuel77 - 4 years ago
I have trying to get the application .exe to try an id or pass but they removes it from a hosting server so they have it https://precisesecurity.com/tools-resources/removal-tools/download-ransomware-decryption-tools
help do you know how can i get back my information