
A ransomware that has been distributed since the summer of 2018 has started to pick up steam in the latest variant. This new variant is currently being called Zorro Ransomware, but has also been called Aurora Ransomware in the past.
It is not currently known how this ransomware is distributed, but there are indications it may be installed by hacking into computers running Remote Desktop Services and that are exposed to the Internet. The attackers will brute force the password for RDP accounts in order to gain access to the computer and install the ransomware.
The good news is that Michael Gillespie and Francesco Muroni have discovered a way to decrypt this ransomware for free. If you are infected with this ransomware, please post a comment in this article or in the Aurora Help & Support topic for help.
Over $12,000 in payments made
As this ransomware utilizes the same bitcoin address for all of its victims, it makes it easy to track how many payments have been made.
The current Zorro Ransomware variant is using the bitcoin address 18sj1xr86c3YHK44Mj2AXAycEsT2QLUFac, which currently has 105 transactions since the end of September.
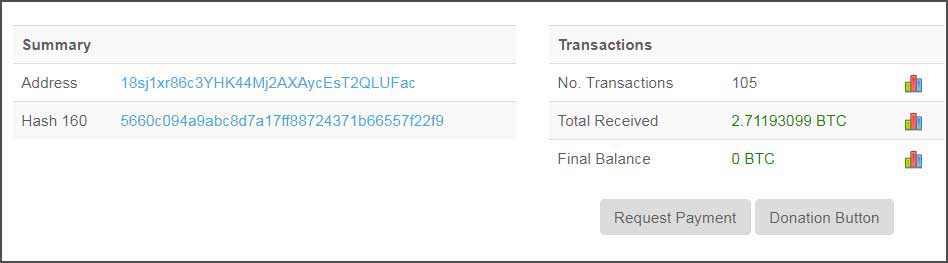
In total, this address has received 2.7 bitcoins, which equals over $12,000 at current bitcoin prices.
How the Aurora / Zorro Ransomware encrypts a computer
When installed, the ransomware will connect to a Command and Control server to receive data and to receive an encryption key to be used to encrypt the victim's files.
It will then connect to http://www.geoplugin.net/php.gp to determine what country the victim is residing in based on their IP address. Based on the string "Russia" found in the executable, it may not encrypt victims who are located in that country.
The ransomware will now proceed to scan a computer for targeted file types, and if a matching file is detected, will encrypt it. The currently targeted file extensions are:
1CD, doc, docx, xls, xlsx, ppt, pptx, pst, ost, msg, eml, vsd, vsdx, txt, csv, rtf, 123, wks, wk1, pdf, dwg, onetoc2, snt, jpeg, jpg, docb, docm, dot, dotm, dotx, xlsm, xlsb, xlw, xlt, xlm, xlc, xltx, xltm, pptm, pot, pps, ppsm, ppsx, ppam, potx, potm, edb, hwp, 602, sxi, sti, sldx, sldm, vdi, vmdk, vmx, gpg, aes, ARC, PAQ, bz2, tbk, bak, tar, tgz, rar, zip, backup, iso, vcd, bmp, png, gif, raw, cgm, tif, tiff, nef, psd, svg, djvu, m4u, m3u, mid, wma, flv, 3g2, mkv, 3gp, mp4, mov, avi, asf, mpeg, vob, mpg, wmv, fla, swf, wav, mp3, class, jar, java, asp, php, jsp, brd, sch, dch, dip, vbs, ps1, bat, cmd, asm, pas, cpp, suo, sln, ldf, mdf, ibd, myi, myd, frm, odb, dbf, mdb, accdb, sql, sqlitedb, sqlite3, asc, lay6, lay, mml, sxm, otg, odg, uop, std, sxd, otp, odp, wb2, slk, dif, stc, sxc, ots, ods, 3dm, max, 3ds, uot, stw, sxw, ott, odt, pem, p12, csr, crt, key, pfx, der,
When encrypting a file it will currently append the .aurora extension to the encrypted file's name. For example, a file named test.jpg would be encrypted and renamed to test.jpg.aurora.
Previous variants of this ransomware have also utilized the .animus, .Aurora, .desu, and .ONI file extensions for encrypted files.
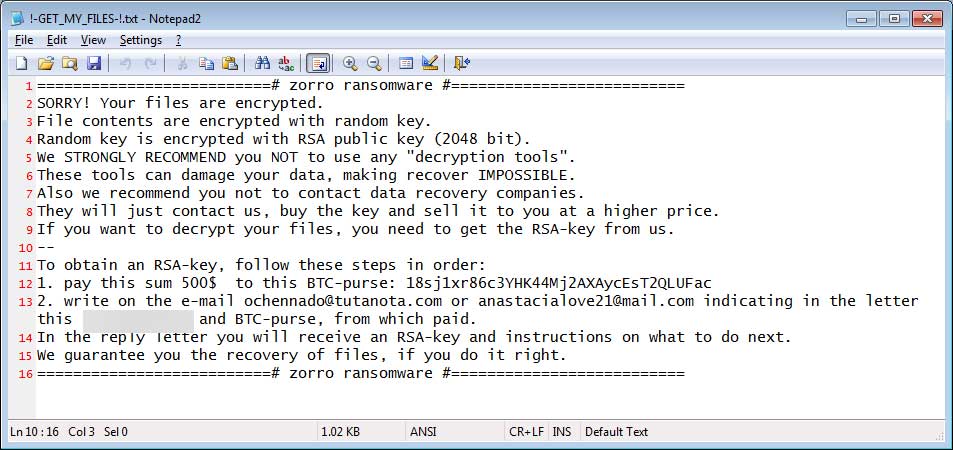
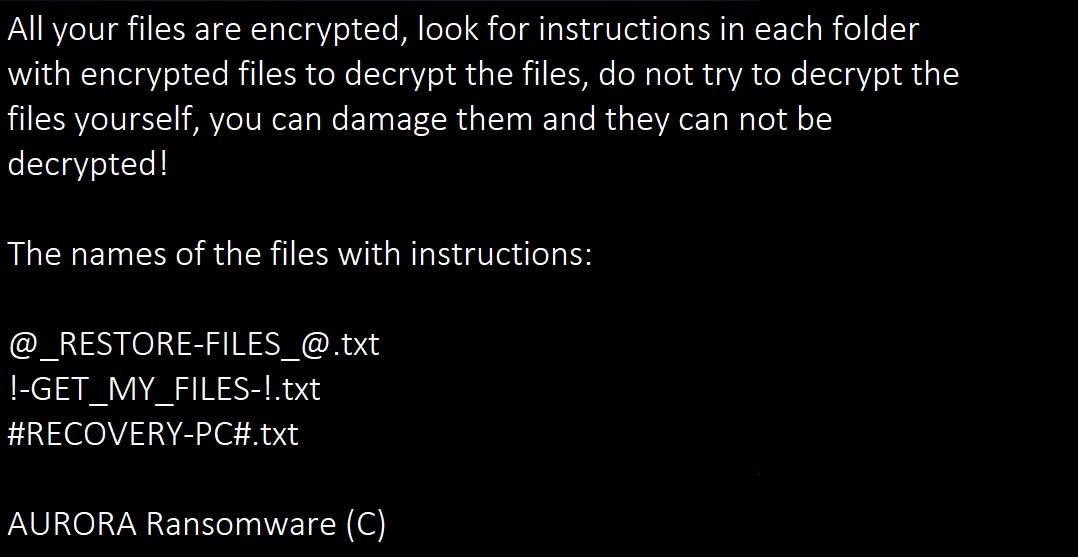
While encrypting files, the ransomware will also create ransom notes in each folder that it traverses. These ransom notes are named !-GET_MY_FILES-!.txt, #RECOVERY-PC#.txt, and @_RESTORE-FILES_@.txt and will contain instructions on how to pay the ransom. It will also contain an email address, which is currently oktropys@protonmail.com, that victim can use to contact the attacker after making payment.
Finally, the ransomware will create the %UserProfile%wall.i file, which is actually a jpg file, and set it as your desktop wallpaper. This image contains instructions on how to open the ransom notes.
As previously stated, this ransomware is decryptable. If you are infected, be sure to leave a comment here or in the Aurora Help & Support topic for help.
How to protect yourself from Aurora / Zorro Ransomware
In order to protect yourself from this ransomware, or from any variant, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
As this ransomware may be installed via hacked Remote Desktop services, it is very important to make sure RDP is locked down correctly. This includes making sure that no computers running remote desktop services are connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
It is also important to setup proper account lockout policies so that it makes it difficult for accounts to be brute forced over Remote Desktop Services.
For more detailed information, please see our guide on locking down Remote Desktop Services.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
- If you are using Remote Desktop Services, do not connect it directly to the Internet. Instead make it accessibly only via a VPN.
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
IOCs
Hash:
SHA256: e8e995787549117aacb30b3d4896c058a8bfc8d0aab312b726d34e6ab85d819d
Associated Files:
!-GET_MY_FILES-!.txt
#RECOVERY-PC#.txt
@_RESTORE-FILES_@.txt
%UserProfile%wall.i
Associated email addresses:
anastacialove21@mail.com
anonimus.mr@yahoo.com
big.fish@vfemail.net
enco@cock.email
enco@cock.email
hellstaff@india.com
j0ra@protonmail.com
ochennado@tutanota.com
oktropys@protonmail.com
UnlockAlexKingman@protonmail.com
Known encrypted file extensions:
.animus
.Aurora
.desu
.ONI
.aurora
Zorro / Aurora Ransom Note:
==========================# zorro ransomware #==========================
SORRY! Your files are encrypted.
File contents are encrypted with random key.
Random key is encrypted with RSA public key (2048 bit).
We STRONGLY RECOMMEND you NOT to use any "decryption tools".
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you need to get the RSA-key from us.
--
To obtain an RSA-key, follow these steps in order:
1. pay this sum 500$ to this BTC-purse: 18sj1xr86c3YHK44Mj2AXAycEsT2QLUFac
2. write on the e-mail ochennado@tutanota.com or anastacialove21@mail.com indicating in the letter this ID-[id] and BTC-purse, from which paid.
In the reply letter you will receive an RSA-key and instructions on what to do next.
We guarantee you the recovery of files, if you do it right.
==========================# zorro ransomware #==========================


Comments
Amigo-A - 5 years ago
Information for devs:
Zorro ransomware name already before taken
https://twitter.com/BleepinComputer/status/844538370323812353
https://id-ransomware.blogspot.com/2017/03/zorro-ransomware.html
Bullwinkle-J-Moose - 5 years ago
I notice it encrypts .ISO files...
How can it possibly encrypt my 50GB .ISO file when it it currently loaded in the Virtual ROM drive along with my backups and software ?
Lawrence Abrams - 5 years ago
Probably wouldn't be able to as the file is open. Any unmounted images, though, would be a different story.
Bullwinkle-J-Moose - 5 years ago
"Any unmounted images, though, would be a different story."
A different story if I were not using Shadow Mode (Google: Shadow Defender)
Even if I manually unmounted the ISO and let the malware reboot to begin the encryption process, Shadow Defender would wipe the malware before booting with the ISO once again loaded at boot-time
Windows 8.1 and 10 with Shadow Mode, Windows XP with Driveshield and Linux Live = Good Stuff !
backfolder - 5 years ago
I think that duplicate/copy your ISO, then rename with different extension, for example Whatever-name.MyISO should protect. When you need it, return the copy and rename again. Also you can hide the iso renamed or protect against write. This is for backup, not for working actively whit it. IMMO.
Warthog-Fan - 5 years ago
How can you tell if RDP is active on a computer?
JohnnyJammer - 5 years ago
Use wmic
wmic rdtoggle get allowtsconnections << If 1 means its enabled
or use the command sysdm.cpl, navigate to remote tab and see if its allowed mate.
Warthog-Fan - 5 years ago
Johnny,
Thanks.