New variants of Locky are being released at a rapid rate lately. Yesterday, we had a new variant that appends the .SH*T extension to encrypted files and today they switched to using the .THOR extension. Maybe Locky had its mouth washed out with soap for cursing? Regardless of the reasons for the switch, I am happy as I won't have posts with curse words all over the forums.
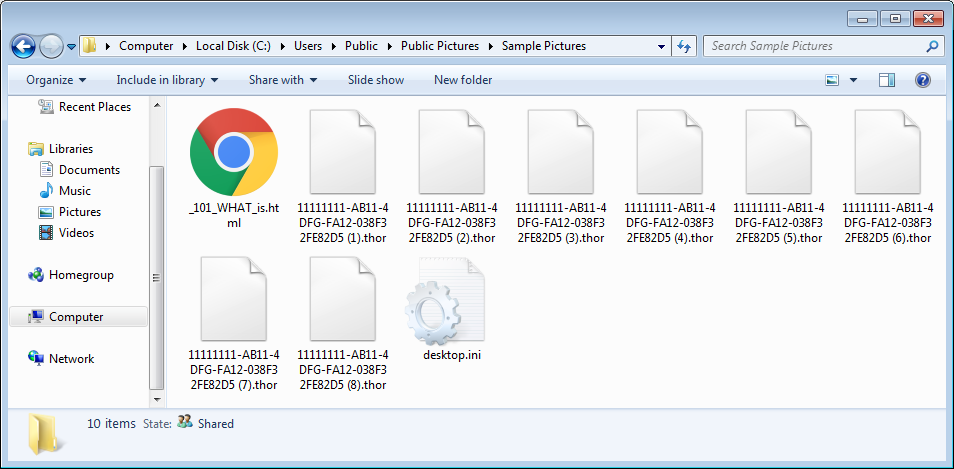
The Thor Locky variant being distributed via SPAM Campaigns
This new variant is currently being distributed through a variety of SPAM campaigns with VBS, JS, and other attachments. One SPAM campaign that I have seen has a subject line of Budget forecast and contains a ZIP attachment called budget_xls_[random_chars].zip.
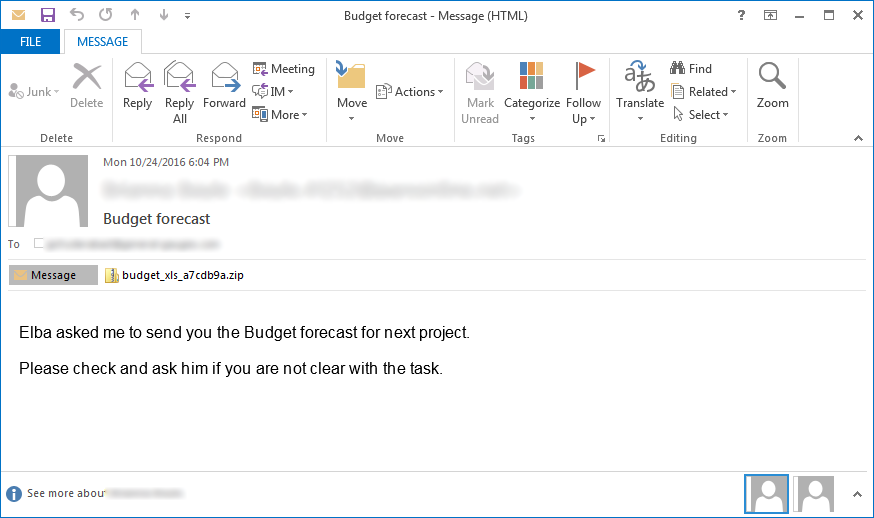
This budget_xls zip file will contain a VBS script with a name like budget A32aD85 xls.vbs as shown below.
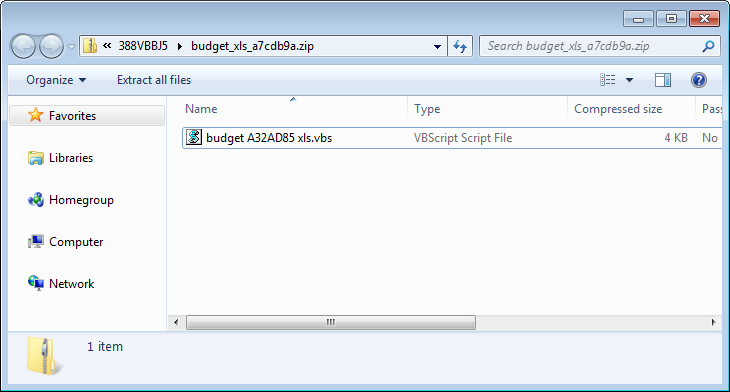
Locky continues to use a DLL Installer
When the Locky SPAM attachments are executed, they will download an encrypted DLL, decrypt it on the victim's computer, and then execute it using Rundll32.exe to encrypt a victim's files.
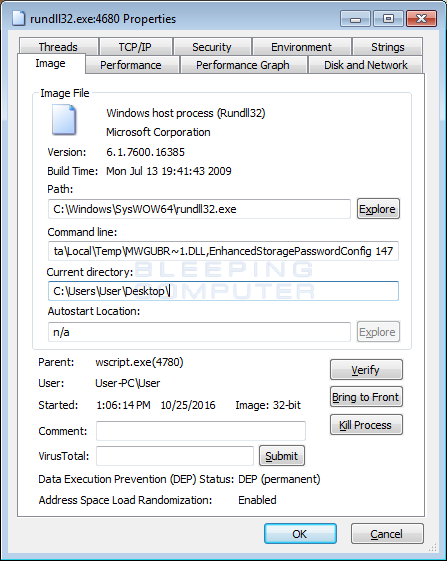
The DLLs are currently being executed with the following arguments:
C:\Windows\SysWOW64\rundll32.exe %Temp%\MWGUBR~1.dll,EnhancedStoragePasswordConfig 147
Once executed it will scan for targeted file types and encrypt them to a scrambled name with the .thor exension. For example, a file called accounting.xlsx could be renamed to 024BCD33-41D1-ACD3-3EEA-84083E322DFA.thor. The format for this naming scheme is first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].thor.
It is not possible to decrypt the Locky Ransomware Thor Variant
Unfortunately, there is still no realistic way to decrypt the Locky Ransomware regardless of the extension.
At this time the only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Locky does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.


Comments
alpotero - 7 years ago
I'm still waiting to know what locky author's real plan is...
Lawrence Abrams - 7 years ago
Ransomware domination?
logicslayer - 7 years ago
Dealt with this one first thing this morning.
kenhall5551 - 7 years ago
Another informative piece.. Thank you for supplying the nuts and bolts in assessing theses threats, Lawrence.
HVC-Logan - 7 years ago
Thank you for the information. Your site is phenomenal. I have donated several times.
A client opened an email attachment and all of his data files became encrypted with the Thor extension. The Ransom Cost is 3.5 Bitcoins. Has anyone had experience they can share regarding this new variant and will a decryption key be presented upon payment?
DodoIso - 7 years ago
If you sensor your posts dropping the I in SH*T, perhaps Google may not be able to redirect .SH*T victims to BleepingComputer.com. I just did a quick test, and it's a shame to see 3 days old web pages proposing solutions to this not-yet-decryptable ransomware.
Lawrence Abrams - 7 years ago
It is not censored here: https://www.bleepingcomputer.com/news/security/locky-ransomwares-new-shit-extension-shows-that-you-cant-polish-a-turd/. I just do not need it everywhere.
ClovisGermano - 7 years ago
My pc was infector by this virus, removed the virus, however how do I get back my files? are very important and I have no backup, will it takes to find the solution?
HVC-Logan - 7 years ago
I have a client whose data was encrypted with the Locky virus. xyzxyz.THOR extensions. We had to pay the ransom. I assume you have the Virus encryption page. After I paid the bitcoin ransom, a new "decrypter page" was presented to download the key and all of the data was decrypted. To add insult to injury the page said you should "make sure to backup your data!". That is good advice - AS LONG AS YOUR BACKUP is not powered on and connected to your computer!
HVC-Logan - 7 years ago
I have a client whose data was encrypted with the Locky virus. xyzxyz.THOR extensions. We had to pay the ransom. I assume you have the Virus encryption page. After I paid the bitcoin ransom, a new "decrypter page" was presented to download the key and all of the data was decrypted. To add insult to injury the page said you should "make sure to backup your data!". That is good advice - AS LONG AS YOUR BACKUP is not powered on and connected to your computer!
ClovisGermano - 7 years ago
Impossible to pay the ransom, they are asking 3.00 BTC, I do not need all the files just a few. Please someone help me.
HVC-Logan - 7 years ago
I wish I could. From what I have read in this and other forums, there is no current method known.
ClovisGermano - 7 years ago
Let me know, are solution? And how long it takes on average?
dkirkpat - 7 years ago
I just resolved this issue on a client PC. The previous versions process showed no previous versions. I used the Shadow Explorer. Here are the instructions: https://www.bleepingcomputer.com/tutorials/how-to-recover-files-and-folders-using-shadow-volume-copies/#shadow-explorer.
Worked like a charm.
Lawrence Abrams - 7 years ago
Glad you were lucky enough to be able to do this. This is exactly why everyone should attempt Shadow Volume Recovery before making a ransom payment!
eq2675 - 7 years ago
FYI, if you have renamed vssadmin.exe to something else, that file is needed to run Shadow Explorer.
ClovisGermano - 7 years ago
My case was more tense because nothing appears before the virus.
mdaemon - 7 years ago
As dkirkpat, I recovered all files from a client PC using Shadow Explorer. In this PC was installed Foolish CryptoPrevent v7.4.21, I gave a look at the "Alerts" but there were no ones, but maybe CryptoPrevent blocked the ransomware from delete the SVC