Today a new Locky Ransomware variant was discovered by @dvk01uk that switches from the .ZEPTO extension to the .ODIN extension for encrypted files. It is important to note that if you are infected with this ransomware, you are not infected with the Odin Ransomware. You are instead infected by Locky, which is using the .ODIN extension. There is a difference.
Like previous variants, this sample is being spread through WS, JS, etc email attachments attached to SPAM emails. If a recipient double-clicks on one of these script files, it will download an encrypted DLL installer, decrypt it, and execute it using the legitimate Windows program called Rundll32.exe.
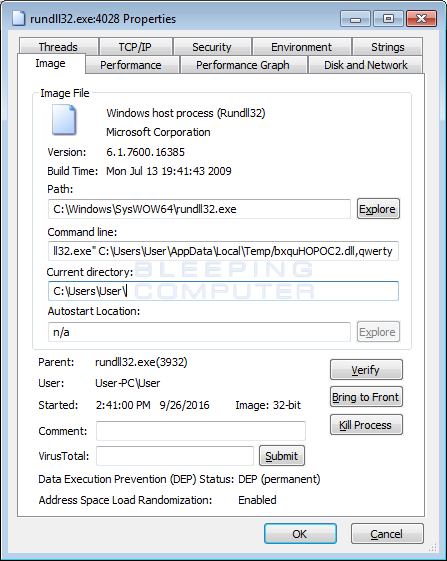
The command that is executed to launch the DLL is:
rundll32.exe %Temp%\[name_of_dll],qwerty
Once executed, Locky will encrypt a victim's files, rename them, and then append the .ODIN extension. For example, test.jpg may be renamed as 5FBZ55IG-S575-7GEF-2C7B-5B22862C2225.odin.
With this release, the names of the ransom note have changed as well. The ransom notes that are created by the current version are _HOWDO_text.html, _HOWDO_text.bmp, and _[2_digit_number]_HOWDO_text.html.
Last, but not least, the extensions targeted for encryption by this variant are:
.yuv, .ycbcra, .xis, .wpd, .tex, .sxg, .stx, .srw, .srf, .sqlitedb, .sqlite3, .sqlite, .sdf, .sda, .s3db, .rwz, .rwl, .rdb, .rat, .raf, .qby, .qbx, .qbw, .qbr, .qba, .psafe3, .plc, .plus_muhd, .pdd, .oth, .orf, .odm, .odf, .nyf, .nxl, .nwb, .nrw, .nop, .nef, .ndd, .myd, .mrw, .moneywell, .mny, .mmw, .mfw, .mef, .mdc, .lua, .kpdx, .kdc, .kdbx, .jpe, .incpas, .iiq, .ibz, .ibank, .hbk, .gry, .grey, .gray, .fhd, .ffd, .exf, .erf, .erbsql, .eml, .dxg, .drf, .dng, .dgc, .des, .der, .ddrw, .ddoc, .dcs, .db_journal, .csl, .csh, .crw, .craw, .cib, .cdrw, .cdr6, .cdr5, .cdr4, .cdr3, .bpw, .bgt, .bdb, .bay, .bank, .backupdb, .backup, .back, .awg, .apj, .ait, .agdl, .ads, .adb, .acr, .ach, .accdt, .accdr, .accde, .vmxf, .vmsd, .vhdx, .vhd, .vbox, .stm, .rvt, .qcow, .qed, .pif, .pdb, .pab, .ost, .ogg, .nvram, .ndf, .m2ts, .log, .hpp, .hdd, .groups, .flvv, .edb, .dit, .dat, .cmt, .bin, .aiff, .xlk, .wad, .tlg, .say, .sas7bdat, .qbm, .qbb, .ptx, .pfx, .pef, .pat, .oil, .odc, .nsh, .nsg, .nsf, .nsd, .mos, .indd, .iif, .fpx, .fff, .fdb, .dtd, .design, .ddd, .dcr, .dac, .cdx, .cdf, .blend, .bkp, .adp, .act, .xlr, .xlam, .xla, .wps, .tga, .pspimage, .pct, .pcd, .fxg, .flac, .eps, .dxb, .drw, .dot, .cpi, .cls, .cdr, .arw, .aac, .thm, .srt, .save, .safe, .pwm, .pages, .obj, .mlb, .mbx, .lit, .laccdb, .kwm, .idx, .html, .flf, .dxf, .dwg, .dds, .csv, .css, .config, .cfg, .cer, .asx, .aspx, .aoi, .accdb, .7zip, .xls, .wab, .rtf, .prf, .ppt, .oab, .msg, .mapimail, .jnt, .doc, .dbx, .contact, .mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .wallet, .upk, .sav, .ltx, .litesql, .litemod, .lbf, .iwi, .forge, .das, .d3dbsp, .bsa, .bik, .asset, .apk, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .pst, .onetoc2, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key


Comments
Binary_Fission - 7 years ago
We have a customer that picked up this ransomware this afternoon and is reporting seeing an .odin file in c:\users\default as well... Has anyone else seen that? Also, the file encryption may be occurring on non-mapped drive locations...??! Still need confirmation on that... They also believe the source of the malware was an XLS file.
Lawrence Abrams - 7 years ago
Yes, locky will encrypt unmapped network shares as well. It will also target all matching files, even though I believe in user\default.
Akatriel - 7 years ago
It happened in our environment too, mass spam with .xls.exe attachments have been sent to over 500 users and lest than 100 were infected. So far we had to clean wipe the drives and reinstall everything. Not funny at all, though.
Lawrence Abrams - 7 years ago
If anyone has a sample of one of these emails containing the xls.exe I would appreciate a sample. Can be sent to https://www.bleepingcomputer.com/submit-malware.php?channel=3. Will obfuscate any personal info.
PBComputer - 7 years ago
I can get an example tomorrow morning.
PBComputer - 7 years ago
I have just submitted the file it's in a zip
Lawrence Abrams - 7 years ago
Thanks
ChrisJ_NZ - 7 years ago
One of my customers was hit with this today, it came in the form of a Word attachment for a "Receipt". I'm just going to upload it for you
aw2001 - 7 years ago
Any known decryption tools for this variant?
Rajko - 7 years ago
Is there any solution about .odin extension? Need help please. Send me some info on sekulicbn1@gmail.com
Lawrence Abrams - 7 years ago
No solution at this time.
sahmed6032 - 7 years ago
Hi, it will be great if anybody send me the sample to sahmed6032@yahoo.com
Thank you.
anandkumarngn - 7 years ago
Hi Grinler , Is there any solution about .odin extension? Need help please. Send me some info on anandkumarngn@gmail.com and I have affected files and I will attach with this forum
Lawrence Abrams - 7 years ago
Unfortunately, no solution at this time.
alofun - 7 years ago
I found articles about ransomware odin http://www.cuudulieuocung.org/2016/10/virus-doi-ten-file-thanh-odin-ransomware.html
Else89 - 7 years ago
We had an attack today by this, it seemed to spread via a sites internal network but anyone connected to a shared drive was fine. we restored to a back up and we have isolated the pc's infected. it came from a gmail.com email address' all the subjects are "receipt ##-####" we are getting 5-10 every few seconds that is now being stopped by our filter. may be worth people changing filter settings
anandkumarngn - 7 years ago
We too researching about this .ODIN issue , so please give some idea to fix this crypto locker issues guys.
Lagarb - 7 years ago
Wondering if there's an update for this yet, I keep getting clients calling me with this Odin ransomware. Cheers!
tpapple - 7 years ago
I found the odin ransomware not spread by the spam email in china.. have anybody got the same situation?