
2016 is almost over and it definitely taught us one thing; Ransomware is here to stay and it's only going to get worse. With even the smaller ransomware developers earning a lot of money, the ransomware explosion is going to continue with more innovative techniques used in 2017.
Therefore, it is important that every computer user, whether you are only using a computer at home or in the enterprise, needs to understand how to prevent, harden, and protect their computer from ransomware. To help you, I have put together the most important steps a computer user needs to do in order to not only protect themselves from ransomware, but other malware that use similar infection methods.
I know this article is long, but computer security is something that takes effort. If you want to protect your computer and your assets, then I strongly suggest you print this article and read it as time permits.
Make sure you are doing backups!
Backup, Backup, BACKUP! This absolutely the most important task that needs to done to protect their data from being encrypted. The reality is that if you have up-to-date backups, ransomware becomes more of a nuisance than a threat. This is because you can simply remove the infection and then restore your data from backups.
Unfortunately, simply adding an extra hard drive to a computer and backing up to it once in a while is not enough. This is because ransomware will target and encrypt all the drives on a computer, including mapped network drives, and sometimes even target unmapped network shares. This means that backups on local and network storage could be encrypted as well.
Therefore, I strongly suggest that users invest in a good cloud backup strategy with versioning and a long restore window. You need the long restore window in the event that recent cloud backups contain the encrypted files and you need to restore from older versions. Since most cloud backups do not map to a computer as a drive letter, the backups are safe from being encrypted and can easily be used to restore files.
If you do not wish to use a cloud backup, but want to rely on local storage, then make sure to either disconnect the storage devices after backups or make the backup computer isolated and inaccessible over file sharing.
Install a antivirus or antimalware solution that has ransomware behavior detections.
Make sure you have a reliable anti-virus or anti-malware solution installed on the computer. Cybercrime is only increasing and every computer needs good protection on it. I also suggest that you use a product that contains good behavioral detection in order to detect when ransomware infection, even brand new ones, are trying to encrypt your data and then stop it.
Programs such as Emsisoft Anti-Malware, Malwarebytes, HitmanPro.Alert, and ESET are my personal choice. You can also try a good and light-weight ransomware protection program called RansomFree.
Always install operating system updates
As many ransomware infections are installed via scripts called exploit kits that target vulnerabilities in operating systems, if you receive a prompt from your OS that new updates are ready to install, then you should immediately install them. Many of these updates are security updates that protect your computer from vulnerabilities that could literally allow an attacker to execute whatever command they want on your computer.
Microsoft releases security updates on Patch Tuesday, which is the second Tuesday of every month, so be prepared to install the updates and reboot your computer on that day.
Other operating systems, such as Apple and Linux will release security as they are ready. Therefore, always keep an eye out for notifications and install the updates as they become available.
Keep programs on your computer updated
Just like operating system vulnerabilities, exploit kits also target vulnerabilities in commonly installed programs on your computer such as Java, Adobe Flash Player, Adobe Reader, and others. Therefore it is imperative that you keep these programs updated as well.
An easy to use program that can scan a Windows computer for outdated programs is Flexera Personal Software Inspector. This program will monitor your installed apps and alert you when updates are available.
For Macs, you can use MacUpdate Desktop to scan for outdated non-apple programs. This app costs $20 per 6 months, but does come with a free limited trial.
Make sure your SPAM filters are working
One of the largest distribution methods for ransomware is through SPAM emails that pretend to be shipping notices, resumes, bills, or tickets from government agencies. If you are using a web mail vendor like Gmail, Outlook, or Yahoo, then many of these types of SPAM emails will be filtered out for you.
Unfortunately, if you are not using a service that has good SPAM filtering, then these types of emails may sneak through.
Enable the viewing of Extensions
By default, Windows and macOS does not show the extensions of a file when you are viewing a folder. This makes it easy for malware distributors to trick a user into thinking a executable file is actually a more familiar Word, Excel, or a PDF document A victim will open this file expecting it to contain data, but in reality they just ran a program that installs the malware. You can see an example of a program disguised as a PDF below with the showing of extensions enabled and disabled.
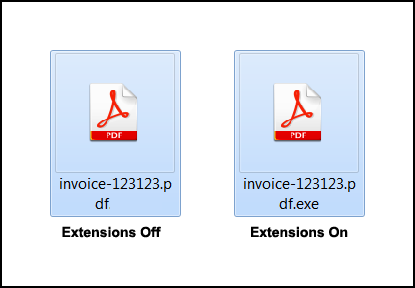
I suggest that everyone immediately enable the viewing of file extensions to make it harder for malware developers to trick you into launching their programs. To learn how to enable extensions, you can follow the steps in these tutorials based on your OS:
How to show File Extensions in Windows
How to show filename extensions on a Mac
Do not open attachments without confirming that someone actually sent it to you
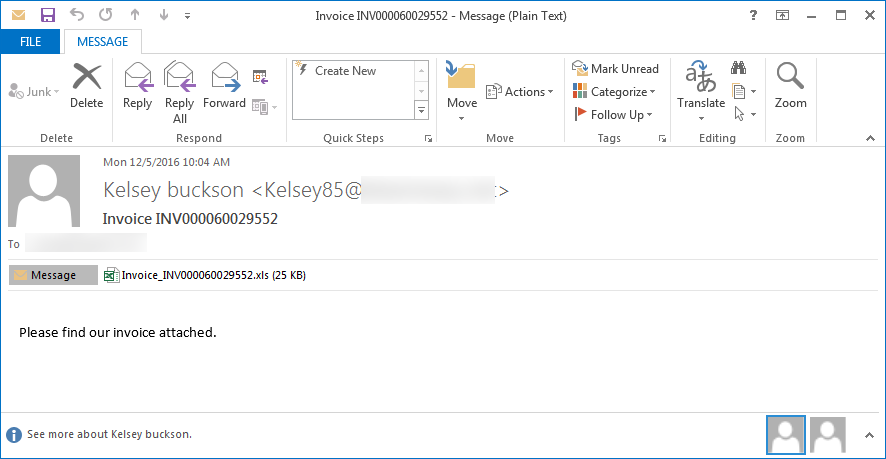
When ransomware is distributed via SPAM, in many cases the downloader or actual infection is attached as an attachment. If you receive an attachment and are unsure why it was sent or who it may have come from, do not open it without first confirming with the person that they actually sent it or by scanning it with VirusTotal. An example ransomware attachment can be seen below.
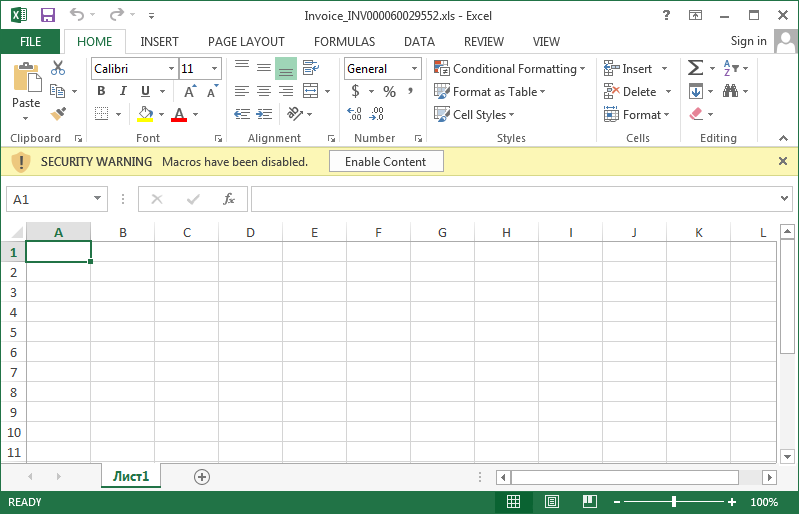
If you do make the mistake of opening an unknown attachment and see a message that you should click a button to enable macros or enable content, as shown below, DO NOT DO IT as this will just download and install the ransomware.
Be careful of what you download from the Internet
Free downloads from the Internet may also come with a hidden ransomware surprise. If they weren't criminal enough already, it has been discovered that some adware bundles are now bundling ransomware. When downloading programs it is important that you only download from sites that you trust and always read the license agreements.
Rename vssadmin in Windows
Shadow Volume Copies are used by Windows to automatically store backups, or previous versions, of files on a computer. These backups can then be used to restore data that was changed or deleted.
Ransomware devs know about this too, so many ransomware infections will execute the vssadmin.exe command in order to delete all shadow volume copies on a computer so that they cannot be used to restore encrypted files.
Unless you have software that relies on vssadmin, I strongly suggest you read this article on how to rename it without losing functionality: Why Everyone Should disable VSSAdmin.exe Now!
Disable Windows Script Host
Many ransomware infections are installed via attachments that are script files coded in Jscript or VBS. Unless you are normally executing Jscript or VBS files, and you would know if you are, then I suggest that you disable the ability to launch these types of scripts in Windows.
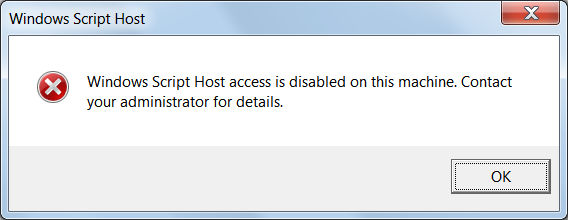
This article from Microsoft explains how to disable the Windows Script Host: Disabling Windows Script Host. Once the scripting host is disabled, if a script is launched you will see a message like the following.
Disable Windows PowerShell
Just like Windows scripting, the Windows PowerShell is also used to install ransomware or even encrypt files. If you are not using PowerShell on your computer, you can disable the execution of PowerShell (ps1) scripts from running by entering this command in a Windows Elevated Command Prompt.
powershell Set-ExecutionPolicy -ExecutionPolicy Restricted
If it was set properly, when you execute a PowerShell script, you will see a message stating that PowerShell scripts have been disabled.
Note: As PowerShell becomes more and more popular, disabling the execution of PowerShell scripts could cause possible issues with legitimate programs. If you find that the execution of PowerShell scripts is necessary, you can change the Set-ExecutionPolicy to another level as described here.
Use strong passwords
Make sure you use strong passwords to protect your computer from unauthorized access. The goal is to make it hard for attackers, so do not use an easy password like 12345 and instead use a hard one like 1$!2M849dy1%.
This is because there are some ransomware infections that are installed by attackers logging into Remote Desktop connections that are secured with weak passwords, which leads us to my next suggestion...
If you do not need Remote Desktop, disable it, otherwise change the port!
If you are not using Remote Desktop, then there is absolutely no reason to keep it enabled.
If you are using it, then you should change the port to something other then the default port of 3389. To learn how to change the port used by Remote Desktop, you can read this tutorial: How to change the Terminal Services or Remote Desktop Port
As most attackers use scripts or scanners to search for open Remote Desktop computers on the default TCP port of 3389, by changing the port you have made your computer invisible to these tools.
Setup Software Restriction Policies in Windows
Software Restriction Policies is a method that allows you to create various policies that restrict what folders an executable can be started from. For more information on how to manually setup Software Restriction Policies, you can see this part of the Locky Guide.
For those who want to let a program do all the work for them, you can use the free CryptoPrevent program, which sets the policies for you. There is a premium version that offers a few extra benefits. In full disclosure, BleepingComputer is an affiliate of FoolishIT and earns a commission from the sale of their premium versions.
Create a Application White List Policy in Windows
This last one is not for the faint of heart and can take quite a bit of tweaking to get it to work. A Software White List Policy is when you configure Windows to only allow programs to execute that you specify. This prevent any unknown programs from running and essentially locks your computer down completely from allowing an unauthorized program to run.
The problem, though, is that this can take quite a bit of work to get setup properly. For those who want to give it a try, we have a White List guide here: How to create an Application Whitelist Policy in Windows
Conclusion
Though it may feel like there are a lot of steps, most of them require you to just change your computing habits or perform a task once and not worry about it again. If you follow these steps, not only will you be protected from ransomware, but you will also be protected from almost all other malware.
Updates:
12/23/16: Updated to include macOS related information and added versioning requirement for cloud backups.


Comments
Viper_Security - 7 years ago
You should the title to "............." on a Windows computer.
Not everyone uses W1nD0z3 lol.
andika - 7 years ago
''because ransomware will target and encrypt all the drives on a computer''
you are wrong. in my case only 3 out of 7 disks in the same computer were infected.
Sintharius - 7 years ago
Probably because it did not have time to encrypt everything - given enough time most ransomware will encrypt everything they can reach, including network drives.
Lawrence Abrams - 7 years ago
You got lucky. They try and target all local disks.
tomo.testira - 7 years ago
I'd like to emphasize that cloud backups, although they don't map a drive letter, indeed *ARE* affected with ransomware. How? Ransomware encrypts your local files and deletes old ones. Sync program simply syncs that state with cloud backup. All files on cloud are encrypted, too, and old ones deleted.
Only clouds which have versioning and large trash-can can save you.
Best
Tomo
stuartmiller - 7 years ago
My computer is struck with some unknown virus and I believe it’s because I downloaded so many games from multiple websites last days. The blog is simply amazing.
Ravendarke - 7 years ago
Lost two years of work as 2d/3d artist few days ago to cerber, sadly all backups were connected in same way and ransomware had enough time.
pnamajck - 7 years ago
ravendarke … i feel for you. i'd suggest retaining those encrypted files (don't pay). eventually, the key might be found … thereby allowing you to decrypt the files.
Ravendarke - 7 years ago
yeah, I´ve unplugged main HDD (one that was encrypted first) and ordered replacement. I will give it two years then I will format and use it.
Lawrence Abrams - 7 years ago
Updated the guide to include information for Mac users and versioning to the cloud backup info.
DyingCrow - 7 years ago
If local backups is the preferred method:
If you have a hard drive as backup media, unplug the power cable when you're done. Really no reason to leave it on and vulnerable to many things. Same for external drives, but that's common sense.
To the same drive:
-Have your files organized in a single folder to make it easier to backup..
-Compress the folder with the files to whatever format you prefer (7zip, zip, rar, etc). Password protect it, because why not.
-Change the extension to something conspicuous like .exe (or something random), and move it to a location where .exe are expected to be, like C:\Program Files\*. There is no telling if .exe in Documents, Downloads, Desktop or whatever will be encrypted in the future after everything else.
-If you ever need to access the backup, change the extension back to the original.
Can also:
-Clutter bloat backups so they all have different sizes. I'd definitely look into a folder with a bunch of random files with very similar sizes, no matter the extension or lack of.
pnamajck - 7 years ago
" Make sure you are doing backups! "
" The only problem with a backup strategy using local storage is if that computer becomes infected, the backups are gone as well. "
along similar trajectory … just keep in mind, the files you're backing up may seem innocuous enough … but, may also contain a ransomware executable. doesn't matter if this backup is local or global. or, along same notion, might become catalyst for ransomware. a simple image you saved to your drive (and backed up) may contain a tiny script … which is all that's needed to manifest another future attack … should you decide to replace infected files or even reinstalling your whole system.
lawrence … thanks for the valuable article … couldn't be at better time.
With Wings4 - 7 years ago
Enable UAC (Prompt), Enable EMET (Max Security), Use Google Chrome (Token stripping, separate processes etc.). DISABLE volume shadow copies (I have found malware hiding here too often). Remove un-needed software (Java, Adobe Reader / Flash - use the embedded browser version). Disable shared folders / printers. Ensure the firewall is enabled. Disable unused services (Remote Registry etc - this is more difficult).
Back during the days of DiamondCS (processguard) they had an app that whitelisted applications by hash, and prevented code injection / sideloading, hooking, and the like.
Windows App Locker is useless as it 'secures' things by filename, and path, and doesn't give a crap about sideloaded dlls, or process injection, or if the (non-existent) hash is valid. I don't think it even verifies signatures for OS binaries.
Ironically if you are using Windows XP, ProcessGuard should be pretty effective. It would be funny to compare that setup to a vanilla Windows 8 install.
Demonslay335 - 7 years ago
I wouldn't fully disable shadow copies, they are useful for recovering data and registry settings. When we do malware cleanup on a machine, we do delete old restore points, as this is what the malware can hide in - but I would not turn off the whole feature itself.
DirkYottabyte - 7 years ago
backups backups backups....my Windows command script to backup to a USB stick or SD card which I do not leave mounted all the time so it does not become a target of ransomeware.
- first, install rsync
- use this script (edit the particulars to suit your environment), save it as a .cmd file
-------------------- start backup script --------------------
@echo off
REM 1. Mount your USB stick or SD card (get volume UID from 'mountvol' command)::
mountvol F: \\?\Volume{1d8b5a6d-cba2-11e6-829a-40167e82541c}\
REM 2. rsync command to sync d:\mydox directory to USB stick F:\bkup directory:
"C:\cygwin64\bin\rsync.exe" -czav /cygdrive/d/mydox/ /cygdrive/f/bkup/
REM (optional) Create a shadow copy of D:
wmic shadowcopy call create Volume='D:\'
REM (Optional) delete the oldest shadow copy of D:
REM vssadmin Delete Shadows /For=D: /Oldest
REM 3. Unmount the USB stick F: drive as we don't want it mounted all the time
mountvol F: /p
-------------------- end backup script --------------------
Enjoy! ;)
Ryanbekabe - 7 years ago
For Ransomware with .dll type, no more macro/widows script disable, just check it bad or good macro/script process.
Anti Ransomware DaK v1 - Detect and Kill Ransomware Process.
#ransomware
#killer v1, 28 Des 2016.
http://bekabe.blogspot.co.id/2016/12/anti-ransomware-dak-v1-detect-and-kill.html
backfolder - 6 years ago
Thanks so much Ryan for helping people!!!
Regards.
Cetus35 - 7 years ago
Excellent article. Thanks for the tips to keep folks computers from being just complete sitting ducks.
I have a question, however, about the last sentence in the "Make sure you are doing backups!" section at the top.
Namely, "The only problem with a backup strategy using local storage [versus cloud] is if that computer becomes infected, the backups are gone as well."
Although directly above that it advises to disconnect the drive once the backup is made.
When I back up to my external, USB-connected, hard drive I then turn it off and disconnect it, as advised.
How then will ransomware infect the drive, as the last sentence mentioned states?
Surely not through teleportation of the malware from my system to the disconnected drive :)
.
.
Lawrence Abrams - 7 years ago
Your right. That last sentence was out of place and did not make sense. Removed it.
johny85 - 6 years ago
I had so many problems with ransomware, mostly because I didn't know how to optimize my computer. Buddy told me that he had the same kind of problems, he got Impedio Security. Currently I am trying it and I'm so relieved that finally something so good has been made. The most important thing that could persuade you to try it, is that the software make instant backups. You can have terabytes of data but Impedio make it fast and save your time
shakermoss - 4 years ago
All great points! I would recommend 2 things i think are the most valuable information vs cloud and local. First: USE DLT tapes and drives. Switch out each tape daily and always do full backup ( i know this is not recommended as you will obviously restore the issue) but you will get all data you need and can parse through that. Second: When you send you differential, daily, full etc.. to the cloud, your restore time will be very much laggy. For home stuff ok, but business, NO WAY!. See most all cloud services backup your data to multiple servers and is encrypted! I waited 1 week to fully restore 200 gig of data.