To further show how ransomware is such a pile of crap, a new version of Locky has been released that appends the .shit extension on encrypted files. Like previous variants, this ransomware is installed using a DLL that is executed by Rundll32.exe. Once executed, it will encrypt targeted file types and append the .shit extension to the name of encrypted files.
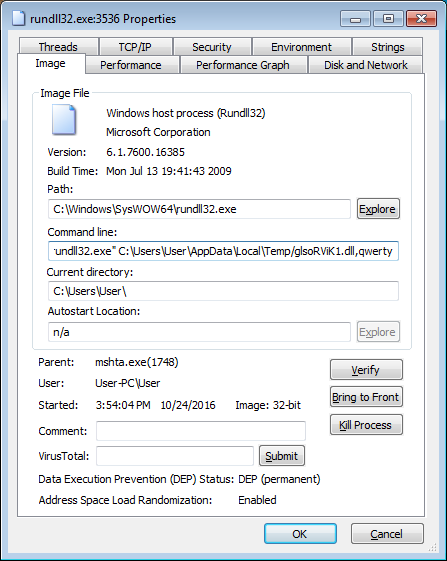
This variant is currently being distributed through SPAM emails with a subject line of Receipt ###-###. According to MalwareHunterTeam, the attachments in the Locky SPAM emails will contain attachments that are HTA, JS, or WSF files that when executed will download an encrypted DLL installer, decrypt it on the victim's computer, and then execute it as seen in the image above.
Once the ransomware is executed, it will target over 380 file extension and encrypt them using AES encryption.
The targeted extensions are:
.yuv,.ycbcra,.xis,.wpd,.tex,.sxg,.stx,.srw,.srf,.sqlitedb,.sqlite3,.sqlite,.sdf,.sda,.s3db,.rwz,.rwl,.rdb,.rat,.raf,.qby,.qbx,.qbw,.qbr,.qba,.psafe3,.plc,.plus_muhd,.pdd,.oth,.orf,.odm,.odf,.nyf,.nxl,.nwb,.nrw,.nop,.nef,.ndd,.myd,.mrw,.moneywell,.mny,.mmw,.mfw,.mef,.mdc,.lua,.kpdx,.kdc,.kdbx,.jpe,.incpas,.iiq,.ibz,.ibank,.hbk,.gry,.grey,.gray,.fhd,.ffd,.exf,.erf,.erbsql,.eml,.dxg,.drf,.dng,.dgc,.des,.der,.ddrw,.ddoc,.dcs,.db_journal,.csl,.csh,.crw,.craw,.cib,.cdrw,.cdr6,.cdr5,.cdr4,.cdr3,.bpw,.bgt,.bdb,.bay,.bank,.backupdb,.backup,.back,.awg,.apj,.ait,.agdl,.ads,.adb,.acr,.ach,.accdt,.accdr,.accde,.vmxf,.vmsd,.vhdx,.vhd,.vbox,.stm,.rvt,.qcow,.qed,.pif,.pdb,.pab,.ost,.ogg,.nvram,.ndf,.m2ts,.log,.hpp,.hdd,.groups,.flvv,.edb,.dit,.dat,.cmt,.bin,.aiff,.xlk,.wad,.tlg,.say,.sas7bdat,.qbm,.qbb,.ptx,.pfx,.pef,.pat,.oil,.odc,.nsh,.nsg,.nsf,.nsd,.mos,.indd,.iif,.fpx,.fff,.fdb,.dtd,.design,.ddd,.dcr,.dac,.cdx,.cdf,.blend,.bkp,.adp,.act,.xlr,.xlam,.xla,.wps,.tga,.pspimage,.pct,.pcd,.fxg,.flac,.eps,.dxb,.drw,.dot,.cpi,.cls,.cdr,.arw,.aac,.thm,.srt,.save,.safe,.pwm,.pages,.obj,.mlb,.mbx,.lit,.laccdb,.kwm,.idx,.html,.flf,.dxf,.dwg,.dds,.csv,.css,.config,.cfg,.cer,.asx,.aspx,.aoi,.accdb,.7zip,.xls,.wab,.rtf,.prf,.ppt,.oab,.msg,.mapimail,.jnt,.doc,.dbx,.contact,.mid,.wma,.flv,.mkv,.mov,.avi,.asf,.mpeg,.vob,.mpg,.wmv,.fla,.swf,.wav,.qcow2,.vdi,.vmdk,.vmx,.wallet,.upk,.sav,.ltx,.litesql,.litemod,.lbf,.iwi,.forge,.das,.d3dbsp,.bsa,.bik,.asset,.apk,.gpg,.aes,.ARC,.PAQ,.tar.bz2,.tbk,.bak,.tar,.tgz,.rar,.zip,.djv,.djvu,.svg,.bmp,.png,.gif,.raw,.cgm,.jpeg,.jpg,.tif,.tiff,.NEF,.psd,.cmd,.bat,.class,.jar,.java,.asp,.brd,.sch,.dch,.dip,.vbs,.asm,.pas,.cpp,.php,.ldf,.mdf,.ibd,.MYI,.MYD,.frm,.odb,.dbf,.mdb,.sql,.SQLITEDB,.SQLITE3,.pst,.onetoc2,.asc,.lay6,.lay,.ms11 (Security copy),.sldm,.sldx,.ppsm,.ppsx,.ppam,.docb,.mml,.sxm,.otg,.odg,.uop,.potx,.potm,.pptx,.pptm,.std,.sxd,.pot,.pps,.sti,.sxi,.otp,.odp,.wks,.xltx,.xltm,.xlsx,.xlsm,.xlsb,.slk,.xlw,.xlt,.xlm,.xlc,.dif,.stc,.sxc,.ots,.ods,.hwp,.dotm,.dotx,.docm,.docx,.DOT,.max,.xml,.txt,.CSV,.uot,.RTF,.pdf,.XLS,.PPT,.stw,.sxw,.ott,.odt,.DOC,.pem,.csr,.crt,.key
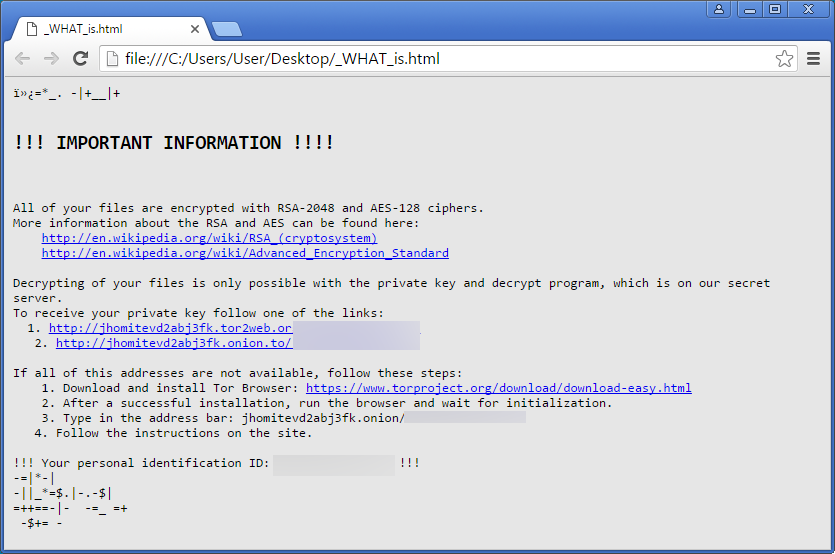
When it has finished encrypting a computer it will display ransom notes with payment instructions. These ransom notes have new names with this version and are named _WHAT_is.html, _[2_digit_number]_WHAT_is.html, and _WHAT_is.bmp.
This configuration for this version as shown by LockyDump is:
Verbose: 0
Loaded: 10000000
The file is a DLL
Read 312 bytes
The headers are different
-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-
Exported name:
setupapi.dll
Exports:
qwerty
-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-
affilID: 3
Seed: 74311
Delay: 63
Persist Svchost: 0
Persist Registry: 0
Ignore Russian Machines: 1
CallbackPath: /linuxsucks.php
C2Servers: 109.234.35.215,91.200.14.124,185.10
RsaKeyID: 542
RsaKeySizeBytes: 114
Key Alg: A400
Key: RSA1
Key Bits: 2048
Key Exponent: 10001
Key Bytes:
C3 3F 68 D4 B1 C9 A6 2F
4D 33 A2 92 E2 99 3C AE
BC 6D 3F 3E D0 EE 9F 51
D8 33 94 2D A3 39 77 18
5A AD E7 53 0E 01 57 EE
94 EE 4A 2C 47 3B 4F 59
0F 5B EA 09 C0 95 EA 64
F2 6E BD EC A2 99 61 E4
D7 80 78 ED F4 73 86 B3
AB 30 38 81 E1 DC FC 41
68 84 F1 E8 9D DE 1D 6F
21 C9 1C 8C 2D B4 0E B8
AF E6 50 36 D7 B2 AB 20
32 9A EC 86 13 61 19 D2
F5 C2 3A E3 4C 96 4A 46
49 99 EF FC 46 BC 6E 07
12 BD 6C 66 70 5B F2 DA
7C 8F 39 77 62 12 C3 D3
1A 93 91 76 0B EB 96 9E
31 DE C0 4B EF BF DC 80
DD C7 17 5E 88 B7 CE 2F
79 43 B2 B9 8B A7 E4 FA
6D C4 42 3E E5 BD 26 6F
C1 34 D5 E1 66 30 65 83
84 DD 31 2F 03 88 42 2A
53 76 1C A7 DD EB 20 E5
F6 90 4C 45 8A 83 A3 FD
A0 96 F3 A8 F4 78 E4 74
48 1D A7 87 C8 51 9F C7
98 3F 1F 7B 69 BA B4 2F
98 EC 3E 30 79 4E 45 8A
D2 68 49 66 56 6F D5 BA
Unfortunately, like previous versions this variant cannot be decrypted for free.


Comments
Dirk41 - 7 years ago
Thanks for the news .
And just out of curiosity , does the decrypt exist paying ?
Lawrence Abrams - 7 years ago
Past variants would decrypt if you paid, though we do not advise it if at all possible.
alpotero - 7 years ago
My customer just got infected by this locky ransomware.. Will check on it tomorrow and see what I can find out
logicslayer - 7 years ago
Yep, first thing I dealt with Monday morning.
Demonslay335 - 7 years ago
New variant with the extension ".thor" has also been officially spotted.
andrew867 - 7 years ago
I had to deal with this same malware yesterday afternoon. The email had the subject containing "complaint letter" with a zip file attached. I'll attempt to get a copy of the zip to see what it contained.
Edit: This is the email contents:
---START---
Dear ,
Client sent a complaint letter regarding the data file you provided.
The letter is attached.
Please review his concerns carefully and reply him as soon as possible.
Best regards,
Frieda George
---END---
I have saved a copy of the zip, if anyone would like to analyze it please reply to this comment.
Edit 2: ZIP file is named "saved_letter_18aa46f40.zip" and contains a obfuscated .js file.
GT500 - 7 years ago
Funny, I got a Locky dropper in a spam e-mail yesterday as well. It's always great when the malware authors send their stuff to me.
jkx - 7 years ago
one of my network computers got this .SHIT virus. All i want to know a way to recover the data files mainly word and excel. the file size is the same as before. its just that they are excrypted. i have tried using data recovery tools to recover deleted data but no luck. anybody got any suggestion. thanks
Lawrence Abrams - 7 years ago
Unfortunately, there is no way to restore without a backup or paying the ransom.
HVC-Logan - 7 years ago
Thank you for the information. Your site is phenomenal. I have donated several times.
A client opened an email attachment and all of his data files became encrypted with the Thor extension. The Ransom Cost is 3.5 Bitcoins. Has anyone had experience they can share regarding this new variant and will a decryption key be presented upon payment?
Lawrence Abrams - 7 years ago
Thanks! This is just Locky, so whatever their past history is goes for this new version. As much as I do not want you to pay, they do have a record of providing the decryption key after payment.
Prashat - 7 years ago
My PC got infected by this ransomware with .a9e3 extension, any idea how to deal with it? I have removed the virus using AVG paid antivirus.
mousegreat - 7 years ago
Allo everyone i have a friend who have this sh#t infection in his pc does anyone know if there is any decryptor available ? please let me know if their is any progress in resolving this matter thank you!